D. Scott Bennett (2008)
Governments, Civilians, and the Evolution of Insurgency: Modeling the Early Dynamics of Insurgencies
Journal of Artificial Societies and Social Simulation
vol. 11, no. 4 7
<https://www.jasss.org/11/4/7.html>
For information about citing this article, click here
Received: 15-Jan-2008 Accepted: 22-Jul-2008 Published: 31-Oct-2008
 Abstract
Abstract| Table 1: Mean and Standard Deviation of Population Initial Anger, Fear, and Violence Threshold Distributions | ||
| Mean | Standard Deviation | |
| Anger | 0.25 | 0.125 |
| Fear | 0.5 | 0.25 |
| Violence Threshold | 0.5 | 0.25 |
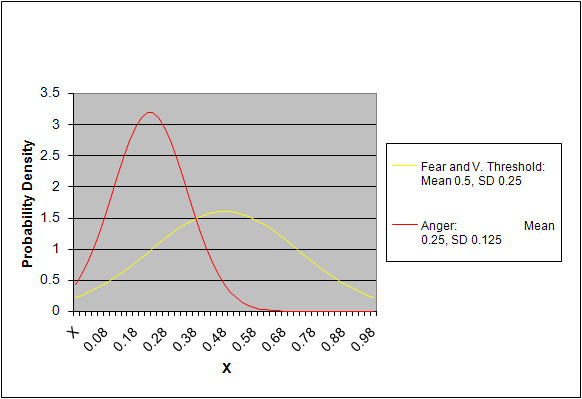
|
| Figure 1. Default Probability Distributions of Fear, Anger, and Violence Threshold |
| Fear t+1 = Feart + 0.10*(1-Feart). | (1) |
| Anger t+1 = Angert + 0.05*(Number of Civilians Hurt)*(1-Angert) | (2) |
If
| Anger t+1 > 1.0, Anger t+1=1.0 | (3) |
For example, if a counterattack injures 5 civilians, then an injured civilian will increase its anger 25% of the way toward the maximum possible anger (1.0).
| Table 2: Summary of Key Model Parameters | ||||
| Parameter | Scope | Definition | Range | Default Value |
