Stanislaw Raczynski (2004)
Simulation of The Dynamic Interactions Between Terror and Anti-Terror Organizational Structures
Journal of Artificial Societies and Social Simulation
vol. 7, no. 2
<https://www.jasss.org/7/2/8.html>
To cite articles published in the Journal of Artificial Societies and Social Simulation, reference the above information and include paragraph numbers if necessary
Received: 12-Dec-2003 Accepted: 17-Mar-2004 Published: 31-Mar-2004
 Abstract
Abstract

|
| Figure 1. Graphical symbols |
|
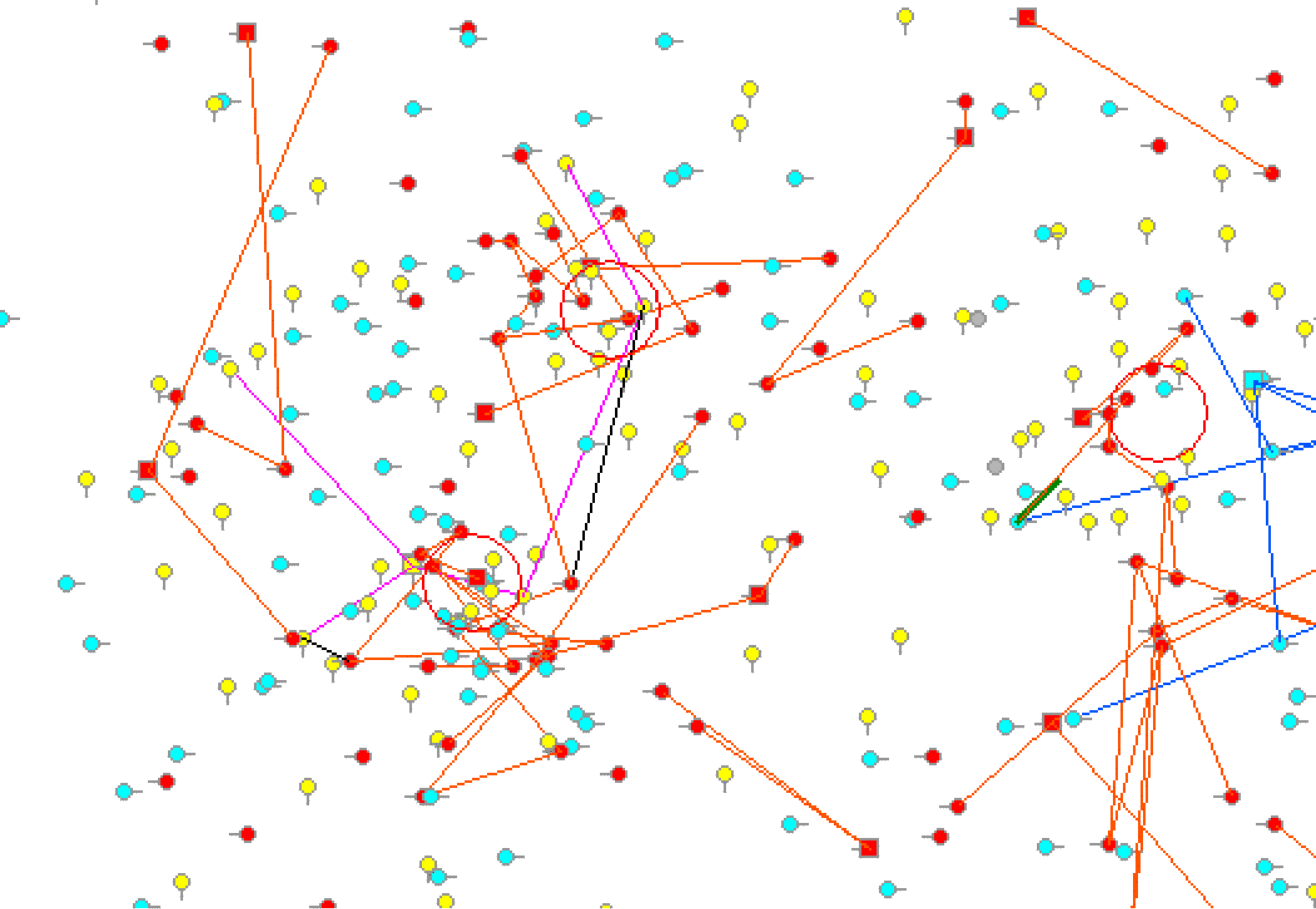
| Figure 2. A screen shot of an early stage in the model run |
|
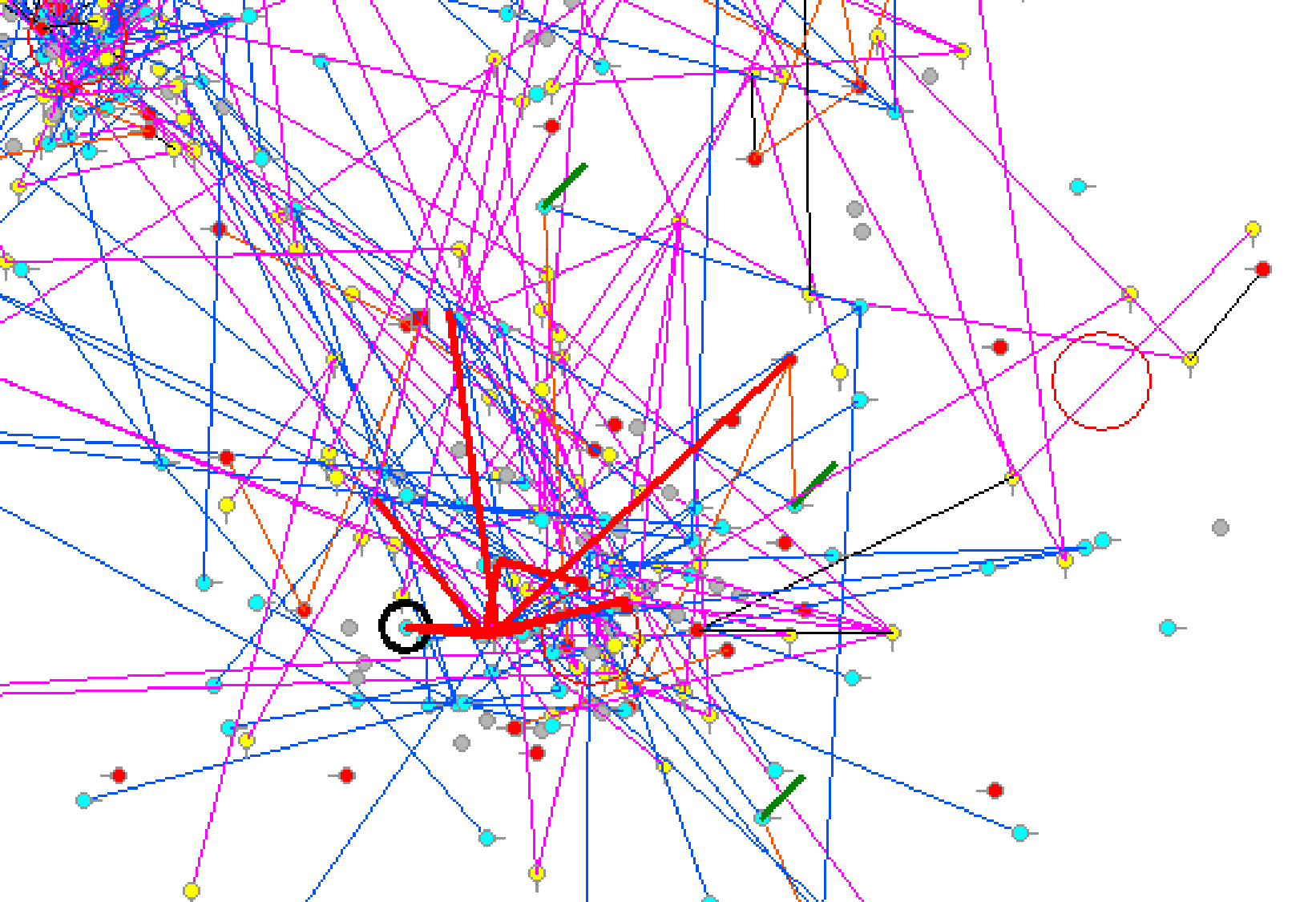
| Figure 3. Destroying a terrorist organization. Bold lines show links being destroyed |
|
