© Copyright JASSS


Ian S. Lustick (2000)
Agent-based modelling of collective identity:
testing constructivist theory
Journal of Artificial Societies and Social Simulation
vol. 3, no. 1,
<https://www.jasss.org/3/1/1.html>
To cite articles published in the Journal of Artificial Societies and Social Simulation, please reference the above information and include paragraph numbers if necessary
Received: 11-Nov-99
Accepted: 22-Jan-00
Published: 31-Jan-00
 Abstract
Abstract
-
Agent-based modeling is an alternative and complementary approach to the study of political identities, including ethnicity and nationalism. By generating many runs with different initial conditions large data sets of virtual histories can be accumulated. This paper presents the ABIR (Agent-Based Identity Repertoire) model which seeks to refine, elaborate, and test constructivist theories of identity and identity change. In this model agents with activated identities interact on a landscape. These agents have repertoires of latent identities. A simple set of micro rules, conforming to constructivist theory's standard propositions about the fluidity, multiplicity, and institutionalizability of identities, as well as their responsiveness to changing incentive structures, determines in any particular interaction what identities will be activated, deactivated, or maintained. Macro-patterns that emerge from these myriad micro-interactions can then be systematically studied. Experiments reported in this paper focus how variation in the size of agent repertoires can affect tension reduction and aggregation across the
landscape. Results suggest that tipping and cascade effects are much more likely when a
small number of exclusivist identities are present in a population.
- Keywords:
-
Agent-based Modeling,
Identity,
Constructivism
 A Constructivist Consensus
A Constructivist Consensus
- 1.1
- Studies of identity--ethnic, national, or otherwise--now begin almost as commonly with a statement decrying the practice of comparing primordialist and constructivist approaches as they do with that comparison itself. This is a relief. As one scholar put it in 1998:
Today...few students of ethnicity would quarrel with the notion that individuals possess multiple identities, that different identities become salient in different settings, and that the salience of one identity vis-à-vis another is often a product of the bearer's own choosing. The old, and sterile, "primordialist"/"instrumentalist" debate is largely over. (Posner, 1998)
For our purposes, we may take this formulation as a not-to-be-problematized portion of our background knowledge. Regardless of how we approach the problem of studying ethnic identity and its political meanings, we can begin by assuming we each approach the topic constructivistically. From this position, identities at both the individual and collective levels are ultimately fluid, chosen, instrumentalizable, responsive to change in relevant incentive structures, and liable to be manipulated by cultural or political entrepreneurs. Examples of more or less standard positions within this approach are (Aronoff 1998; Brass, 1980; Kowert and Legro, 1996; Laitin 1998; Nagel 1994; Tilly 1988). Extremes within this general perspective are anchored on one side by arguments of the sort made by Walker Connor (1998), A.D. Smith (1981, 1986), David Brown (1988), and some socio-biologists such as Gary R. Johnson (1997). These scholars emphasize the psychological affinity of identity appeals based on kinship patterns or tropes in order to explain why communities imagined in common descent terms are so prevalent, stable, and politically potent (i.e. why the effects of opportunities for choice are so limited). At the other extreme are those scholars more impressed with the extraordinary variability of ethnic and other forms of cultural identification over time and in different circumstances. Indeed some sociologists, anthropologists, and cultural studies scholars operating in this mode shift their attention entirely from the individuals and groups themselves (and their putative "identities") to the prevailing categories of identification and the relationship of changing circumstances to "performances" of those categories. Rogers Brubaker is one of the most influential scholars taking this perspective. (Brubaker 1996) Some political economy approaches to identity also tend toward extreme positions of the sort that implicitly imagine any identity as presentable by any actor or group depending on incentives and the choices those incentives make attractive. (Hardin, 1995)
- 1.2
- But surrounding these differences is a convergence of theoretical attitudes. The constructivist paradigm opens wonderful opportunities for complementary application of different approaches to the study of an important set of inter-related phenomena. Because the basics are agreed upon, the dynamics, implications, expectations, and consequences of contingent and malleable processes of identity formation, change, stabilization, and performance can be studied in many different ways: with formal rational choice perspectives, with the tools of empirically ambitious game theory, by manipulating, sifting, and analyzing available aggregate data along relevant demographic, economic, or electoral dimensions, with thickly descriptive, context sensitive case studies, according to hegemonic theories of institutionalized norms, and, as I shall argue, with computer deployed agent-based models.
- 1.3
- Yet this convergence also poses significant, even daunting challenges for those who would gather the intimate data implied as necessary by the categories of this general approach. Primordialism, for all its faults, had the virtue that once people were sorted into the proper "zoological" groups, with their essential characteristics divined, confident predictions could be made about the behavior of their members without actually examining or observing them. Constructivists, on the other hand, must somehow probe the multiplicity of identities available to individuals, the range of "identity projects" available within a population or across overlapping or intermingled populations, and the relationship of those identities to changeable sets of preferences and changeable institutional circumstances. The data gathering problems created by the theory are compounded when the researcher's interests are directed toward exotic, logistically inconvenient, or even dangerous field sites.
- 1.4
- As work done by many intrepid and theoretically sophisticated field researchers shows, it is possible to gather and analyze data relevant to constructivist images of how people trade, instrumentalize, or contextualize their politically relevant identities. It is even possible to discover or arrange natural experiments to use available data to explore the plausibility of certain basic expectations of the overall constructivist posture. Although the overwhelming majority of this research has been focused on simply illustrating or demonstrating the constructed nature, the constituted aspect, of political or cultural identity, some have managed more than this. Thus Laitin (1986) used a hegemonic approach to explain the priority given by Yoruba in Nigeria to ancestral city cleavages over religious identities. Subsequently he has used tipping models to capture the result of mass choice among language repertoires and alternative "identity projects" under somewhat different circumstances (Laitin 1998). Similarly, Posner (1998) shows that changed institutional circumstances in Zambian elections can produce changed patterns of identity based voting. Nothing should or will replace this kind of theory informed field research. But the investment of time and attention to specific cases in this approach is exceedingly high. Nor is it often possible to control variables well enough and often enough to proceed quickly and reliably to more refined claims about the world. The fate of such research projects is also inevitably linked to the fortune of being able to find or construe well-structured natural experiments and (in many cases) to rely on the accuracy and appropriateness of publicly available data sets.
 Agent-Based Models for the Study of Collective Identity
Agent-Based Models for the Study of Collective Identity
- 2.1
- Difficulties of amassing and manipulating collective identity data into theoretically potent comparisons are among the reasons that agent-based modeling can play an important role in the elaboration, refinement, and testing of the kind of specific and logically connected theoretical claims that constructivists have been faulted for not producing. Because the models are run on computers there is no room for ambiguity in the specification of the model's underlying rules. While this means that some stipulative "patches" must be used to operationalize the theoretical hunches contained in constructivist theories, it also poses the necessary and edifying challenge of clarifying exactly what a constructivist theory of political identity, identity formation, and identity change would look like, and what overlooked hypotheses might be buried within its unpacked basic claims.
- 2.2
- Agent-based modeling is an extension in the use of devices known as cellular automata. The most famous of these is the "Game of Life," developed by John Conway and his students. The basic principle is well illustrated in that game, in which a very small number of algorithmic rules for locally communicating spaces that can be "on" or "off" produce circumstances in which inital arrangements lead to spectacularly higher levels of organization and regularized patterns susceptible to treatment as self-contained universes of phenomena, effects, and, virtually, random behavior.[1] Computer modelers, evolutionary game theorists, complexity theorists, and evolutionarily inclined social scientists such as Robert Axelrod (1997), Lars-Erik Cederman (1997), and Joshua Epstein and Robert Axtell (1996) have harnessed computer simulation capabilities to this technique seeking to match agent-based models of this sort with research predicaments, outstanding questions, and clusters of theory in various social science domains. In this paper I want to suggest and illustrate the specific utility of this approach for studying ethnicity and questions of collective political identity.