| Space Size | Global | Dimensions of map grid | 1+ | 50 |
| Interaction Range | Global | Size of neighborhood for insurgents looking to attack, and for range for collateral damage to civilians | 1 to size of map | 3 |
| Effectiveness | Global / All Soldiers | Probability of removing an insurgent during a soldier's counterattack | 0.0 to 1.0 | 0.8* |
| Accuracy | Global / All Soldiers | 1-accuracy equals the probability of injuring any civilian within interaction range during a soldier's counterattack | 0.0 to 1.0 | 0.8* |
| Sensitivity | Global / All Soldiers | Probability of a soldier responding to an attack. Always 1.0 for this simulation (included for later expansion) | 1.0 | 1.0 |
| Initial Anger | Individual / Each Civilian | Level of this civilian's initial anger at the government | 0.0 to 1.0 | Normally distributed, mean 0.25, std. dev. 0.125. |
| Initial Fear | Individual / Each Civilian | Level of this civilian's initial fear of government response to insurgent act | 0.0 to 1.0 | Normally distributed, mean 0.5, std. dev. 0.25. |
| Violence Threshold | Individual / Each Civilian | Level that anger must pass for civilian to be willing to engage in violent insurgency | 0.0 to 1.0 | Normally distributed, mean 0.5, std. dev. 0.25. |
