Introduction
As the United States continues to find itself engaged in military action against non-state actors in places such as Afghanistan and Syria, understanding the effectiveness of alternative strategies available to insurgents and counterinsurgents remains an important area of study. Policymakers (Guide to the Analysis of Insurgency 2012; Nagl 2002; Petraeus 2006; Sepp 2005; US Army Field Manual 3-24 2006, 1-11) and academics (Berman, Shapiro and Felter 2011; Berman et al. 2013; Galula 2006) agree that a government's peaceful interaction with the population is critical in defeating insurgency. Such observers fear that governments can be their own worst enemies when they use violence indiscriminately to try to defeat an insurgency. The advocates of a more peaceful approach emphasize that providing security and aid to the population will increase the support of communities for the government rather than insurgents. But while governments may understand that providing aid to a population in order to sway popular sentiment is a good idea, doing so may be expensive and difficult under violent conditions. And in practice, even proponents of an aid strategy acknowledge that some military action to stop insurgents will be necessary when those insurgents are engaging in effective violence. The US government explicitly notes that both military and economic means will be necessary to defeat insurgency (US Army Field Manual 3-24 2006, 1-11). However, while we understand that states must mix aid and military strategies, it is less well-understood how different mixtures of these strategies might succeed or fail at defeating an insurgency. If establishing security and providing public goods are both important in defeating an insurgency, then what is their relative contribution to achieving the desired outcome for the government? In practical terms, how should states allocate their finite resources when designing counterinsurgency campaigns?
Two findings in the counterinsurgency literature suggest desired elements of a successful counterinsurgency strategy. First, counterinsurgency campaigns that target civilians indiscriminately increase support for insurgency among civilians (e.g., Condra and Shapiro 2012). Second, small-budget, well-designed, local aid programs that improve civilians’ lives increase support for the state among civilians (e.g., Berman et al. 2013).[1] Based on these findings, a reasonable counterinsurgency campaign would avoid targeting civilians and would provide aid to civilians. Governments frequently face constraints on the total resources available for providing aid or for developing precisely-targeted military campaigns. This leads us to ask: what is an effective balance between these approaches? Could sufficient investment in one strategy overcome the lack of investment in another strategy? And in particular, this paper asks whether it is possible for a state to use well-designed local aid programs to compensate for a military strategy that targets civilians.
One cannot draw a direct comparison between the military and aid approaches from observational data, because the availability of sample data is not sufficient to support a parametric analysis. We thus employ a computational model to evaluate the relative contribution of these approaches to ending insurgency, using Bennett’s (2008) computational model of early stages of insurgency as a starting point. Given the focus on the early stages of insurgency, most civilians are initially undecided about supporting insurgents. The insurgents’ goal is to grow the insurgency and the state goal is to defeat it. Rebels succeed if an insurgency survives to become established. The model conceptualizes insurgency as irregular warfare, a situation in which the rebels are weaker than the government in the beginning of the conflict and engage in sporadic attacks rather than a sustained conventional military campaign (Kalyvas and Barcells 2010, 418). Bennett (2008) tracks how civilians react to soldiers employing military tactics of various designs against insurgents. In particular, his model focuses on how soldiers’ ability to avoid harming bystanders and to capture targeted insurgents contribute to the overall state mission of defeating a rebellion (Bennett 2008, 1.6). The simulation establishes that soldiers, who capture targets and avoid collateral damage at least 40% of the time, defeat nascent insurgencies rapidly. By contrast, if soldiers capture targets and avoid collateral damage 30% of the time or less, an insurgency spreads across the population and, in some cases, becomes sustainable. The model illustrates how militaries alienate civilians, inadvertently helping the rebellion, if they injure civilians and/or fail to capture targets.[2]
Since Bennett’s (2008) model explores the effects of the military approach, it may not answer the questions posed in this project. We thus extend Bennett’s (2008) model by allowing both state and insurgent actors to use aid in addition to military means. In our model, individual soldiers and insurgents may provide aid to civilians as an alternative to attacking their opponents. We then trace how civilians react to the interaction of state and insurgent actors employing military tactics against each other and providing aid to civilians. Our model yields that aid may boost a military strategy that avoids civilian casualties, but it may not compensate for a military strategy that targets civilians indiscriminately, emphasizing the paramount importance of a military approach that relies on intelligence and avoids civilian casualties.