- 2.3
- The overall approach reflects a basic disinclination to accept a metaphysic that requires acceptance of "action at a distance." Closely related to the "bottom-up" posture of evolutionary theory and complexity approaches to the "emergence" of higher levels of organization, it is a stance that prefers explanations that do not require leaps of imagination to contradict our best assessments of how human beings behave. This is a commitment to reverse engineering, to dissatisfaction with claims of causal effect unless there is some plausible route specified, from the independent to the dependent variable. Axelrod's admonition to design models by adhering to the master KISS rule: "keep it simple, stupid" (Axelrod, 1997, pp. 4-5) reflects an attempt to provide mechanisms for linking independent and dependent variables whose plausibility, at least, will not be challenged. That is, by keeping the behaviors available to agents limited and algorithmic, Axelrod and other agent-based modelers aspire to produce evidence in support of stories which, if not confirmably true, at least cannot automatically be categorized as false because they contradict what we know of human capabilities.[2]
- 2.4
- Computer simulation then presents itself as a technology for creating virtual histories permitting systematic examination of the consequences, via known mechanisms, of variation in initial conditions and loadings on specific variables. The bet is that complex interaction effects produce non-linear transformations or the "emergence" of higher levels of organization out of simple unit level behavior, and that tracking and manipulating these behaviors will afford unprecedented opportunities to explore the dynamics and requirements of emergence processes. By stipulating possible and plausible microprocesses (standardization of responses according to simple rules to locally and readily available cues) microprocesses can be understood. Macro-effects can thus be explained by patterns of adjustment in microprocesses. Evolutionary dynamics can then explain trajectories of change in patterns of microprocesses in relation to macro effects.
- 2.5
- Essentially, the trade-off made in the choice for agent-based modeling approaches is acceptance of the nearly complete artifactuality of the findings (There is no direct need for field data to gather for purposes of testing the model.) in return for the capacity to run very controlled experiments pitting well understood and precisely operationalized conditions against one another. The production of scores, hundreds, and even thousands of "virtual histories" also means that investigators can control for QWERTY effects.[3]
- 2.6
- Some work applying agent based models (ABMs) to collective identity questions has been done. (Axelrod 1997; Cederman 1997, 184-212). These efforts build on more general research applying evolutionary theory to cultural transmission, including study of how cultures emerge and transform out of vast numbers of micro-interactions entailing the diffusion or disappearance of cultural fragments (Boyd and Richerson, 1985). Likening these fragments in some ways to "genes," Dawkins called them "memes," hence the study of "memetics." (Dawkins 1989; Dennett 1995). But although this work is important, and although it does (usually without knowing it is "writing prose") base itself on "constructivist" approaches to identity, it has not been informed or disciplined by the vocabulary, questions, or specific empirical challenges of work by political scientists, anthropologists, sociologists, and cultural studies scholars who have been trying to apply constructivist theory to empirical questions about collective identity.
- 2.7
- In such ABM's, the rules for choosing some among a vast number of possible algorithms, are not themselves produced by a theory about the world in which we can have some degree of confidence, or in whose disconfirmation we would have some reason to be surprised or interested. When ABM's are designed in the absence of externally generated theoretical expectations, the architects of the models often resort to folk theorems based on little more than anecdotal and impressionistic frames of reference. The ready availability of contradictory folk theorems opens the door wide to the temptation to make judgments about the construction of the model based on preliminary exploration of the virtual space created by alpha versions of the model, or by general accumulated knowledge of the "good tricks" (an evolutionary term itself) which lead to interestingly patterned results.
- 2.8
- For example, in his chapter on "A Landscape of Aggregation" Axelrod posits that agents are driven by "propensities" to work together, depending on how much alike they are. Justification for this position from established social psychological theory or international relations theory is not offered. The reader is, in essence, asked to accept that these relationships are commonsensical, or obvious enough, not to require justification. And they are simple enough to conform to the KISS principle. Indeed there may well be validity in these claims, but the model would nonetheless be more convincing if its algorithms were in some explicit sense linked to a pre-existing set of corroborated theories. In any case, once the model created here is tested in the World War II alliance case, to challenge traditional Balance of Power theories, another problem arises from the effort to appeal to common sense, rather than theory, for construction of the model. Who is to say which dimensions of likeness or differentness are to be considered most salient when coding alliance choices in relation to theoretical expectations? Under some circumstances, for example, perhaps the "Orthodox Christian" heritage shared by Russia, Romania, Greece, and other Balkan countries; the Catholic heritage of France, Italy, Poland, Hungary, and Spain, and the more heavily Protestant heritage of Britain, Germany, Holland, and Scandanavia, is more salient than ethnic, linguistic, or ideological similarities or differences. To his credit, Axelrod acknowledges the force of the point made here when he notes at the end of the article that one way to improve the "foundations of landscape theory...is by providing guidance on how the concepts of the theory should be operationalized in a particular application. Having a well-developed set of ideas about how propensity should be measured would be particularly helpful" (Axelrod 1997, pp. 93-94).
- 2.9
- In his most direct study of culture and identity, "Disseminating Culture" (1997, 145-177) Axelrod makes an admirable and partially successful attempt to address this problem. Some substantial attention is directed to social psychological literature on "social influence theory," a literature suggesting that people who share attributes do come more easily to share beliefs (151). This basic position, combined with Deutsch-style "transactionalist" expectations associated with the contact hypothesis, produces a model in which agents sharing more traits interact with each other more, and thereby increase the odds, almost guaranteeing, that they will become more like one another. But close consideration of this model suggests that most of its dramatic results derive from the rule that creates a powerful positive feedback loop toward sharing all traits once one similarity triggers more interaction between two agents. Indeed, the only thing that then stops the system from moving toward complete convergence are the initial conditions which may produce so much convergence so quickly in different zones that no similarities at all stretch across the zonal boundaries. A powerful tendency toward convergence, in other words, is built into the model (not really emergent from complex interactions within it) by algorithmically producing more contact with similarity, and, automatically, more similarity (up to complete identity) with each interaction. These rules are far stronger, it would appear, than the theories to which reference is made would justify.
- 2.10
- My contention is that both constructivist theory and agent-based modeling can benefit by closer contact and my work aims to accomplish this. The model I will now describe, and some experiments with it whose results I will here report, was produced by inferring as systematically as possible from prevailing constructivist theories the categories, conditions, and transformation rules that should govern the operation of agents and the design of landscapes within which they operate.
- 2.11
- My report of some initial and preliminary findings of experiments with this model will be presented as follows. First I shall briefly explain the fundamental elements of the model, surveying some of its capacities. Second, I will describe three experiments performed with the model. I will then report the results of those experiments, followed by a brief discussion of these results and the directions of our continuing research.
 Description of the Agent-Based Identity Repertoire (ABIR) Model
Description of the Agent-Based Identity Repertoire (ABIR) Model
- 3.1
- The Agent-Based Identity Repertoire (ABIR) model I am about to describe was developed over many iterations and via intensive discussions between me and my computer programmer, , over the last year. Dergachev wrote the program for this model in "C" in 1998 and 1999. However, its feasibility was first demonstrated by a rudimentary version developed in JAVA by Daniel Shapero, a student at Johns Hopkins University, in work done in 1997 and 1998. The current version of the model (not the source code) is fully downloadable for Windows 98 or NT at http://www.math.upenn.edu/~vdergach/ps-i.[4] A more advanced version (2.0) designed with Linux, is still in its alpha stage and is also available, though not yet recommended for use. Experiments conducted with ABIR and reported here were conducted by me and by Dan Miodownik.
