Scott Moss (1998)
Journal of Artificial Societies and Social Simulation vol. 1, no. 4, <https://www.jasss.org/1/4/1.html>
To cite articles published in the Journal of Artificial Societies and Social Simulation, please reference the above information and include paragraph numbers if necessary
Received: 20-Aug-98 Accepted: 10-Oct-98-98 Published: 15-Oct-98
![]()
 Abstract
Abstract
Where social simulation models are devised to support policy analysis, it is clearly a virtue if they are constructed in a way which is open to empirical inputs and, moreover, which makes clear the limits of those inputs. Although no effort in this direction was made on the basis of the experiments reported here, other work (e.g., Moss and Edmonds, 1997) has shown that appropriately specified models can be used to help domain experts identify and ameliorate inconsistencies between their own qualitative judgements and quantitative relationships drawn either from statistical data or physical theory. The models reported here were used to investigate a particular issue of the relationship between direct communication among a group of managers and the efficiency with which their common organizational task is carried out. The results were in line with the beliefs and experience of our informant.
While many tasks undertaken within organizations require cooperation among several of the units comprising the organization, there are important cases in which tasks are efficiently and accurately represented as requiring action by a single individual or unit within the organization. One such task is the identification and management of critical incidents. In such cases, it would always be possible to model the process at a sufficiently low level that the required co-operation among units or individuals must be represented explicitly. However, it is not always necessary to capture that level of detail in order to analyse the management issues involved. The issue of detail or, equivalently, reductionism is pragmatic: we choose the level of detail to elucidate the relationships of interest and to hide unwanted detail.