Two Broad Approaches to Counterinsurgency
Counterinsurgency (COIN) includes military, paramilitary, political, economic, psychological, and civic actions by a government designed to defeat an armed movement by a nonstate opponent aimed at the overthrow or territorial change of an incumbent government (US Army Field Manual 3-24 2006, 1-1). Military and paramilitary means may be viewed as a direct approach that aims to physically eliminate or neutralize the rebels (Nagl 2002). We refer to this as the military approach to counterinsurgency. In contrast, political, economic, psychological, and civic measures may be grouped together as an indirect approach designed to improve the welfare of civilians beyond security concerns, thus winning their hearts and minds and turning civilians away from the insurgency (Nagl 2002). We label this as the aid approach.
What is the military approach? The military strategy relies on “stick” operations of violence, e.g., detention and elimination of individual insurgents, disruption of insurgent support networks, and decapitation of insurgent organizations (U.S. Government Counterinsurgency Guide 2009, 14-15). It is a kinetic component of a government’s response to guerrilla warfare.[3]
The military approach may be carried out using either selective or indiscriminate violence, which have opposite effects on the dynamics of insurgency. Selective state violence punishes based on individual behavior, targeting only rebels or individuals who aided rebellion. Intuitively, such violence has a suppressive effect on insurgency, as it makes participation in rebellion costlier relative to neutrality or loyalty to the state. The use of selective violence thus deters civilians from joining or aiding the rebellion (Kalyvas 2006).
In contrast, indiscriminate state violence punishes civilians based on their affiliation with a group, e.g., their village or ethnic group, regardless of whether individuals took up arms or assisted rebels in any way. Indiscriminate violence makes loyalty to the state costly, sometimes even costlier than neutrality, which means it effectively encourages civilians to join the rebellion (Kalyvas and Kocher 2007). Even when civilians do not join the rebels they can assist them by providing or withholding information from the government about the rebels. In particular, when civilians are aggrieved at the government because of indiscriminate state violence, they are more likely to withhold private information about the rebels from the government, thus preventing the government from using selective violence. This leads to further growth of the insurgency (Berman, Shapiro and Felter 2011, Condra and Shapiro 2012). Empirically, this logic has been supported by multiple studies, and practitioners of COIN have also recognized the importance of avoiding state indiscriminate violence (Headquarters, Department of the Army 2006; Petraeus 2006; Sepp 2005).[4]
Given the counterproductive effect of indiscriminate violence, it is puzzling why states use it. Possible reasons include lack of intelligence (Kalyvas 2006), bad discipline (Humphreys and Weinstein 2008), or its ability to drive a wedge between insurgents and civilians (Lyall 2009). We do not focus on the reasons why a government chooses to use indiscriminate or selective violence, leaving these decisions exogenous in our model, instead focusing on the consequences of these decisions.
Following Bennett (2008), we model both selective and indiscriminate types of violence. The military strategy has two features: (i) state soldiers’ ability to identify and capture the target, i.e., intelligence about who the insurgents are and ability to remove insurgents from the population (effectiveness), and (ii) the extent of collateral damage if any, i.e., how many civilians are hurt during the operation (accuracy). Thus, following Bennett (2008), our model may represent a range of military approaches from pure indiscriminate violence to pure selective violence.
What is the aid approach? An aid strategy relies on “carrot” operations to persuade civilians to support the central government by delivering political, economic, and development benefits that come in the form of direct aid, employment, medical care, infrastructure, and other non-violent projects (U.S. Government Counterinsurgency Guide 2009, 14-15). We use “aid” as a short cut to describe any services provided to civilians aimed at improving their welfare.
Not every aid program is created equal. Some programs increase support and cooperation from civilians, which in turn allows the government to decrease insurgent attacks. Other programs seem to have no impact on insurgency dynamics. For instance, in the Iraq war, scholars compared the large-scale infrastructure building projects managed by USAID and small-scale programs managed by battalion commanders designed to provide local public goods. They concluded that small-budget programs designed to address specific local needs of communities were more effective at increasing civilians’ support and cooperation than large-budget programs that were attempting to affect change beyond one local district (Berman, Shapiro and Felter 2011; Berman et al. 2013). Intuitively, among small-budget programs, those designed by groups of specialists with diplomatic, reconstruction, and military expertise were more effective at garnering civilians’ cooperation than programs designed without expert input (Berman et al. 2013).