- 3.2
- The ABIR model begins with a landscape comprised of square shaped agents. The size and shape of the landscape are among the variables that can be stipulated for purposes of experimentation. Each agent communicates directly with its Moore neighborhood of eight agents, four touching its sides and four touching its corners. Each agent appears as a particular color, to which a number is assigned labelling this, its currently "activated" identity. At the beginning of a "run" the landscape is "reseeded," randomizing both the distribution of activated identities and that of subscribed identities. An agent's activated identity is one among a stipulatable number of identities which comprise each agent's identity "repertoire." It is this notion of "repertoire," along with the conditions under which different identity elements from it are evoked and the circumstances under which it can be changed, which distinguishes this model as a simulation of collective identity rather than a general model of trait dissemination or contagion.[5] The identities in each agent's repertoire, including its activated identity, comprise a subset of the total number of identities present in the repertoires of all agents in the landscape. This number, of identities present across the landscape, is also stipulatable, though in the current version of the model the limit for this number is 20.
- 3.3
- There are two kinds of agents: basic agents and entrepreneurs. The exact proportion of each in any landscape is stipulatable for experimental purposes, as is the size of the repertoire of entrepreneurs. However, all entrepreneurs have repertoires that are larger than those of basic agents. Entrepreneurs also differ from basic agents in the rules governing their interaction with neighbors. In every time period each agent compares its own activated identity to the activated identities of its neighbors. (The exact micro-rules are attached to this paper as Appendix A.) These calculations are performed synchronously, except that all entrepreneur agents make their calculations and implement the results before basic agents do. By adding the number of agents activated on different identities each agent determines identity weights in its neighborhood. If the neighborhood identity weight of its activated identity is equal to or higher than the identity weight of other available identities, no change occurs and its activated identity remains the same. If the identity weight of another identity in its neighborhood, which is also in its repertoire, is significantly higher than the weight of its activated identity, the agent changes its activated identity to conform to that with the greatest identity weight and its previously activated identity remains in its repertoire.
- 3.4
- The calculation of identity weights is adjusted by two factors in addition to the number of Moore neighborhood agents activated on individual identities. In every time period each identity present in the repertoire of any agent in the landscape is assigned a bias value. This value changes with stipulatable frequency (volatility) and range (extent of possible change in negative or positive direction). The repertoires of agents represent the multiplicity and potential fluidity of identities associated with cells, individuals, or groups, etc. The inclination to adopt an unactivated identity within an agent's repertoire is meant to conform to prevailing theoretical beliefs about situationally responsive choices among identity projects, so these changing bias numbers (randomly generated at stipulatable rates) are meant to represent changing environmental signals about the current value of being activated on one identity or another.
- 3.5
- Calculation of identity weights is also affected by the presence of entrepreneurs in the Moore neighborhood. The identity activated by an entrepreneur is counted by agents in its neighborhood as two, rather than one. Entrepreneurs, in other words, are figured as more influential than basic agents. The algorithms determining entrepreneur behavior also differ from those producing basic agent calculations in that an entrepreneurs changes its activated identity to one within its repertoire after noticing even a slight identity weight difference. Likewise, although basic agents can substitute new identities for old ones in their repertoires if the identity weight superiority of the new identity is overwhelming compared to their activated identity, entrepreneurs are more sensitive , and more ready, to discard identities within their repertoires for new, but attractive identities. In sum, entrepreneurs are modeled as having larger repertoires, more influence, more sensitivity to shifts in their incentive structure, and more openness to changing their repertoires as well as their activated identities.
- 3.6
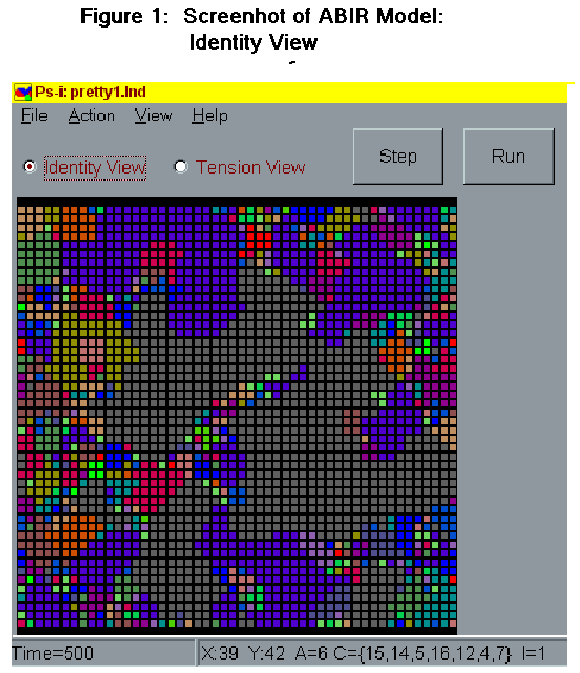
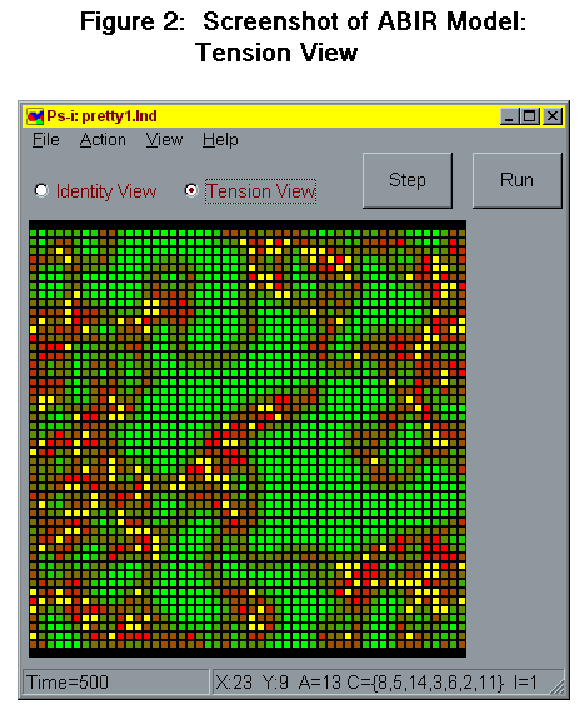
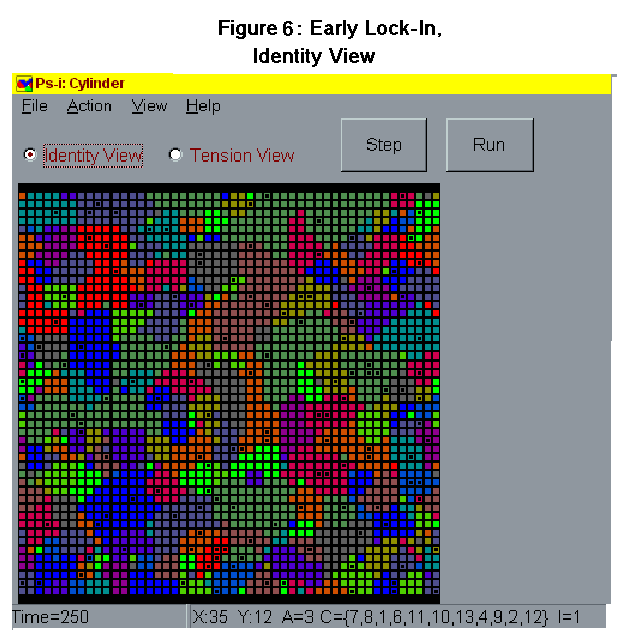
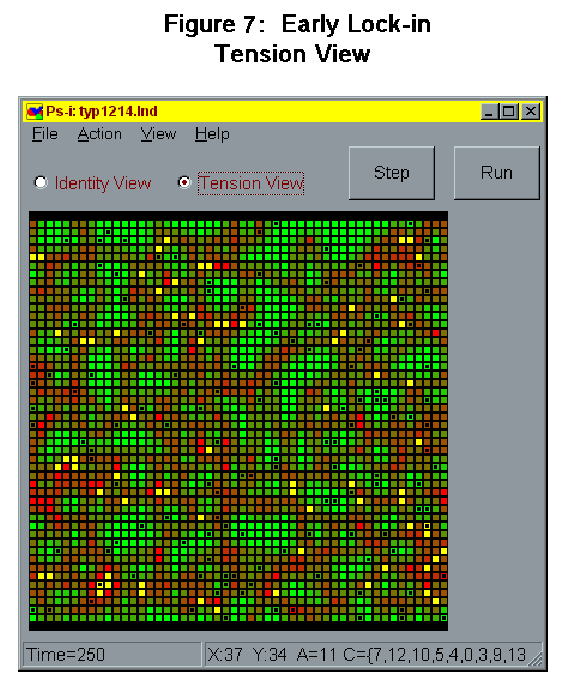
- Statistical monitors within are used to track changes in the distribution of activated and subscribed (within repertoire) identities over time and to describe changing "tension" levels. Tension levels are determined, at each time period, by counting the number of encounters between agents activated on different identities. The model can be viewed dynamically in two displays. The activated identity display shows expansion and contraction in the activated presence of different identities across the landscape, with each identity in the landscape assigned a distinct color. In the tension display, the evolving history of the landscape can be viewed in terms of locally present encounters between similar or dissimilarly activated agents. In this display, yellow represents high levels of difference, red represents medium levels, dark green low levels, and light green no difference. Figures 1 and 2 show typical ABIR screenshots of an identity and a tension level display of one run of the model at 500 time periods.