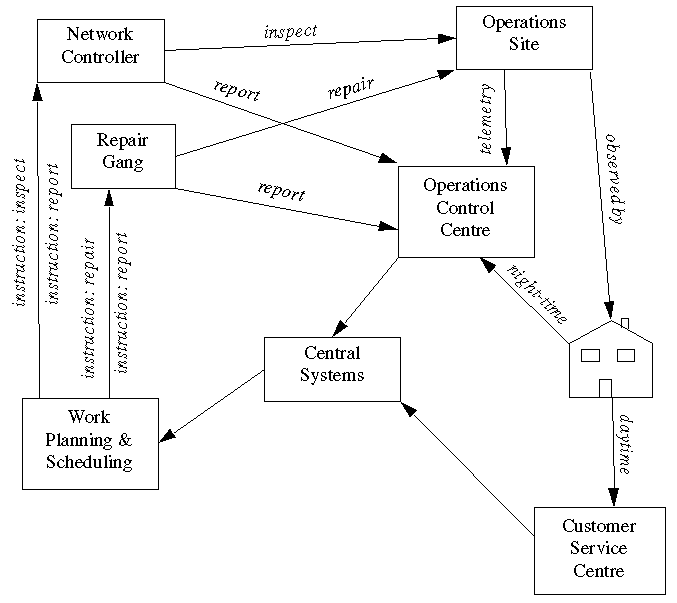 |
| Figure 1: Incident management organization |
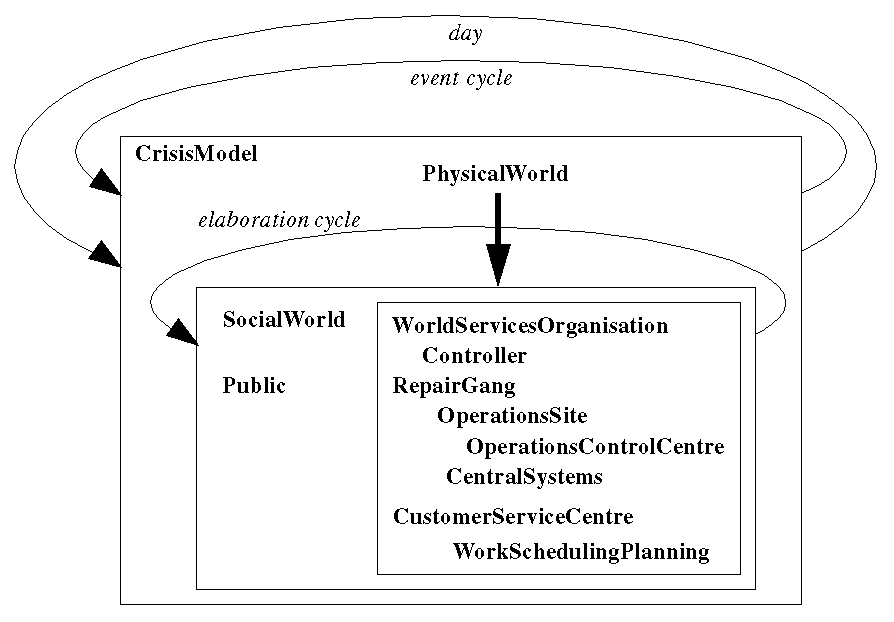 |
| Figure 2: Container structure of critical-incident model |
Table 1: Controllers' endorsements | |
| token | value |
|---|---|
| noEffect | -1 |
| newModel | 0 |
| reducedEvents | 1 |
| eliminatedAllEvents | 2 |
| reportedModel | 2 |
| specializedModel | 3 |
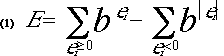
where b is an arbitrary number base not less than 1. Each term on the right of equation (1) is the decimal value of sum of the values of the endorsements in number base b. So if the number base is 2, then an endorsement of the third level of importance (such as specializedModel in Table 1) will be twice as important as an endorsement of the second level of importance (such as eliminatedAllEvents in Table 1). An endorsement of any level of importance will always be b times as important as an endorsement of the next lower level of importance.
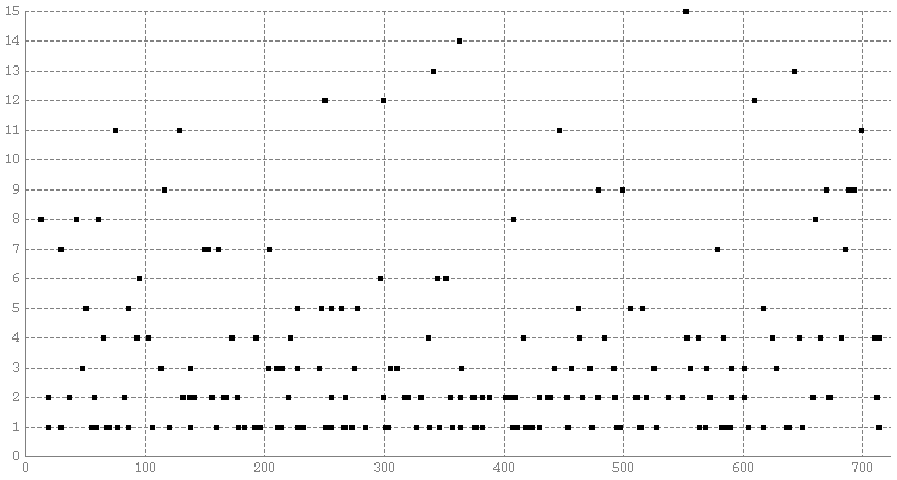 |
| Figure 3: Time pattern of the duration of critical incidents |
| Table 2: Percentage distributions of episode lengths (no model-sharing) | |||||
| Elapsed event cycles | 0<n<=2 | 2<n<=4 | 4<n<=6 | 6<n<=8 | 8<n |
|---|---|---|---|---|---|
| 0-53 | 68.75 | 6.25 | 12.5 | 12.5 | 0 |
| 54-107 | 58.82 | 17.65 | 11.76 | 0 | 11.76 |
| 108-161 | 60.00 | 13.33 | 13.33 | 6.67 | 6.67 |
| 162-215 | 40.00 | 20.00 | 26.67 | 13.33 | 0 |
| 216-269 | 25.00 | 25.00 | 25.00 | 16.67 | 8.33 |
| 270-323 | 22.22 | 22.22 | 33.33 | 11.11 | 11.11 |
| 324-377 | 61.11 | 22.22 | 16.67 | 0 | 0 |
| 378-431 | 53.33 | 26.67 | 13.33 | 6.67 | 0 |