Given these results, we do not focus on global aid programs that could theoretically improve the welfare of the entire civilian population in our model. Instead, we model localized effects of the aid approach. Since some local programs may be designed without any expert feedback, we allow for the effects of the aid strategy to vary with respect to the number of civilians recruited at a time and the intensity with which civilians’ attitudes change.[5] The state aid approach varies across two dimensions in our model: (i) the number of civilians affected by an interaction and (ii) the intensity of change in the affected civilians’ attitudes. As a result, a well-designed small-scale program would increase the approval of the government among more civilians than a poorly-designed program.
Insurgents may also use non-violent recruitment strategies to increase their ranks of fighters and their support among civilians. Sometimes, insurgent organizations fill the void of governance and provide both public goods and law enforcement services to the population. For instance, Al-Qaeda in the Arabian Peninsula distributed water to families in Southern Abyan during summer heat, installed electric lines to communities that never had electricity before, and helped carry out investigations about stolen property (Johnsen 2014, 279). In other cases, insurgent organizations invest less in communities, instead seeking new recruits through individual monetary benefits or emphasis on one’s group identity. For instance, the Taliban has focused its recruitment efforts on providing attractive salary packages combined with appealing to Pashtunwali cultural notions of honor (European Asylum Support Office 2012). To use Olson’s (1993) terminology, in our model, both the state and the insurgents are acting partially as “stationary bandits” as we model the struggle between the two political organizations to increase their territorial control over a given locality. It thus makes sense for insurgents as well as the state soldiers to provide some services to the population and avoid stealing 100% of the civilians’ profits to extract greater returns in the longer term.
In short, both sides of the conflict use non-violent means to win the approval of the population, eventually controlling it. While no empirical work has systematically studied the quality of insurgent use of the aid strategy, we assume that some efforts of the rebels’ non-violent methods of recruitment work better than others. Thus, we model the quality of the rebel aid approach as varying across the same dimensions as the government aid: the number of civilians affected by an interaction and the intensity of change of civilians’ attitudes.
Why model these two approaches simultaneously? Recent empirical work in the counterinsurgency literature has concluded that it is the synergy between a government’s aid and military strategies that is key to suppressing an insurgency (Berman et al. 2013). In other words, we should expect that a combination of the military action that targets insurgents without harming civilians and small-scale aid programs that address a specific local need will have a better chance at defeating an insurgency than state efforts that harm civilians and employ large-scale projects that bypass local community needs. It is less clear how different mixtures of these strategies might succeed or fail at defeating an insurgency. If the military and aid approaches are both important, then what is their relative contribution to achieving the desired outcome for the government? The use of a computational model allows us to compare various combinations of strategies by insurgents and counterinsurgents and determine which approach plays a more important role in defeating an insurgency.
Our model does not represent counterinsurgency comprehensively. Rather, following Epstein (2008), it illuminates one element of this phenomenon, the relative contribution of non-violent and violent methods to the success of counterinsurgency. Previous models captured the relative weight of selective vs. indiscriminate targeting of insurgents (e.g., Kress and MacKay 2014; Bennett 2008) and considered the use of violent vs. non-violent methods of counterinsurgency in concert (e.g., Findley and Young 2007; Caulkins et al. 2008; and Kress and Szechtman 2009). Our model contributes to this line of research by allowing counterinsurgents to use various combinations of the military and aid approach by also focusing on the specific features of each approach.
The Model
Our model expands Bennett’s (2008) model of early stages of insurgency. We chose Bennett’s (2008) model as a starting point because he allows for a full range of military strategies from highly indiscriminate to highly selective. Bennett (2008) omits the aid strategy altogether, a gap that we fill. See Figure 1 for a graphical representation of how our model differs from Bennett’s (2008). The complete pseudo code is included in the Appendix.[6] The model parameters and their default values are listed in Table 1.