 Experiments and Results
Experiments and Results
- 4.1
- Among the simplest relationships we have explored is that between increasing repertoire size and tension level. We have begun our exploration of this topic using a standard array of low settings for environmental turbulence and a moderately sized, mixed type of landscape geometry. The landscape geometry for these experiments is a cylinder, meaning that the top and bottom are bordered with immutable and inactive cells but that the sides wrap around in the form of a torus. Its size is 50X50, including the 100 immutable and inactive agents at the top and bottom, rendered in black. The volatility level was set at .005 (meaning that for each identity at each time slice there is a .005 probability that the bias assigned to it will be eligible for reassignment). The range within which bias variation can occur was set at -2,+1. Fifteen identities were evenly distributed in the initial randomization of the landscape, both in the number of agents activated on particular identities and in the distribution of subscribed identities (those present in the repertoires of agents). Each condition was run twenty times for 500 time periods, recording the results at the 500th time period for each run in each condition. In the simplest condition, there are no entrepreneurs in the landscape.
- 4.2
- Our hypothesis was that at very small repertoire sizes it would be difficult for any identity to expand its presence locally, leading to sluggish patterns of change across the landscape and a kind of "atomization" of the landscape in which relatively few agents came to unite with those around them by activating on the same identity. We further hypothesized that as the repertoire size of agents across the landscape increased, that tension levels would fall as agents found more agents in their neighborhood with overlapping identity repertoires. Locally overlapping repertoires would then be translated into more frequent changes of activated identity in response to the appearance of positive biases regarding those overlapping identities. The patterns of conformance in activated identity that would arise would lower the overall tension level in the environment, meaning that the number of encounters between agents not activated on the same identity would fall. We did not hypothesize specifically about the rate of the decline in tension levels.
- 4.3
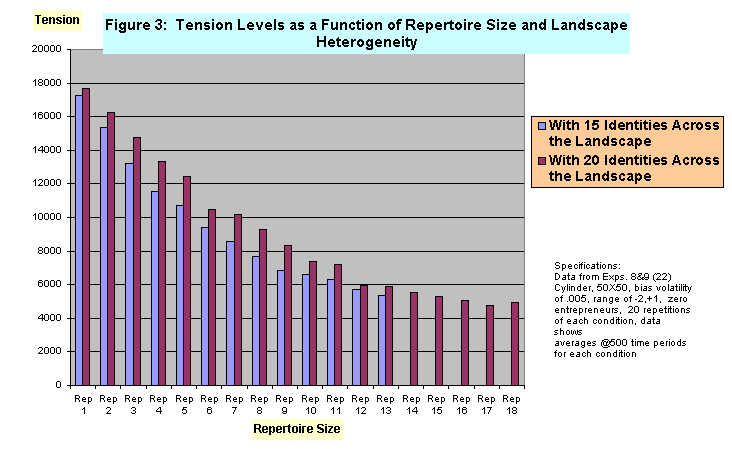
- The results of our experiments confirmed our initial expectations, but also produced a more striking and regular pattern in the relationship between repertoire size and tension levels than we had anticipated. Under the stipulated conditions (including the presence of 15 identities across the landscape population), tension levels dropped rapidly with initial increases in small repertoire sizes. The rate of decrease in tension slowed but continued to decline significantly in the mid-range of repertoire sizes, developing into a small and almost asymptotic rate of decline in the high range of repertoire size.[6] When the experiment was repeated, but within a more heterogeneous landscape--with 20 identities present--and therefore with repertoire sizes varying from 1 to 18, the same pattern was found. Figure 3 displays these falling levels of tension on the Y axis as repertoire size increases along the X axis for landscapes with 15 and landscapes with 20 identities present.
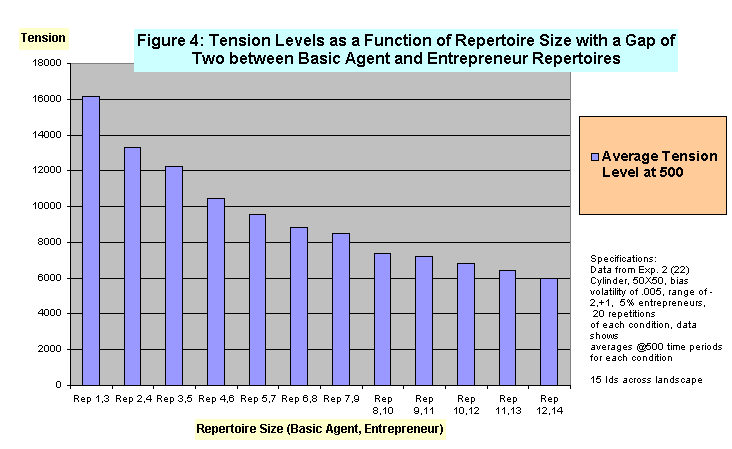
- 4.4
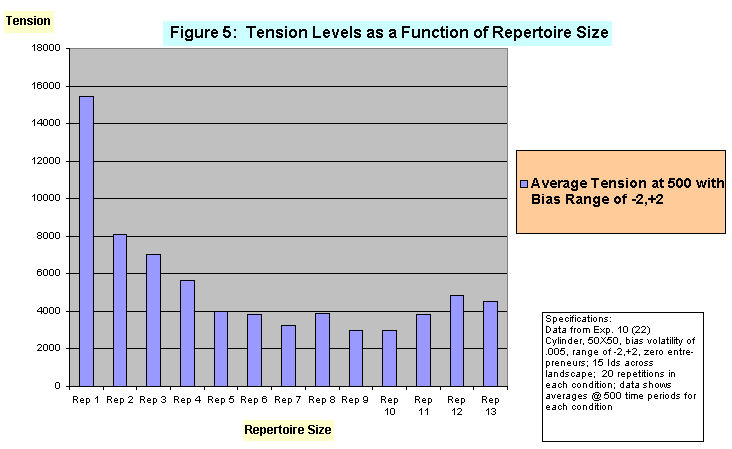
- This effect is also apparent with the introduction of entrepreneurs into the landscape. For example, Figure 4 compares rates of decrease in tension level resulting from increasing repertoire size when 5% of the agents in the landscape are entrepreneurs, and when the repertoire size of an entrepreneur is two identities larger than the repertoire size of a basic agent.[7] When the "riskiness"[8] of the environment is increased by keeping the volatility at .005 but increasing the minimum-maximum range by one third, to -2,+2, landscapes with no entrepreneurs display similar overall pattern. This result is displayed in Figure 5. Here average tension levels drop very sharply in the range of small repertoires, but then level off with increasing repertoire size. With medium and large repertoire sizes, average tension levels are much lower than in the smallest repertoire conditions, and overall are lower than those under less risky environmental conditions, but exhibit greater variability. This appears to be the result of the riskier environment producing some better opportunities for newly advantaged identities to break established patterns of activation while also enabling identities which happen to enjoy a relatively constant, high, and favorable bias to expand their presence into larger proportions of the landscape.