| Anger Increment per Injury | Global | Amount per injured civilian that anger increases in each civilian injured by a soldier counterattack | 0+ | 0.05 |
| Fear Increment | Global | Amount that fear increases in each civilian injured by a soldier counterattack | 0+ | 0.10 |
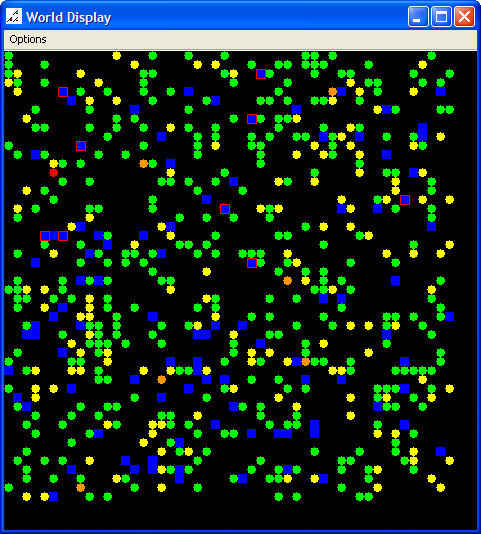 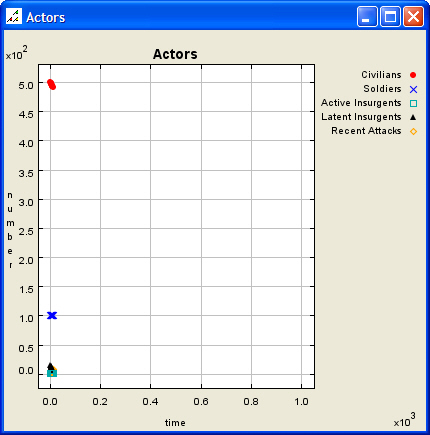
|
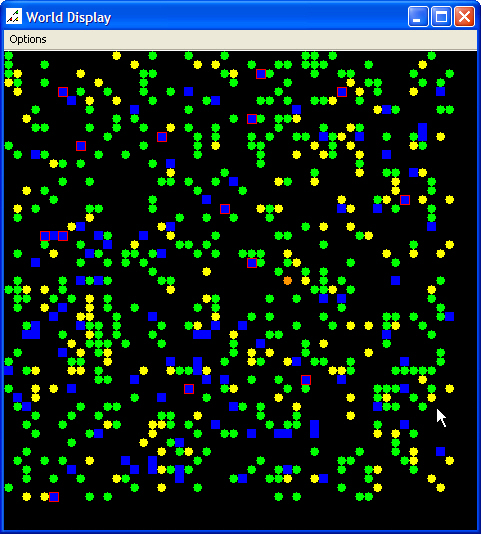
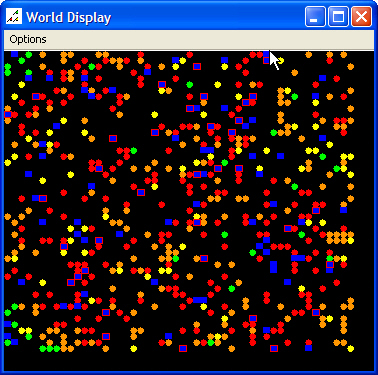
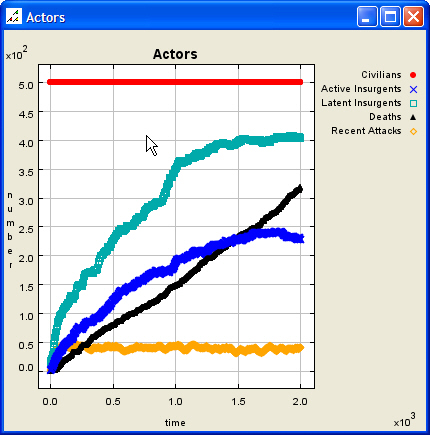
| Figure 2. Initial Scenario Map and Data Graph |
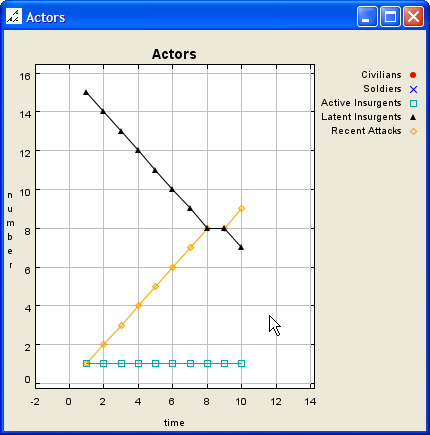
|
| Figure 3. Initial Scenario Data Graph, Expanded |
 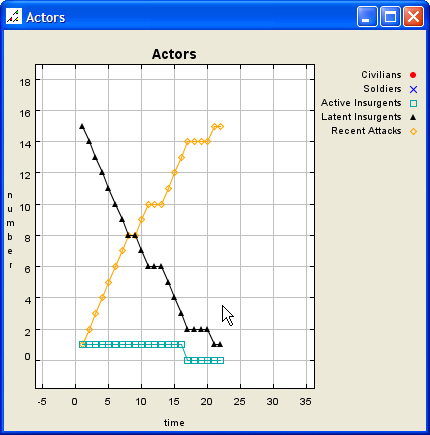
|
| Figure 4. Initial Scenario Map and Data Graph, After Termination |
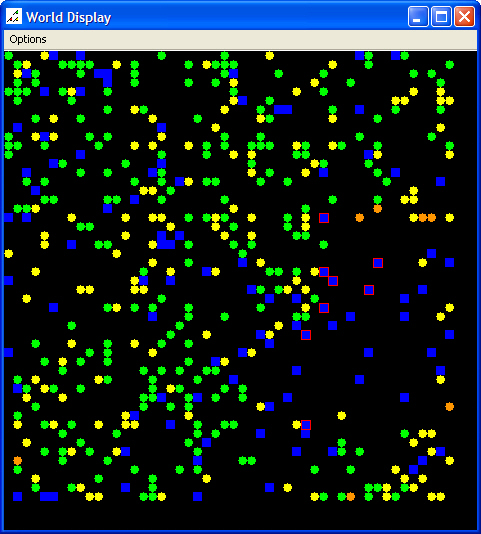 
|
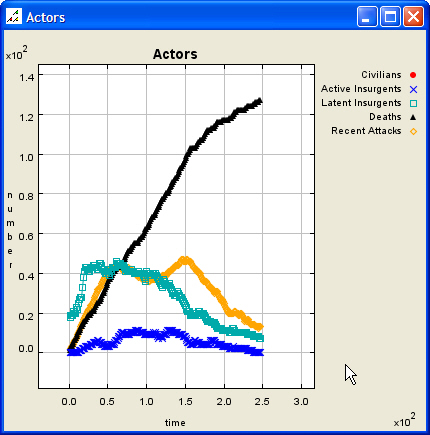
| Figure 5. High Effectiveness, Low Accuracy Scenario, After Termination |
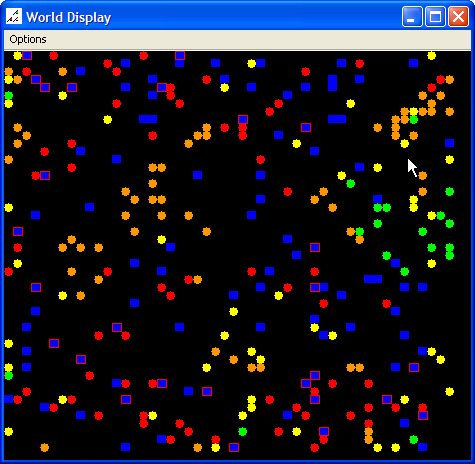 
|
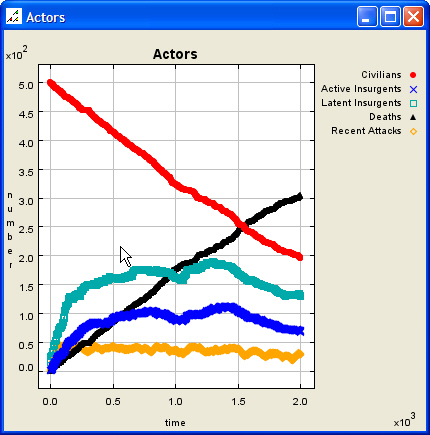
| Figure 6. Low Effectiveness, Low Accuracy Scenario, After Termination |
|
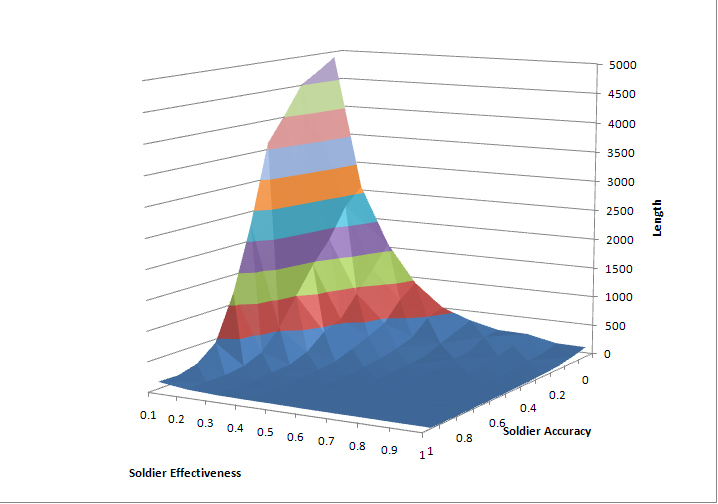