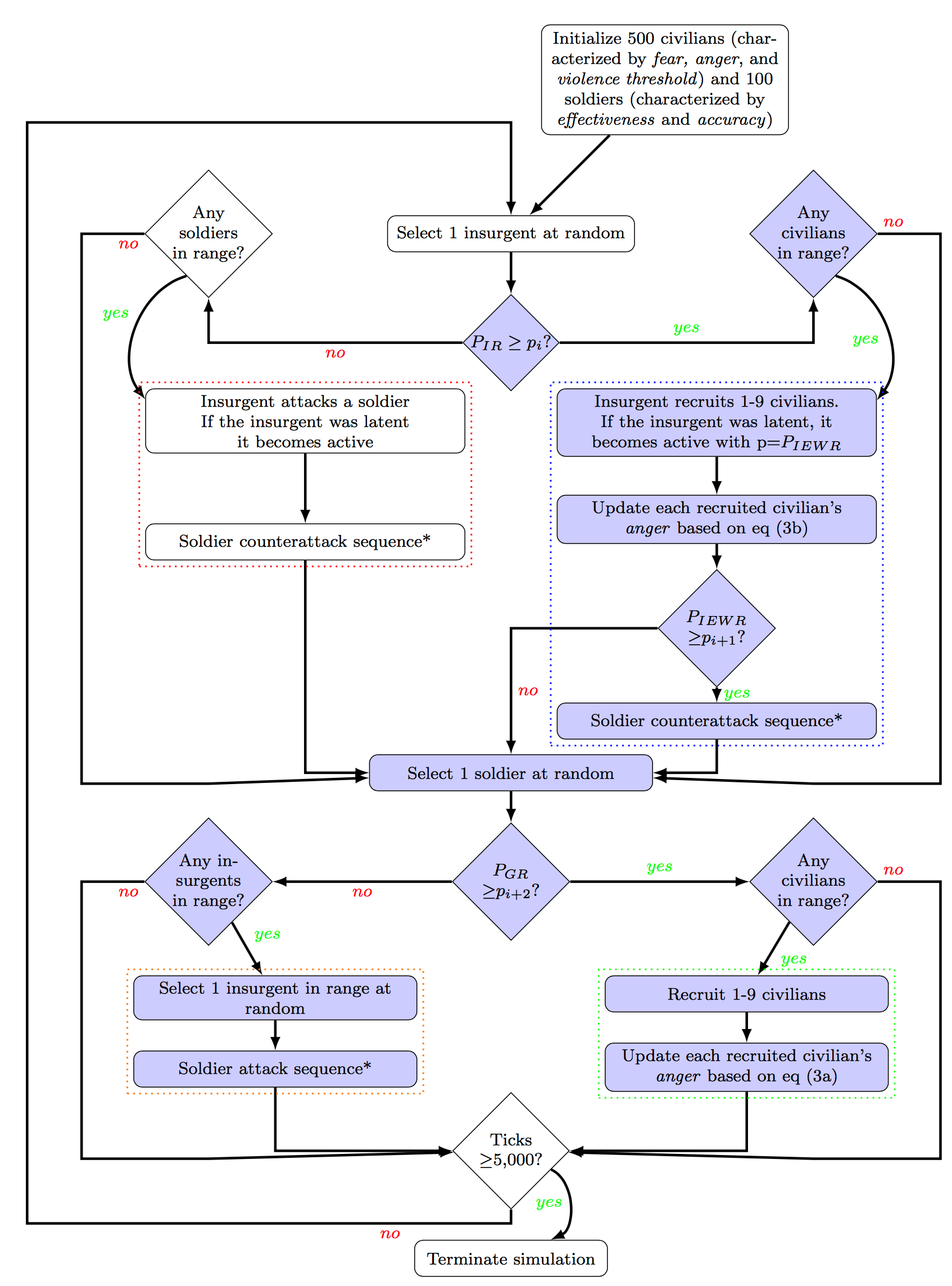
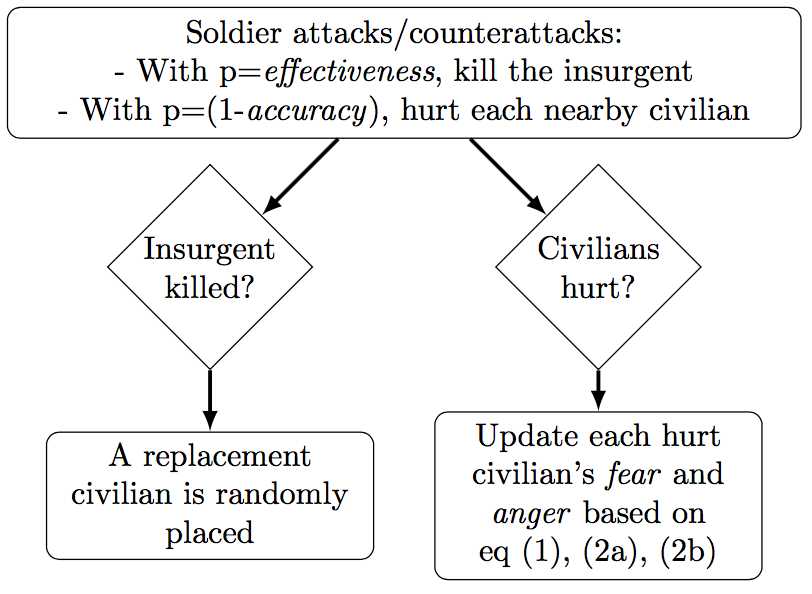
Time: In the course of each simulation model run, the interactions among agents (the actors in the model) may develop into a defeat of insurgency (all insurgents are removed which terminates the run) or a sustained insurgency (if the simulation reaches 5,000 ticks, it terminates the run). The sequence within each tick is described in the following subsections and is represented graphically in Figure 1. Each tick includes an action sequence by a randomly selected insurgent, followed by an action sequence by a randomly selected soldier. A selected insurgent probabilistically decides between attacking a soldier, which always triggers a counterattack by a soldier, and peacefully recruiting civilians, which probabilistically triggers a counterattack by a soldier. Then, during state turn, a selected soldier probabilistically decides between attacking an insurgent and peacefully recruiting civilians (providing aid). One may think of a model’s tick as an hour or perhaps a day. While time units are not defined in this model, it makes sense to think of a tick as a rather short period of time.
Agents: The model assumes two core types of agents: civilians, who may become rebels/insurgents, and soldiers, who never change their identity. We make no assumptions about social groupings among civilians, continuing to rely on “light’’ agents, as Bennett (2008) does.
Civilians represent the bulk of a population. Individual civilians are characterized by a degree of anger at the government, a degree of fear of the government, and a violence threshold, i.e., a propensity to use violence under the right circumstances. Table 1 describes the default distributions used to “populate” the world with civilians of these characteristics. The three parameters are distributed normally, however, the mean of the anger parameter distribution is 0.25, while the mean of the fear and violence threshold parameter distributions is set to 0.5. This allows for only a small proportion of civilians to become initially latent insurgents (Bennett 2008, 3.4).[7] Five hundred (500) civilians are placed on the grid by default.
| Notation | Parameter | Scope | Definition | Range | Default Value |
| Space Size | Global | Dimensions of map grid | 1+ | 50 | |
| Interaction Range | Global | Size of neighborhood for insurgents looking to attack, and for collateral damage range | 1 to size of map | 3 | |
| effectiveness | Effectiveness | Global/All soldier | Probability of removing an insurgent during a soldier’s counterattack | 0.0 to 1.0 | 0.01 to 0.9* |
| accuracy | Accuracy | Global/All Soldiers | 1-accuracy equals the probability of injuring any civilian within interaction range during a soldier’s counterattack | 0.0 to 1.0 | 0.01 to 0.9* |
| anger | Initial Anger | Individual/Each Civilian | Initial level of this civilian’s anger at the government | 0.0 to 1.0 | Normally distributed, mean 0.25, SD 0.125 |
| fear | Initial Fear | Individual/Each Civilian | Initial level of this civilian’s fear of government response to insurgent act | 0.0 to 1.0 | Normally distributed, mean 0.5, SD 0.25 |