- 4.5
- A more interesting relationship exists between repertoire size and the extent of concentration or aggregation of identity activation that emerges over time. Guidance for our hypothesis in regard to this relationship came in part from standard constructivist theories of how individuals or groups with multiple identity options respond to changing incentive structures and in part from a theory of asymmetric thresholds of institutionalization and deinstitutionalization developed to explain stickiness and non-linearity in patterns of change in the size of states. (Lustick 1993) We hypothesized that as the repertoire size of agents comprising a landscape increased, non-activated identities in agent repertoires would be more likely to activate, and to remain activated following appearances of temporary positive biases. This would occur, we reasoned, because with each agent having a larger repertoire, these non-activated but suddenly advantaged identities would be more likely to find support from neighboring agents with that identity in their (larger) repertoires. This would be reflected in the emergence of larger, more consolidated blocs of particular activated identities. These aggregated blocs of activated identity concentration, having emerged and, one might say, "institutionalized" their control of particular spaces, would then tend to protect themselves against the pressures toward shrinkage which more unfavorable biases, arising later in the history of the landscape, would produce. We expected that landscapes in which identities could gain this kind of an early lead in the concentration of their presence would also produce, by the end of 500 time periods, relatively more histories featuring a small number of prevalent or dominant activated identities at the end of 500 time periods.
- 4.6
- We did indeed find this effect. But we also found the suggestion of something else just as interesting. As the size of the repertoire increased to become a relatively large fraction of the number of identities across the landscape, the aggregate amount of concentration in the landscape at the end of 500 time periods leveled off and even began to decrease. This tendency toward curvilinearity, we believe, results from the initial burst of expansion that evenly distributed identities can expect to enjoy when agents share almost all of one another's identities. This means that even without favorable biases, but with a random distribution of initial conditions, very small clusters of neighboring agents who happen to be activated on the same identity will quickly expand by triggering activation on their identity from among their many neighbors who share it within their repertoires. But typically this process leads to a kind of early lock-in where many clusters of activated identities are big enough to resist small negative biases, but not strong enough, even with positive biases, to break down the solidity of the clusters that border them. See Figure 6 and 7 for screen shots (one in identity view, and one in tension view) of a typical early lock-in (at time 100) landscape characterized by a proliferation of many small but well defined clusters of activated identity with very little tension across the landscape.
- 4.7
- One overall measure of concentration that we use is the Herfindahl Index, traditionally employed to describe the extent of concentration in an industry or market for econometric or anti-trust purposes. This aggregate index is calculated as equal to the sum of the squares of the market shares. To employ this index we use a statistical monitor built into the program which describes, at each time period, the number of identities with activated agents occupying 0-10% of the landscape, 10-20%, 20-30%, 30-40%, etc. If, for example, in a particular run, one identity is seen to occupy between 10 and 20% of the landscape and two identities are seen to occupy between 20% and 30%, then the Herfindahl index for that run is calculated by treating the first identity as occupying 15% of the space and each of the other two identities as occupying 25%. The square of .15 is.0225. The square of .25 is .0625. Doubling .0625 (because there were two identities occupying between 20 and 30% of the landscape) and adding it to .0225 a Herfindahl index of concentration is calculated as .1475.[9]
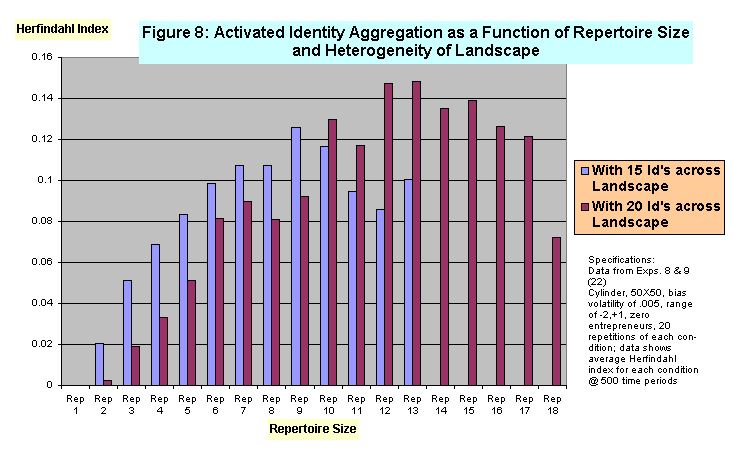
- 4.8
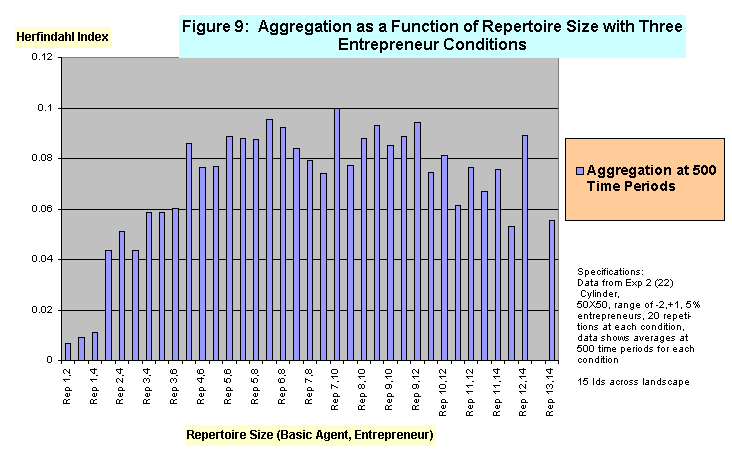
- The mildly curvilinear relationship between increasing repertoire size and amount of activated identity concentration is illustrated in Figure 8. The chart shows that with zero entrepreneurs present Herfindahl index scores rise from very low levels when repertoires are small to high levels in the medium range of repertoire sizes, before declining somewhat in the high range of repertoire sizes. The chart shows that these effects are present both when there are 15 identities present across the landscape, and when the landscape is more heterogeneous -- i.e. when there are 20 identities distributed across the same number of agents in the same kind of landscape. Figure 9 shows that when entrepreneurs are added, and the size of their repertoires are varied from one to three more than that of basic agents, that the curvilinear relationship of identity aggregation and repertoire size remains.