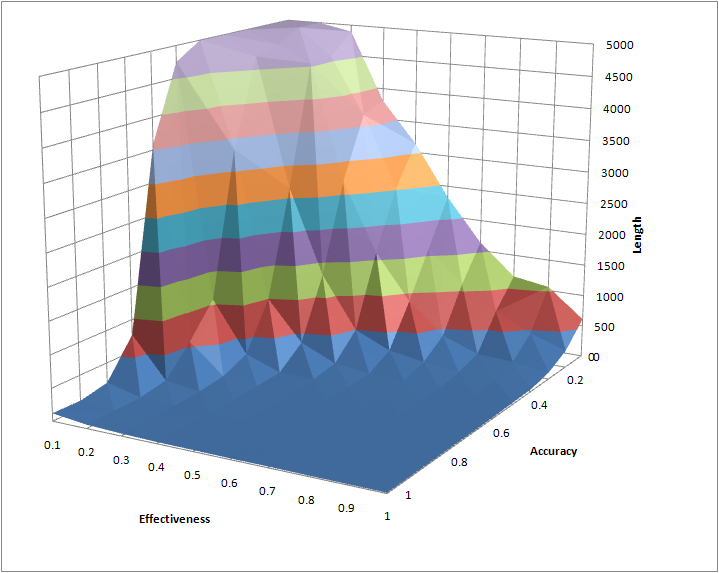
| Figure 7. Average Time to Simulation Termination, Varying Accuracy and Effectiveness, 25 Runs per Combination |
|
| Figure 8. Scenario with Replacement, No Neighborhood Influence |
|
| Figure 9. Time to Simulation Termination, Varying Accuracy and Effectiveness, Simulations with Replacement and No Neighborhood Influence, Average of 25 Runs per Combination |
|
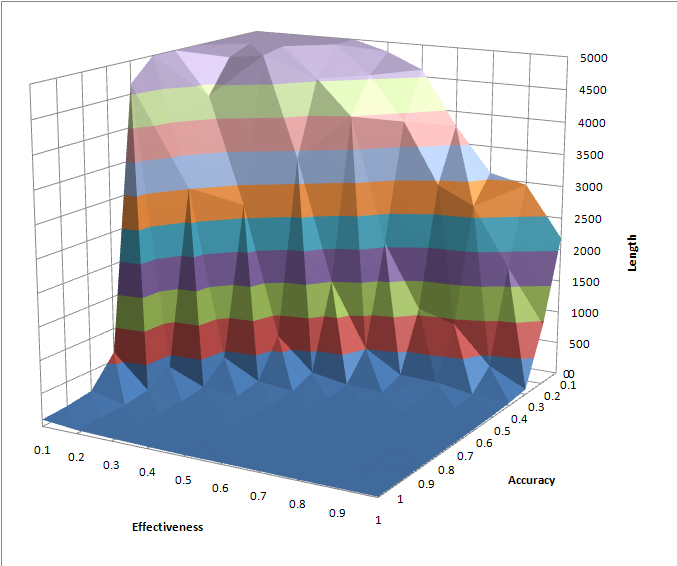
| Figure 10. Time to Simulation Termination, Varying Accuracy and Effectiveness, Simulations with Replacement and Neighborhood Influence, Average of 25 Runs per Combination |
2 It is generally accepted that it is easier to motivate civilians to oppose occupying forces or a government seen as a puppet rather than a legitimate indigenous government and its forces (e.g. Metz and Millen 2004). In the model developed here, the difference in these situations is easily captured by increasing the baseline level of anger among civilians (discussed below), and so differences will be explored in the sensitivity analysis. This higher level of anger at an occupying or puppet government would not require changes to the dynamics of the model, however.