| Violence Threshold | Individual/Each Civilian | Level that anger must pass for civilian to be willing to engage in violent insurgency | 0.0 to 1.0 | Normally distributed, mean 0.5, SD 0.25 | |
| Fear Increment | Global | Amount that fear increases in each civilian injured by a soldier counterattack | 0+ | 0.10 | |
| Anger Increment per Injury | Global/All Soldiers | Amount per injured civilian that anger changes in each civilian injured by: | -1 to +1 (normally > 0) | ||
| - Moderate | - soldier counterattack (when soldier was responding to insurgent action) | 0.05 | |||
| - High | - soldier proactive attack (when soldier attacks in turn Turn rather than recruiting) | 0.1 | |||
| PIR | P(Insurgent Recruits) | Global/All Insurgents | Probability an insurgent will recruit when selected to take action (alternative is to undertake attack) | 0.0 to 1.0 | 0.0 to 0.9* |
| Recruits) | All | will recruit when selected | |||
| Anger Change Given Insurgent Recruitment | Global/All Insurgents | Change in civilian anger after being recruited by insurgent | -1.0 to +1.0 (normally > 0) | 0.0 to 0.25* | |
| Number Civilians Recruitable by Insurgent | Global/All Insurgents | Number of civilians an insurgent affects if it recruits | 1+ | 1 to 9* | |
| P(Insurgent Exposed) Given an Attack | Global/All Insurgents | Probability an insurgent is exposed when it attacks | 0.0 to 1.0 | 1.0 | |
| PIEWR | P(Insurgent Exposed) Given it Recruits | Global/All Insurgents | Probability an insurgent is exposed when it recruits | 0.0 to 1.0 | 0.0 to 0.99* |
| PGR | P(Soldier Does Good Works) | Global/All Soldiers | Probability a soldier will recruit (provide aid), when selected to take action (alternative is to undertake attack) | 0.0 to 1.0 | 0.0 to 0.9* |
| Anger Change Given Soldier Recruitment | Global/All Soldiers | Change in civilian anger after being recruited by Soldier | -1 to +1 | −0.25 to | |
| Number Civilians Recruitable by Soldier | Global/All Soldiers | Number of civilians a soldier affects if it recruits | 1+ | 1 to 9* |
A rebel/insurgent is a civilian who is willing to engage in violence against the government, and specifically against a nearby soldier (who represents the government). Insurgents in turn may be latent, i.e., willing to engage in violence, or active, i.e., having actually done so. Growth of insurgency occurs in the model when ordinary civilians turn into insurgents. A civilian becomes a latent insurgent when the civilian is angrier at the government than afraid of it (angerit>fearit), and if their anger passes an individual threshold propensity to use violence (angerit> violence thresholdit). If a latent insurgent is within a defined range of a soldier and is given an opportunity, then the latent insurgent will conduct an attack and become an active insurgent.
The insurgents’ assumed goal is to convert more civilians into insurgents. Each tick, a randomly selected latent insurgent either attacks a nearby soldier (if PIR is less than a random draw from a uniform distribution) or uses the aid strategy to peacefully recruit nearby civilians (if PIR is greater than or equal to a random draw). The general activity of “peaceful recruitment” covers many specific actions on the ground that a civilian could use to express his or her anger at the government, including secretly recruiting followers, participating in a protest to express displeasure, writing or blogging or posting, or using many other specific activities designed to create attention and draw followers to the insurgents’ cause.[8]