- 4.9
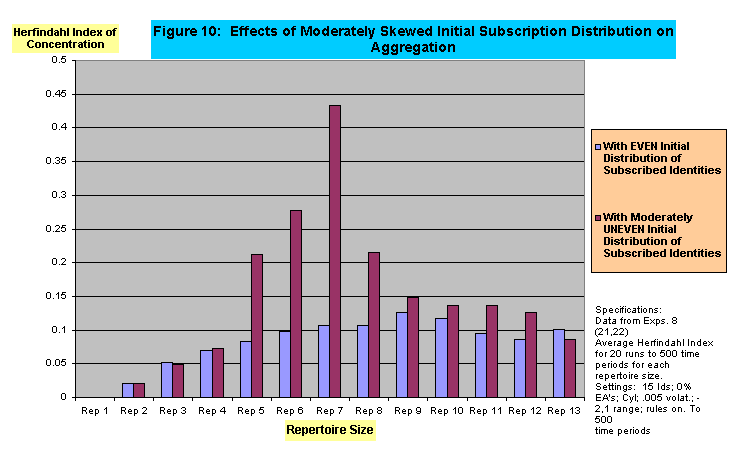
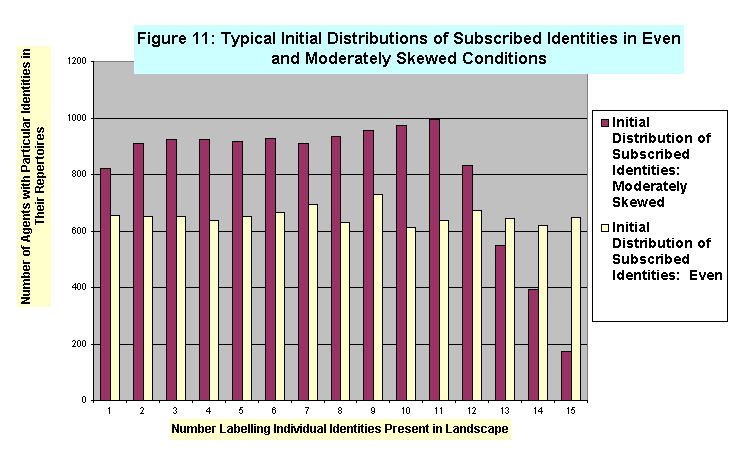
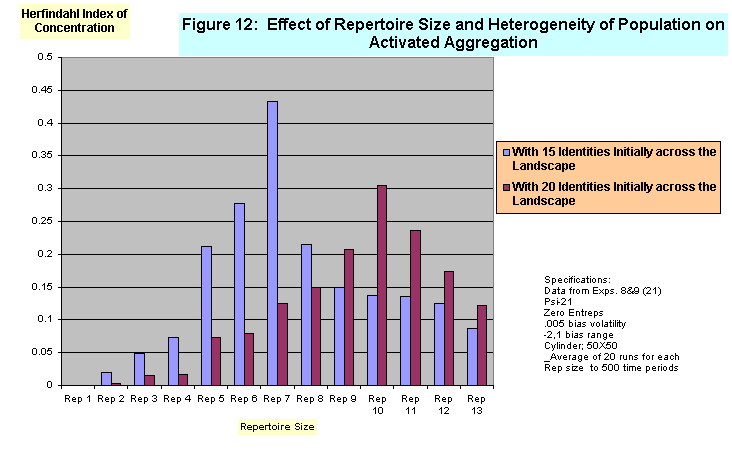
- The robustness of this effect is given even stronger support in a more subtle manipulation. The results displayed in Figure 10 were produced when identities were initially distributed randomly at the activated level, but when this random distribution of activated identities was accompanied by a mild degree of skewness in the distribution of subscribed identities. In the moderately uneven, or skewed initial subscription condition, twenty per cent of identities appearing in the initial landscape were present in significantly fewer agent repertoires than the other 80%. Figure 11 shows typical initial distributions of subscribed identities in the even and moderately skewed condition. We see in Figure 10 that the curvilinear pattern is considerably more pronounced under conditions of a moderately skewed subscription distribution than when the initial distribution at the subscription level was even. As shown in Figure 12, this effect is maintained, for moderately skewed initial subscription distributions, in conditions of both moderate and high heterogeneity (15 vs. 20 identities present in the population).
- 4.10
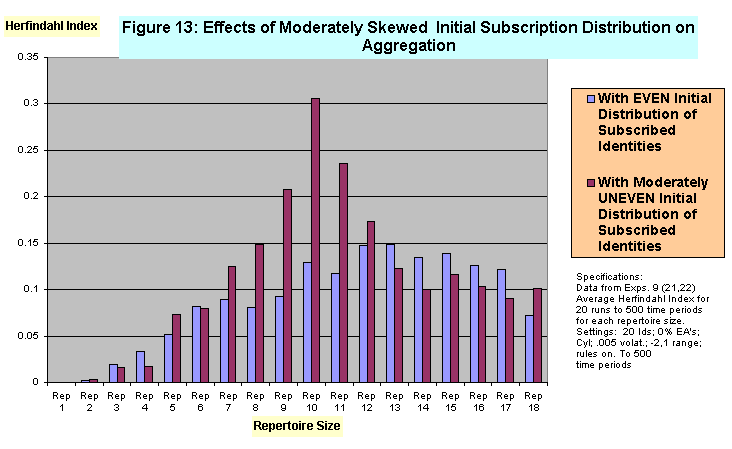
- We can think of this phenomenon as suggestive of a non-intuitively obvious effect of the presence within a population of exclusivist identities. To exist within an identity repertoire that contains more than one identity, any particular identity must be able to "co-exist" within the same agent's repertoire at the same time, even if only one or neither are activated. An "exclusivist" identity can be thought of as an identity that finds some other identities present in the population so distasteful or so inconsistent with its own implicit claims about the individual and the world, that it cannot coexist with those identities within the set of the agent's subscribed identities. To the extent that an identity is exclusivist in this sense it will appear in the set of subscribed identities of fewer agents than will inclusivist identities-identities more capable of tolerating diversity within an agent's repertoire. Looking again at Figure 10 we see that in the middle range of repertoire sizes (5-8 in a landscape with 15 identities) Herfindahl indexes in the moderately skewed condition are two to four times what they are in the even distribution condition. Figure 13 shows a similar pattern, but with the middle range located between repertoire sizes 8-11 for a more heterogeneous population (20 identities present in the landscape). Figure 14 shows that although this effect remains apparent when entrepreneurs are introduced into the landscape, the absolute level of aggregation achieved is substantially lower and the presence of the effect becomes more prominent, at least in these initial experiments, in the 7-11 range of basic agent repertoire size.[10]
- 4.11
- What appears to account for this striking effect of the presence of a small proportion of exclusivist identities? Our hypothesis is that the existence of small asymmetries in the latent capacities of subscribed identities to exploit fluctuations in environmental biases increases the probability for already spreading identities that some of these fluctuations will trigger tips or cascades--greatly accelerated increases in the number of agents activated on a subset of the non-exclusivist identities. What is particularly interesting about this result is the counter-intuitive suggestion that inclusivist identities may have a better chance of spreading through a population, and achieving a certain dominance at the activation level, when that population contains some exclusivist identities than if all identities within the population are equally inclusivist.
 Discussion and Implications:
Discussion and Implications:
- 5.1
- Additional experiments are being conducted to test the robustness of these findings about tension, aggregation patterns, and rates at which identities are extinguished (activation rates of 1% or lower across the population) under other conditions, including higher levels of bias volatility, wider ranges of bias change, and different densities of entrepreneur agents. This paper, however, is meant primarily to introduce the technique and some initial findings in order to establish the availability, or at least the plausibility, of agent-based modeling as an aggregate data based technique for learning about ethnic and other kinds of identity politics and conflict. The study is also designed to show that agent-based models can be designed to conform to rather specific requirements of free-standing theories under discussion on the frontiers of political science, anthropology, and other related disciplines and that they can be used to pose and even answer hitherto not addressed, or inadequately addressed, questions. In this sense this research is a response to the problem of over-reliance on "common sense" or folks theorems noted earlier as present in some of the work of Axelrod and others.
- 5.2
- Substantively, the scope of the research reported here has been limited. In particular we do not here explore very deeply the role of entrepreneurs--of agents who have relatively larger repertoires, who monitor their environments more sensitively, who have greater effects on their neighbors, and who more aggressively trade their identities for current advantage, and who make their decisions before other agents. In constructivist theories of identity, however, they play an important role in facilitating changes in collective identities to correspond to very new or long ignored circumstances. Preliminary findings reported here and elsewhere (Lustick with Miodownik 1999) suggest that in the ABIR context entrepreneurs work to foster diversity when environmental turbulence or other conditions produce powerful cascades that would otherwise push the landscape toward uniformity. Under conditions of atomization and relative stagnation, however, entrepreneurs, we believe, will encourage higher levels of aggregation. The presence of entrepreneurs, who do not act synchronously with basic agents, also helps ABIR explore the difference between synchronous and asynchronous modeling and helps establish the robustness of our findings in the absence of entrepreneurs or pure synchronicity.
- 5.3
- From these few ABIR experiments it is apparent that real advances in the refinement, elaboration, testing, and critique of constructivist theories of identity are possible using these techniques. Thus, while constructivists standardly model agents as possessing multiple identities, virtually nothing has been said by constructivist theorists about the possible implications of variability in the size of these repertoires. One reason for this is the difficulty of gathering this kind of data reliably. But with ABIR it is possible to conduct thought experiments rigorously, according to counterfactual logic, with statistical precision, and with virtually unlimited possibilities for operationalizing the kinds of factors constructivist theories might deem important.