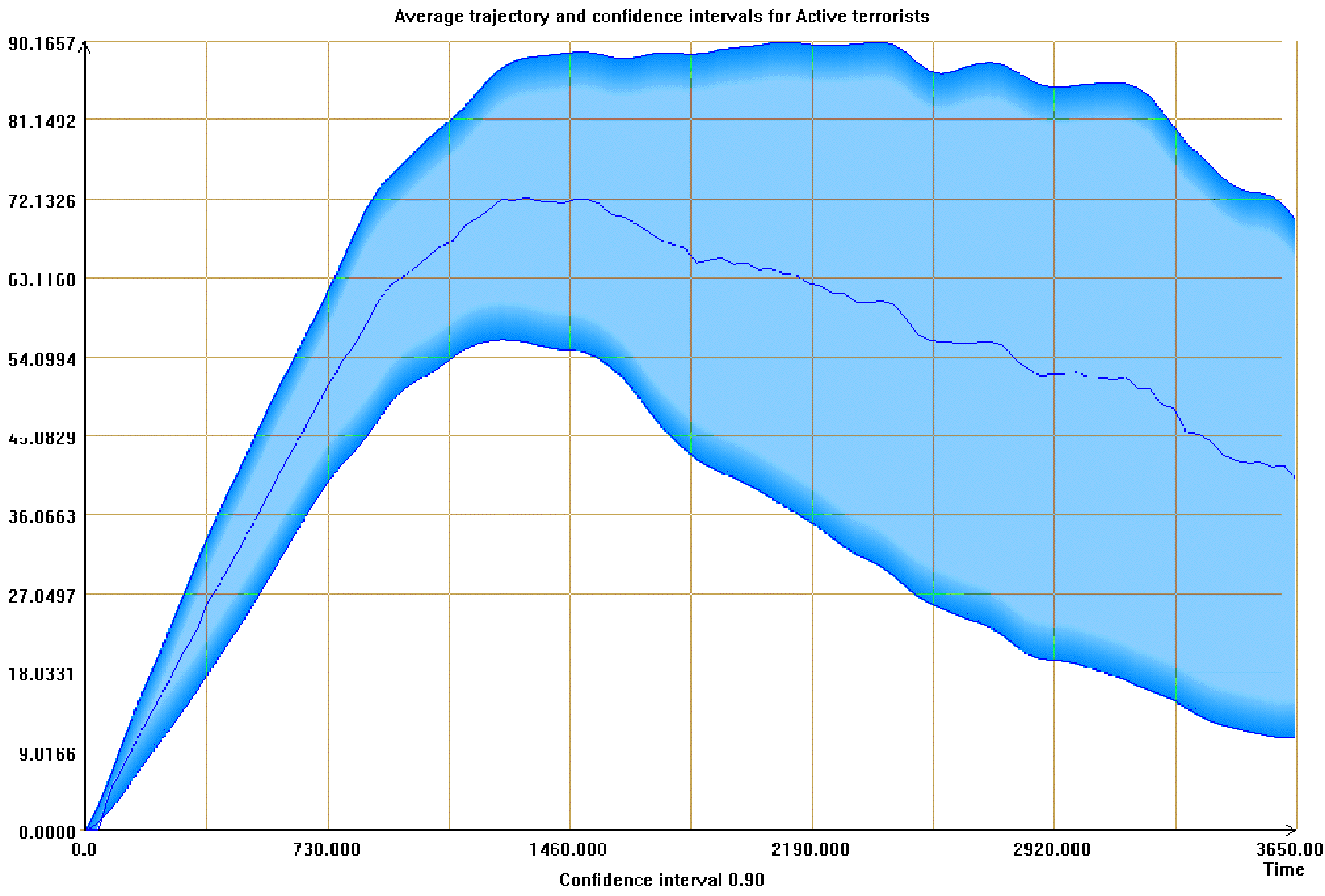
| Figure 4. Average and confidence intervals for the number of active terrorists. Terrorist-supporting structure enabled |
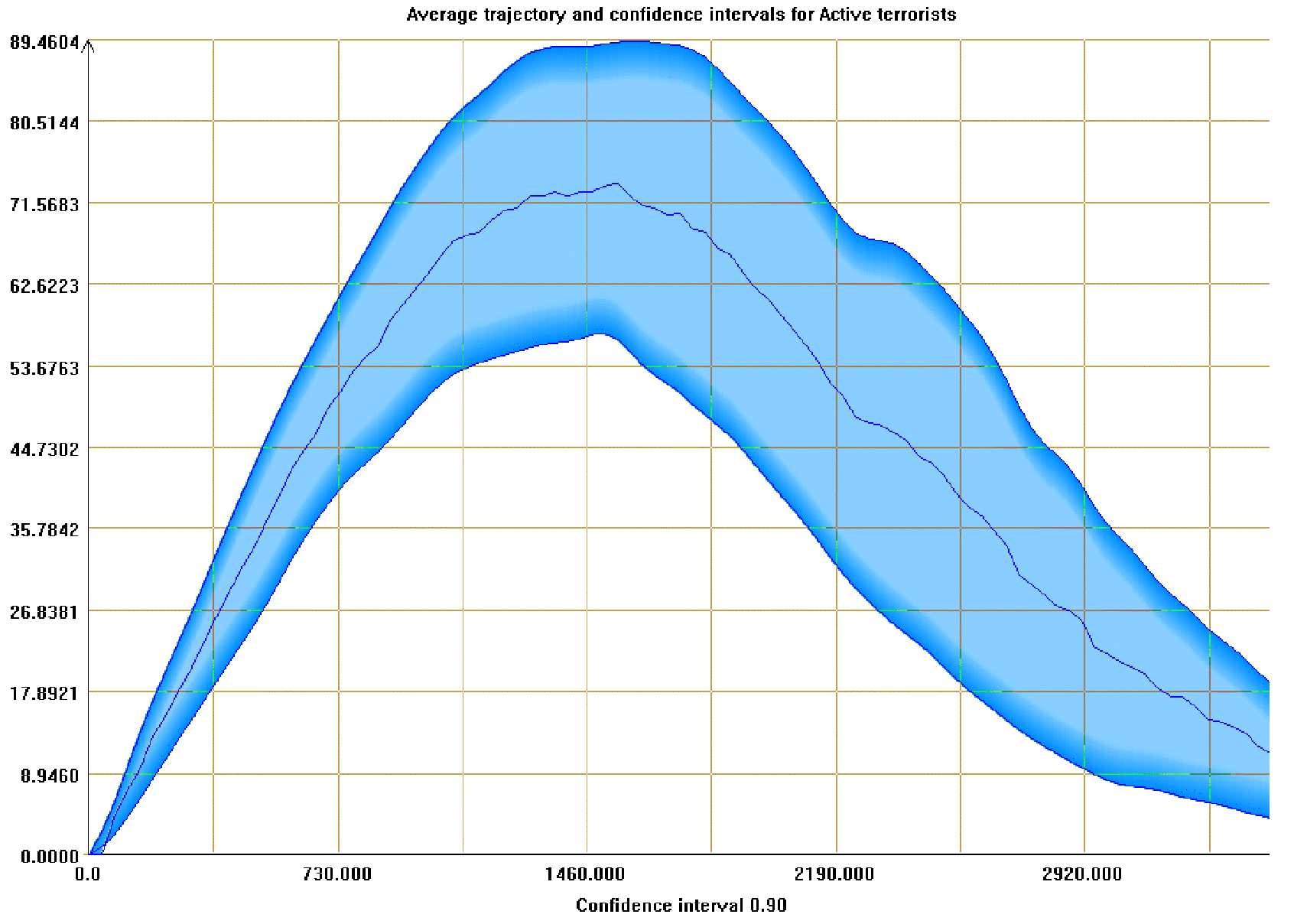
|
| Figure 5. Average and confidence intervals for