| 432-485 | 64.71 | 17.65 | 5.88 | 0 | 11.76 |
| 486-539 | 43.75 | 25.00 | 25.00 | 6.25 | 0 |
| Avg overall | 49.77 | 19.60 | 18.35 | 7.32 | 4.95 |
| Std dev | 15.54 | 5.89 | 8.18 | 5.72 | 5.15 |
Table 3: Percentage distributions of episode lengths (with model-sharing) | |||||
| Elapsed event cycles | 0<n<=2 | 2<n<=4 | 4<n<=6 | 6<n<=8 | 8<n |
|---|---|---|---|---|---|
| 0-53 | 37.50 | 12.50 | 12.50 | 37.50 | 0 |
| 54-107 | 56.26 | 18.75 | 12.50 | 6.25 | 6.25 |
| 108-161 | 53.33 | 13.33 | 0 | 20.00 | 13.33 |
| 162-215 | 64.71 | 29.41 | 0 | 5.88 | 0 |
| 216-269 | 57.89 | 15.79 | 21.05 | 0 | 5.26 |
| 270-323 | 53.85 | 23.08 | 15.38 | 0 | 7.69 |
| 324-377 | 68.72 | 10.53 | 10.53 | 0 | 10.53 |
| 378-431 | 87.50 | 6.25 | 0 | 6.25 | 0 |
| 432-485 | 50 | 31.25 | 6.25 | 0 | 12.50 |
| 486-539 | 64.71 | 17.65 | 11.76 | 0 | 5.88 |
| Avg overall | 59.45 | 17.85 | 9.00 | 7.59 | 6.41 |
| Std dev | 12.57 | 7.64 | 6.86 | 11.59 | 4.77 |
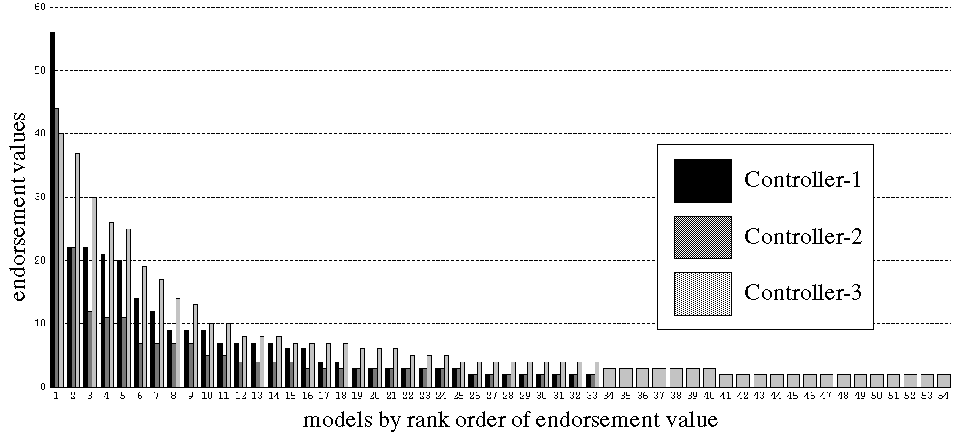 |
| Figure 8: Model endorsement values by instances of Controller without communication between controllers |
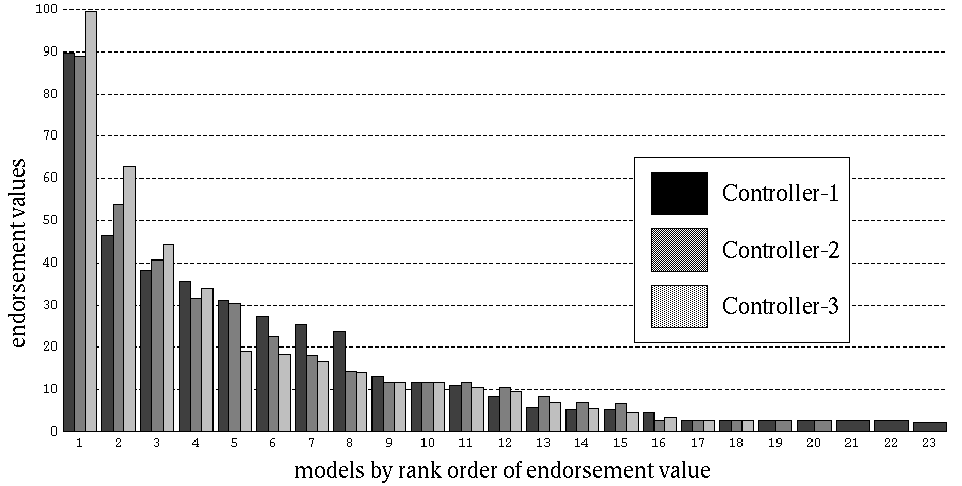 |
| Figure 9: Model endorsement values by instances of Controller with communication between controllers |
2 It should be noted that clause definitions can be made private in which case they can be asserted and retrieved only by the agent on whose databases they are stored. Any such agent must be of the type for which the clause is defined.
CARLEY, K. M. and D. Svoboda (1996), "Modeling Organizational Adaptation as a Simulated Annealing Process," Sociological Methods and Research 25(1), pp. 138-168.
COHEN, P.R. (1985), Heuristic Reasoning: An Artificial Intelligence Approach (Boston: Pitman Advanced Publishing Program). COOPER, R., J. Fox, J. Farringdom and T. Shallice (1996), "A systematic methodology for cognitive modelling", Artificial Intelligence, v. 85, pp. 3-44.