Soldiers’ assumed goal is to remove all of the latent insurgents from the world, thereby defeating the insurgency. Soldiers target insurgents to pursue this goal. Each tick, a randomly selected soldier either attacks an active nearby insurgent if there is any (if PGR is less than a random draw from a uniform distribution) or uses the aid strategy to peacefully recruit nearby civilians (if PGR is greater than or equal to a random draw). By default, 100 soldiers are placed on the grid.
Space: We did not alter the simulation space from Bennett’s (2008) model, thus the space in the model is simulated by a two-dimensional grid (not a torus) of rectangular cells (by default, the size of the grid is 50 by 50 cells). Agents interact only with their neighbors, where neighbors are defined as all actors within a specified Moore distance (3 cells by default). We may think of this space as a city district, or a city, or a country. Each agent occupies one grid cell, and only one agent can occupy one cell. The agents do not move.
World Map Display: We also did not alter the display of agents from Bennett’s (2008) model. Agents are displayed in the space via different colors and shapes. Civilian agents may be green (anger < fear < violence threshold), yellow (anger > fear and fear < violence threshold), orange (latent insurgents, i.e., anger > fear > violence threshold), or red (active insurgents, i.e., a latent insurgent that carried out an attack). Soldier agents are represented by blue squares, outlined in red when soldiers are attacked by active insurgents.
Modeling the military approach: As Figure 1 shows, there are three circumstances in which soldiers may use the military action: (i) during a soldier’s turn, a soldier may probabilistically determine to attack, given that there is an active insurgent in the neighborhood; (ii) during an insurgent’s turn, a soldier responds to an insurgent attack with a counterattack; (iii) during an insurgent’s turn, a soldier responds to an insurgent’s use of aid, if an active insurgent is detected during peaceful recruitment. While a significant portion of violence in civil conflicts is remote, e.g., the use of improvised explosive devices by the rebels or the use of drones by the government, here we only model direct violence. Future research should explore the consequences of remote violence on duration of insurgency.[9]
A soldier executes the military action by removing (capturing or killing) an insurgent with a probability equal to the soldier’s level of effectiveness, i.e., P(Soldier Removes Insurgent)=effectiveness. This parameter captures soldiers’ ability to identify who the insurgents in the population are and target them. In other words, it is uncertain if soldiers will be able to identify who the insurgent is after observing an attack occur. The effectiveness parameter is supposed to capture the difficulty of obtaining intelligence about who the insurgents are in a population.