the number of active terrorists. Terrorist-supporting structure disabled |
|
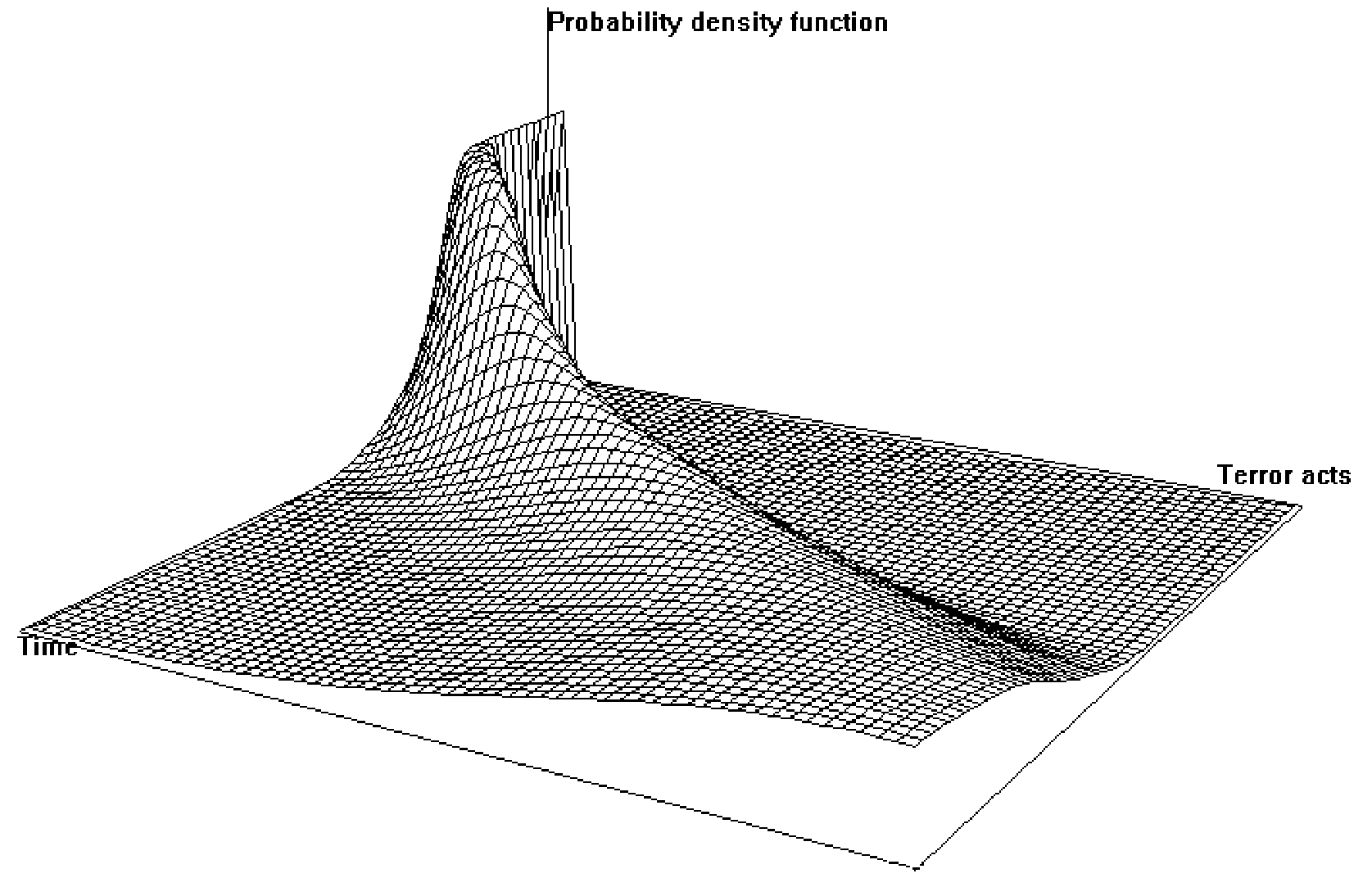
| Figure 6. 3D image of the probability density function for terrorist acts. Terrorist-supporting structure enabled |
|