HUBER, G.P. 1991, "Organizational learning: The contributing processes and the literatures", Organizational Science, v. 2, pp. 88-115.
JIN, Y. and R. Levitt (1996), "The Virtual Design Team: A computational Model of Project Organizations", Computational and Mathematical Organization Theory, v. 2, pp. 171-195.
LAIRD, J.E., A. Newell and P.S. Rosenbloom (1987), "Soar: An architecture for general intelligence", Artificial Intelligence, v. 33, pp. 1-64.
MILLER, G.A. (1956), "The magic number seven, plus or minus two: Some limits on our capacity for processing information", Psychological Review, v. 63, pp. 81-97.
MOSS, S. (1995), "Control metaphors in the modelling of decision-making behaviour", Computational Economics, v. 8, pp. 283-301.
MOSS, S. and Edmonds, B. (1997), "A knoweldge-based model of context-dependent attribute preferences for fast-moving consumer goods", Omega, v. 25, pp. 155-169.
MOSS, S. and Edmonds, B. (1998), "Modelling economic learning as modelling", Cybernetics and Systems, v. 29, pp. 215-247.
NEWELL, A.(1990), Unified Theories of Cognition, (Cambridge MA: Harvard University Press).
PRAHALAD, C.K. and R.A. Bettis (1986), "The dominant logic: A new linkage between diversity and performance", Strategic Management Journal, v.7, pp.485-501.
TAMBE, M. (1997) "Towards Flexible Teamwork", Journal of Artificial Intelligence Research, v. 7, pp. 83-124.
TAMBE, M. and P.S. Rosenbloom (1996) "Architectures for Agents that Track Other Agents in Multi-agent Worlds", Intelligent Agents, II, Springer Verlag Lecture Notes in Artificial Intelligence (LNAI 1037).
YE, M. and K.E. Carley (1995), "Radar Soar: towards and artificial organization composed of intelligent agents", Journal of Mathematical Sociology, v. 20, pp. 219-246.
Return to Contents of this issue
© Copyright Journal of Artificial Societies and Social Simulation, 1998