3 A different model could be developed to focus on the dynamics of final national government defeat by insurgents. That model would likely be quite different, with quite different dynamics of government defeat at play. This later stage of an insurgency, specifically after it reaches the point of being self-sustaining, is not the focus of the model here.
4 The simulation parameterizes this probability of response to allow future exploration of a possible optimal response strategy for a government dealing with insurgents that might include only partial or occasional responses to attacks.
5 While it is easiest to think of “injury” as literal injury (injured civilians) in the case of collateral damage in conflict situations, in other circumstances the “injury” that civilians react to could be property damage, individual disruption (being forced from homes, searched), or neighborhood disruption (setup of checkpoints, vehicle searches). All of these actions might inflame anger at the soldiers undertaking the actions.
6 In the versions of the simulation presented here, only the fear and anger of those civilians actually injured in a counterattack are updated. In a variant, everyone in the neighborhood (that is, within the “interaction range” of the targeted insurgent) has their fear and anger updated. The main effects of the simulation and the effectiveness/accuracy relationships are not substantially affected by this change.
7 In every combination, the standard deviation of length over the 25 runs is smaller than the mean, typically between 25% and 50% of the mean length. The s.d. is typically smaller in runs at the “edges” of the space, that is, where accuracy or effectiveness are close to 0 or 1. There is thus a good bit of variation within the runs, but not enough to conceal a clear trend in the mean. More runs do not appreciably change the shape of the figures displayed here. The author's website includes a spreadsheet listing the mean and standard deviation of the 25 runs at each combination of accuracy and effectiveness, and computing 75% and 89% bounds for the mean based on the Chebyshev inequality.
BAPAT, Navin (2005) Insurgency and the Opening of Peace Processes. Journal of Peace Research 42: 699-717.
BENNETT, D. Scott (2008a) Recruiting Your Way to Victory: Varying Strategies in Insurgent/Counterinsurgent Warfare. Paper presented at the annual meeting of the Midwest Political Science Association, Chicago, IL, April 5, 2008.
BENNETT, D. Scott (2008b) Being Your Own Worst Enemy, and Learning to Win: A Model of Government Learning in Responding to Insurgency. Manuscript.
BHAVNANI, Ravi, Dan Miodownik, and Jonas Nart (2008) REsCape: An Agent-Based Framework for Modeling Resources, Ethnicity, and Conflict. Journal of Artificial Societies and Social Simulation (11: 27). https://www.jasss.org/11/2/7.html.
CEDERMAN, Lars-Erik (2006) Articulating the Geo-Cultural Logic of Nationalist Insurgency. In Kalyvas, Stathis, and Iain Shapiro, eds., Order, Conflict, and Violence. Cambridge: Cambridge University Press.
CHATURVEDI, A. R., D. Dolk, R Chaturvedi, M. Mulpuri, D. Lengacher, S. Mellema, P. Poddar, C. Foong, and B. Armstrong (2005) Understanding Insurgency by Using Agent-Based Computational Experimentation: Case Study of Indonesia." Proceedings of the Agent 2005 Conference on Generative Social Processes, Models, and Mechanisms.