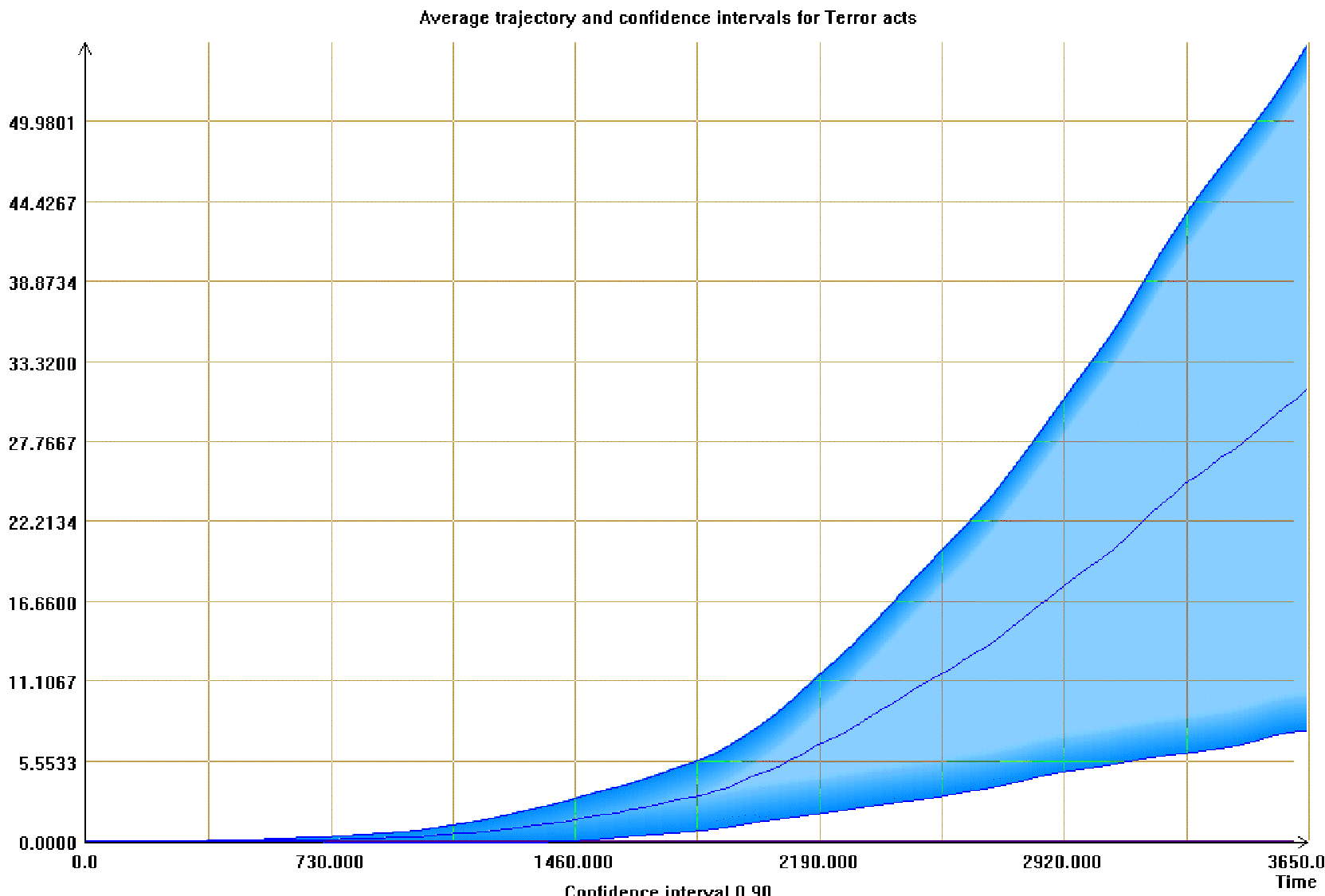
| Figure 7. Average and confidence intervals for the number of terrorist acts. Terrorist-supporting structure enabled |
BAK, Per (1997) How Nature Works: The Science of Self-Organized Criticality. Oxford: University Press.