- 5.4
- This kind of work also holds out the prospect of making direct contributions to game theoretic and other rational choice approaches that seek to explain patterns of collective mobilization and its absence by algorithmic responses of large numbers of heterogeneous agents. Prominent here is Timur Kuran's work (Kuran 1995) on a variety of phenomena related to what he calls "preference falsification" and David Laitin's previously cited investigations of tipping effects in the processes of identity formation. (Laitin 1998) Just as exciting is the potential for harnessing insights from the burgeoning fields of complexity, studying the linear and non-linear dynamics of emergence processes (Holland 1998) and evolutionary psychology (Boyd and Richerson 1985). As noted above, this latter approach includes the notions of "meme" and "memetics." Again, the claim here is that the appropriate unit of analysis for the study of culture is the ideational fragment (analogous in some ways to a "gene") rather than the individual (Dawkins 1989, Dennett 1995). It would appear that the ABIR model can give significant support to this theory. Indeed it is worth noting that unlike many other agent-based models, it is not agents who live, die, and evolve in the histories of landscapes or populations, but the identities (or one might say "memes") at the subscription level that either proliferate or shrink away toward extinction. Findings regarding agent-level tipping effects reported here are therefore illustrative of the way ABIR can help identify mechanisms linking micro patterns to macro outcomes.
- 5.5
- In the versions[11] of the ABIR model used in these experiments the capacity exists to custom design landscapes of many kinds--mixtures of agents of different size repertoires in different spatial distributions, landscapes with various sorts of blockades, bottlenecks, curves, limits to spatial accessibility, openness, etc. These design capabilities permit application of the technique for, among other things, study of structural and diffusionist theories in international and comparative politics. Histories of dynamic landscapes can also be interrupted with "punctuations" of severe environmental turbulence. Individual landscapes can be saved so that the effect of initial conditions can be tested, and the distribution of possible micro histories of specific locales explored. Different kinds of agents can also be designed, including fanatics (agents who do not make calculations about identity weights but who do influence their neighborhoods); apathetic agents (who do not influence their neighbors but who do calculate identity weights and respond to what they notice); and locally influential agents, (whose activated identities can count for significantly more than basic or even entrepreneurial agents in the identity weight calculations of their neighbors). [12]
- 5.6
- As noted above, a new alpha version of the program is now available and has greatly expanded capacities, including the ability to manipulate some of the rules according to which agents respond to one another. It is also equipped with much more finely grained statistical monitoring capabilities. This new version will also lay the basis for exploring systematically an important question posed to all agent based modeling efforts--the implications of synchronicity vs. asynchronicity in the pattern of change in the state of agents in the population. Insofar as entrepreneurs in an ABIR landscape act before all basic agents in any time period, it is already possible, to some extent, to examine this question. But expanded capacities in this area will be very important.
- 5.7
- Meanwhile all researchers are invited, not only to download the ABIR model, but to replicate or extend the experiments reported in this paper.
 Acknowledgement
Acknowledgement
-
I am very grateful for the assistance provided by Dan Miodownik in
connection with the preparation of this article.
 Notes
Notes
-
1See Dennett (1995) pp. 163-181 for an excellent introduction to Conway's Game of Life. See Fearon (1997) for highly relevant considerations regarding use of cellular automata according to the general approach taken here. A big difference in our treatments is that I am not interested in using ABIR to make point predictions, but agree with Fearon that such predictions are not possible using this kind of model. Our focus instead is explaining variation in distributions of outcomes.
2Concerning the advantages of the simplicity and "naivete" of agents in evolutionary game theory (and by extension, in agent-based modeling) see Mailath 1998, pp. 1355-56.
3By this I mean the assumption that the particular episodes studied in the "real world" are typical of the worlds producible if repeated "runs" could be observed with slightly different initial conditions.
4Point your browser at this address, scroll to the bottom of the page, and click on "Download" the windows version.
5In separate research the model has been adapted to simulate repertoires of arguments possessed by more or less sophisticated citizens (Lustick with Miodownik, 1999). It is an empirical question how broadly the basic mechanisms modeled with ABIR can be usefully applied in other domains.
6For technical reasons it is impossible to examine landscapes in which the repertoire size is larger than N-2, where "N" is the number of identities present across the landscape.
7This same result occurred when the repertoire size of the entrepreneur was decreased to one more than that of a basic agent, and increased to three, four, five, and six more. Although we have found tension levels to be sensitive to increases in the density of entrepreneurs in the landscape, those results are not reported here.
8The pattern of change in the environmental biases is determined on two dimensions. Change in the range within which biases can vary is considered change in levels of "risk" (or opportunity) while change in the likelihood of variation at any give range is considered change in "volatility."
9This is actually an adjusted version of the Herfindahl index since the identities occupying between 0% and 10% of the landscape population are not included in the sum of squares.
10Similar results were obtained when this experiment, with entrepreneurs present, was run on the more heterogeneous landscape, containing twenty identities.
11The version available on the website is known as PSi-22. It produces even initial distributions of subscriptions with the reseed command. An alternate version, available for anyone who requires it but not currently available on the website is PSi-11. This version produces moderately skewed initial subscription distributions with the reseed command.
12These capabilities are currently being used, in research on political discourse and deliberative democracy.
 References
References
-
Myron J. ARONOFF, "The Politics of Collective Identity," Reviews in Anthropology, Vol. 27, no. 1 (March 1998) pp. 71-85.
Robert AXELROD, The Complexity of Cooperation: Agent-Based Models of Competition and Collaboration (Princeton: Princeton University Press, 1997).
Robert BOYD and Peter J. Richerson, Culture and the Evolutionary Process (Chicago: University of Chicago Press, 1985).
Paul R. BRASS, "Ethnic Groups and Nationalities: The Formation, Persistence, and Transformation of Ethnic Identities over Time," in Ethnic Diversity and Conflict in Eastern Europe, Peter F. Sugar, ed. (Santa Barabara: ABC Clio, 1980) pp. 1-68.
David BROWN, "Why is the Nation-State so Vulnerable to Ethnic Nationalism?" Nations and Nationalism, Vol. 4, no. 1 (1998) pp. 1-15.
Rogers BRUBAKER, Nationalism Reframed: Nationhood and the National Question in the New Europe (Cambridge: Cambridge University Press, 1996).
Lars-Erik CEDERMAN, Emergent Actors in World Politics: How States and nations Develop and Dissolve (Princeton: Princeton University Press, 1997).
Walker CONNOR, "Beyond Reason: The Nature of the Ethnonational Bond," in Ethnonationalism: The Quest for Understanding (Princeton: Princeton University Press, 1998) pp. 196-209.
Richard DAWKINS, The Selfish Gene (Oxford: Oxford University Press, 1989) second edition.
Daniel C. DENNETT, Darwin's Dangerous Idea (New York: Simon and Schuster, 1995).
Joshua M. EPSTEIN and Robert Axtell, Growing Artificial Societies: Social Science from the Bottom Up (Washington, D.C.: Brookings Institution Press, 1996).
James D. FEARON, "Causes and Counterfactuals in Social Science: Exploring an Analogy between Cellular Automata and Historical Processes," in Counterfactual Thought Experiments in World Politics: Logical, Methodological, and Psychological Perspectives, Philip E. Tetlock and Aaron Belkin, eds. (Princeton: Princeton University Press, 1996) pp. 39-67.
Gary R. JOHNSON, "The Architecture of Ethnic Identity," Politics and the Life Sciences, Vol. 16, no. 2 (September 1997) pp. 257-62.
Russell HARDIN, "Self-interest, group identity," in Nationalism and Rationality, Albert Breton, Gianluigi Galeotti, Pierre Salmon, and Ronald Wintrope, eds. (Cambridge: Cambridge University Press, 1995) pp. 14-42.
John H. HOLLAND, Emergence: From Chaos to Order (Reading, Massachusetts: Helix Books: Addison-Wesley Publishing Company, 1998).