CUI, Xiaohui, and Thomas E. Potok (2007) A Particle Swarm Social Model for Multi-Agent Based Insurgency Warfare Simulation. Software Engineering Research, Management & Applications, 2007: 177-183.
DORAN, Jim (2005) Iruba: An Agent-Based Model of the Guerrilla War Process. In Klaus Troitzsch, ed. Representing Social Reality: Pre-Proceedings of the Third Conference of the European Social Simulation Association, Koblenz, September 5-9, 2005. Germany: Verlag Dietmar Fölbach, pp. 198-205.
EPSTEIN, Joshua M., John D. Steinbruner, Miles T. Parker (2001) Modeling Civil Violence: An Agent-Based Computational Approach. Center on Social and Economic Dynamics, Brookings Institution, Working Paper No. 20, January 2001.
FEARON, James D. and David D. Laitin (2003) Ethnicity, Insurgency, and Civil War. American Political Science Review 97:75-90.
FINDLEY, Michael G., and Joseph K. Young (2007) Fighting Fire with Fire? How (Not) to Neutralize an Insurgency. Civil Wars 9(4): 378-401.
GALULA, David (2006) Counterinsurgency Warfare: Theory and Practice. Westport, CT: Praeger Security International. Originally published 1964.
HENDRICKSON, David C., and Robert W. Tucker (2005) Revisions in Need of Revising: What Went Wrong in the Iraq War. Carlisle, PA: Strategic Studies Institute of the U.S. Army War College.
LOUIE, Marcus A., and Kathleen M. Carley (2007) The Role of Dynamic-Network Multi-Agent Models of Socio-Political Systems in Policy. Manuscript.
MANWARING, Max (2004) Shadows of Things Past and Images of the Future: Lessons for the Insurgencies in our Midst. Carlisle, PA: Strategic Studies Institute of the U.S. Army War College.
METZ, Steven, and Raymond Millen (2004) Insurgency and Counterinsurgency in the 21st Century. Carlisle, PA: Strategic Studies Institute of the U.S. Army War College.
MILITARY Operations Research Society (2006) MORS Workshop Report: Agent-Based Models and Other Analytic Tools in Support of Stability Operations. Unclassified Research Report for MORS Workshop, October 25-27, 2005.
NAGL, John A (2005) Learning to Eat Soup with a Knife: Counterinsurgency Lessons from Malaya and Vietnam. Chicago: Chicago.
O'NEILL, Bard E(2005) Insurgency & Terrorism. Washington: Potomac Books.
RECORD, Jeffrey, and W. Andrew Terrill (2004) Iraq and Vietnam: Differences, Similarities, and Insights. Carlisle, PA: Strategic Studies Institute of the U.S. Army War College.
RUBY, Keven, David L. Sallach, Charles M. Macal, Veena S. Mellarkod, Alexander Wendt (2005) Occupation Dynamics: Contesting Hearts and Minds. Proceedings of the North American Association for Computational Social and Organizational Science, June 26-28, 2005.
SMALL, Melvin, and J. David Singer (1982) Resort to Arms: International and Civil Wars, 1816-1980. Beverly Hills, Calif.: Sage Publications.
UNITED STATES DEPARTMENT OF THE ARMY (2007) The U.S. Army/Marine Corps Counterinsurgency Field Manual. Chicago: University of Chicago.
WARREN, T. Camber (2006) Communication, Coordination, and Conflict: An Agent-Based Model of Loyalty Fragmentation. Paper presented at the Annual Meeting of the American Political Science Association, August 31-September 3, 2006.
WHEELER, Scott (2005) It Pays to Be Popular: a Study of Civilian Assistance and Guerilla Warfare. Journal of Artificial Societies and Social Simulation 8(4) https://www.jasss.org/8/4/9.html.
WIMBERLEY, Scott (1997) Special Forces Guerrilla Warfare Manual. Boulder: Paladin Press.
Return to Contents of this issue
© Copyright Journal of Artificial Societies and Social Simulation, [2008]