CIOFFI-REVILLA C., 1998, Politics and Uncertainty: Theory, Models and Applications, Cambridge: Cambridge University Press.
CHATTERJEE ,S., Seneta E., 1977, Towards consensus: some convergence theorems on repeated averaging. Journal of Applied Probability, 14, pp.89-97.
COHEN J., Kejnal J. and Newman C., 1986, Approaching Consensus Can Be Delicate When Positions Harden. Stochastic Processes and their Applications, 22, pp.315-322.
DEFFUANT G., Amblard F., Weisbuch G. and Faure T., 2002, How Can Extremism Prevail? A Study Based on the Relative Agreement Interaction Model. Journal of Artificial Societies and Social Simulation, vol.5, no.4. https://www.jasss.org/5/4/1.html
EPSTEIN J.M., Axtell R., 1996, Growing Artificial Societies: Social Science from the Bottom Up, Brookings Institution Press, Washington D.C.
GALAM S., Wonczak S., 2000, Dictatorship from Majority Rule Voting. European Physical Journal B, 18, pp.183-186.
GOTTS N.M., Polhill J.G. and Law A.N.R., 2003, Agent-Based Simulation in the Study of Social Dilemmas, Artificial Intelligence Review 19(1), pp.3-92.
HOLLAND J.H., 1998, Emergence: From Chaos to Order, Massachusetts: Helix Books: Addison-Wesley Publishing Company.
KRAUSE U., 2000, A Discrete Nonlinear and Non-Autonomous Model of Consensus Formation. In: Elaydi S., Ladas G., Popenda J and Rakowski, Communications in Difference Equations, Amsterdam, Gordon and Breach, pp.227-236.
LATANE B., Nowak A., 1997, Self-Organizing Social Systems: Necessary and Sufficient Conditions for the Emergence of Clustering, Consolidation and Continuing Diversity. In Barnett F.J. and Boster F.J., Progress in Communication Sciences, Ablex Publishing Corporation, pp.1-24.
LONG J.E., Systems Analysis: A Tool to Understand and Predict Terrorist Activities, Vitech Corporation. http://www.seecforum.unisa.edu.au/Sete2002/ProceedingsDocs/62S-Long-INTEL.pdf
LUSTICK S., 2000, Agent-Based Modeling of Collective Identity, Journal of Artificial Societies and Social Simulation, vol.3, no.1. https://www.jasss.org/3/1/1.html
MACY M.W., Willer W., 2002, From Factors to Actors: Computational Sociology and Agent-Based Modeling, Annual Review of Sociology , 28, pp.143-166.
RACZYNSKI, S, 1980, Simulation of Interaction Between Certain Hierarchical Structures, Proceedings of the conference "Simulation of Large Systems", Universitat Bielefeld, Bielefeld, 1980.
RACZYNSKI, S, 1988, Process Hierarchy and Inheritance in PASION, Simulation 50(6), June 1988.
RACZYNSKI, S, 2003, Continuous Simulation, a Chapter in Encyclopedia of Information Systems, Academic Press, Elsevier Publ.,.
SMITH, Roger, 2002, Counter Terrorism Simulation: A New Breed of Federation, Simulation Interoperability Workshop, Orlando, Florida, Spring 2002
SMITH, Roger, 2001, Modeling and Simulation Adds Insight on Terrorism, Signal Magazine, December 2001. Armed forces Communications and Electronics Association (AFCEA).
YOUNGER S, M. 2003, Discrete Agent Simulations of the Effect of Simple Social Structures on the Benefits of Resource Sharing, Journal of Artificial Societies and Social Simulation, vol.6, no.3. https://www.jasss.org/6/3/1.html
ZEIGLER B.P., 1976, Theory of Modeling and Simulation, Wiley-Interscience, New York, 1976.
Return to Contents of this issue
© Copyright Journal of Artificial Societies and Social Simulation, [2004]