Paul KOWERT and Jeffrey Legro, "Norms, Identity, and Their Limits: A Theoretical Reprise," in The Culture of National Security: Norms and Identity in World Politics, Peter J. Katzenstein, ed. (New York: Columbia University Press, 1996) pp. 451-97.
Timur KURAN, Private Truths, Public Lies: The Social Consequences of Preference Falsification (Cambridge: Harvard University Press, 1995).
David D. LAITIN, Hegemony and Culture: Politics and Religious Change among the Yoruba (Chicago: University of Chicago Press, 1986).
David D. LAITIN, Identity in Formation : the Russian-speaking populations in the near abroad (Ithaca, N.Y. : Cornell University Press, 1998).
Ian S. LUSTICK, Unsettled States, Disputed Lands: Britain and Ireland, France and Algeria, Israel and the West Bank-Gaza (Ithaca: Cornell University Press, 1993).
Ian S. LUSTICK with Dan Miodownik. "Deliberative Democracy and Public Discourse: reliminary Findings Using the ABAR (Agent-Based Argument Repertoire) Model". Prepared for the Penn National Commission on Society, Culture, and Community (October 1999).
George J. MAILATH, "Do People Play Nash Equilibrium? Lessons from Evolutionary Game Theory," Journal of Economic Literature, Vol. XXXVI (September 1998) pp. 1347-74.
Joane NAGEL, "Constructing Ethnicity: Creating and Recreating Ethnic Identity and Culture," Social Problems, Vol. 41, no. 1 (February 1994) pp. 152-176.
Daniel N. POSNER, "The Institutional Origins of Ethnic Voting," Paper delivered at the 1998 Annual Meeting of the American Political Science Association, Boston, September 3-6, 1998, p. 4.
A.D. SMITH, The Ethnic Revival (Cambridge: Cambridge University Press, 1981).
A.D. SMITH, The Ethnic Origins of Nations (Oxford: Blackwell, 1986).
Charles TILLY, "Repertoires of Contention in America and Britain, 1750-1830," in The Dynamics of Social Movements: Resource Mobilization, Social Control, and Tactics ed. by Mayer N. Zald and John D. McCarthy, UPA Lanham, MD 1988, 126-155
 Appendix:Rules governing the agent-based identity repertoire model
Appendix:Rules governing the agent-based identity repertoire model
-
The Landscape:
A population of square shaped agents in a two dimensional array comprises a landscape. The shape and size of the landscape is stipulatable.
The Environment:
The environment of the landscape has biases toward each identity present in the repertoires of agents in the population, that is toward all subscribed identities. The set of bias values toward identity x, B(x) is stipulatable. Bias values for each identity change randomly and at a rate determined by an evironmental volatility setting.
Agents:
There are two types of agents who inhabit the environment, basic agents and entrepreneurs. Entrepreneurs are both more sensitive to change in their environments and more influential in their impact on agents in their neighborhood. Each agent (basic or entrepreneur) has a repertoire of C identities. The elements of C will be chosen from a series of D identities (D less or equal to 20) such that no two elements in C may be identical. For the basic agent, the length of C will be L (de facto = 6); for the entrepreneur the length of C will be H (de facto 9) such that H > L. The first element of repertoire C is deemed the activated identity. The activated identity is the way in which that particular agent presents itself to its neighbors. Each agent's elements in C other than the activated element are unknown to other agents.
During each turn, each agent interacts with its Moore neighborhood of agents.
All entrepreneurs act first and in parallel. Each entrepreneur looks to his Moore neighbors and goes through the following process.
- Identity weights for all activated identities in the neighborhood, including the activated identity of agent E in the center of the neighborhood, are calculated. The identity weight (IW) of an identity in a neighborhood is equal to the number of agents in the neighborhood, including E, activated on that identity, plus that identity's environmental favorability bias, plus one point for each entrepreneur in the neighborhood (including the agent in the center) activated on that identity.
(For example, if identity x is activated in 5 agents, two of whom (including the central agent) are entrepreneurs, and if the environmental bias for that identity is -1, then the IW for that identity is 5 + 2 + (-1) = 6.)
- If the identity weight of agent E's activated identity is equal to or greater than the IW of any other activated identity in its neighborhood then E's activated identity remains unchanged, E's repertoire C does not change, and the process ends.
- If an identity, x, in C other than E's activated identity, has an IW greater than that of E's activated identity, then x becomes E's activated identity. The formerly activated identity becomes a non-activated identity in C. If the IW's of more than one identity in the neighborhood and within E's repertoire are greater than the IW of E's activated identity, then the identity with the biggest IW becomes the activated identity for E. If these IW's bigger than the IW of E's activated identity are equal, then one of these identities becomes E's activated identity. Which one? Answer--the one with the largest subscription in the neighborhood, then in the population, and then the lowest digit between the two identity labels.
- If an identity, x, not in C, is activated with an IW at least 3 points greater than E's activated identity, then x is added to E's repertoire (but does not activate on that turn) and the identity in E's repertoire with the lowest IW in the neighborhood is removed from the repertoire. If multiple identities are thereby candidates for removal, the identity listed to the extreme right in the cache is removed.
- If an identity, x, not in E's repertoire, is activated with an IW at least 6 points greater than E's activated identity, then x becomes an activated identity of agent E, the formerly activated identity becomes a non-activated identity within E's repertoire, and an identity in E's repertoire is removed, using the same procedure as in step 4, above.
After entrepreneurs act, all basic agents act in parallel. Each basic agent A looks to his 8 neighbors and goes through the following process.
- Identity weights for all activated identities in the neighborhood, including the activated identity of agent A in the center of the neighborhood, are calculated. The identity weight (IW) of an identity in a neighborhood is equal to the number of agents in the neighborhood, including A, activated on that identity, plus that identity's environmental favorability bias, plus one point for each entrepreneur in the neighborhood (including the agent in the center) activated on that identity.
- If the identity weight of agent A's activated identity is equal to or greater than the IW of any other activated identity in its neighborhood then A's activated identity remains unchanged, A's repertoire C does not change, and the process ends.
- If an identity, x, in C other than A's activated identity, has an IW 2 or more points greater than that of A's activated identity, then x becomes A's activated identity. The formerly activated identity becomes a non-activated identity in C. If the IW's of more than one identity in the neighborhood and within C are 2 or more points greater than the IW of A's activated identity, then the identity with the biggest IW becomes the activated identity for A. If these IW's two points bigger than the IW of A's activated identity are equal, then one of these identities, using the procedure described in step 3, for entrepreneur agents, becomes A's activated identity.
- If an identity, x, not in agent A's repertoire, is activated with an IW at least 5 points greater than A's activated identity, then x is added to A's repertoire and the identity in A's repertoire with the lowest IW in the neighborhood is removed from the repertoire. If multiple identities are thereby candidates for removal, the removed identity is the identity listed at the extreme right of the cache.
- If an identity, x, not in A's repertoire, is activated with an IW at least 7 points greater than A's activated identity, then x becomes an activated identity of agent A, the formerly activated identity becomes a non-activated identity within A's repertoire, and an identity in A's repertoire is removed, using the same procedure as in step 4, above.
Initial Conditions:
Agents' initial repertoires are given with a uniform distribution and randomly. The percentage of entrepreneurs in the population is set at the beginning of each run.

 Return to Contents of this issue
Return to Contents of this issue
© Copyright Journal of Artificial Societies and Social Simulation, 1999
 Abstract
Abstract![]() A Constructivist Consensus
A Constructivist Consensus
![]() Agent-Based Models for the Study of Collective Identity
Agent-Based Models for the Study of Collective Identity
![]() Description of the Agent-Based Identity Repertoire (ABIR) Model
Description of the Agent-Based Identity Repertoire (ABIR) Model
![]() Experiments and Results
Experiments and Results
![]() Discussion and Implications:
Discussion and Implications:
![]() Acknowledgement
Acknowledgement![]() Notes
Notes![]() References
References![]() Appendix:Rules governing the agent-based identity repertoire model
Appendix:Rules governing the agent-based identity repertoire model![]()
Return to Contents of this issue