The probability that a soldier’s counterattack inflicts collateral damage on each civilian in the neighborhood of the targeted insurgent is parameterized by the soldier’s level of accuracy, i.e., each nearby civilian is injured with probability P(Soldier Injures Civilians)=1−accuracy. Furthermore, multiple civilians may be hurt in the soldier’s counterattack creating a temporary variable Number of Civilians Injured, which records the number of hurt civilians for a current instance of soldier counterattack. When any civilian is hurt, his or her level of fear of the government increases (a deterrent effect), as shown below each civilian i in tick t+1:
| $${fear}_{i(t+1)} = {fear}_{it} + 0.1 (1-{fear}_{it})$$ | (1) |
In addition, a civilian’s level of anger also increases. Furthermore, anger increases in proportion to the total number of civilians injured by the soldier’s attack and the amount of increase accounts for whether a soldier was provoked by an insurgent, as follows:
| $${anger}_{i(t+1)} = {anger}_{it} + 0.05* {Number\,of\,Civilians\,Injured}*(1-{anger}_{it})$$ | (2a) |
| $${anger}_{i(t+1)} = {anger}_{it} + 0.1* {Number\,of\,Civilians\,Injured}*(1-{anger}_{it})$$ | (2b) |
Consider an example. Two civilians got injured during a soldier’s counterattack. Civilian A had fear of 0.1 and anger of 0.05, while civilian B had fear of 0.6 and anger of 0.3. Civilian A’s fear will update to 0.19, while civilian B’s fear will update to 0.64, showing the “diminishing return” in fearfulness to reflect that over time it takes more extreme actions to provoke the same response in human beings (Bennett 2008, 3.13). Similarly, civilian A’s anger will update from 0.05 to 0.145, while civilian B’s anger will update from 0.3 to 0.37. If civilians A and B were injured in an unprovoked attack by a soldier, then their fear in tick t+1 would have been the same as after a counterattack, but their anger levels would have been 0.24 and 0.44 respectively.
The model assumes that soldiers do not die. In addition, the supply of civilians is effectively infinite: although insurgents die and are removed, they are always replaced with a randomized civilian (not necessarily a new insurgent) placed somewhere in the world grid.
Modeling the aid approach: Both soldiers and rebels probabilistically decide between attacking their opponents and employing aid to recruit nearby civilians peacefully. The probability of each action is set exogenously, and globally (one value for all soldiers, one for all civilians). This exogenous, centralized probability setting provides direction across agents. If a central government or other command structure were to dictate (and rigorously enforce) that one option was always to be followed, the probability of one action would be set to 0% or 100%. Alternatively, as agents have more discretion/freedom, the probability will be closer to 50%. In other words, we are specifying that the proclivity to carry out aid projects is set centrally, but communication, impact, and reaction come from local gains/visibility of these projects. A future project could expand the spread of information by expanding the radius of interaction/view around any action. We suspect that this would accelerate the dynamics of the model rather than make a fundamental change, but fully exploring the implications of global communication/information remains for further work.
If a soldier chooses to use the aid strategy during his or her turn, then the soldier will gain support decrease the anger of a Number of Recruitable Civilians by Soldier by a given increment Anger Change Given Soldier Recruitment. Both parameters are varied systematically in the model, as described in Table 2. The Number of Recruitable Civilians by Soldier takes on values of 1, 5, and 9 civilians. The increment by which civilians’ anger declines varies as −0.25, −0.15, and −0.05. The recruited civilians’ anger in the following tick is updated as:
| $${anger}_{i(t+1)} = {anger}_{it} + {Anger\,Change\,Given\,Soldier\,Recruitment}*(1-{anger}_{it})$$ | (3a) |
For example, civilians A and B, whose anger levels were 0.05 and 0.3 respectively in tick t, were recruited by a soldier that was assigned to recruit 5 civilians decreasing their anger by 0.1. In tick t+1, A’s anger will become 0 (-0.045 would be updated to 0) and B’s anger will become 0.23. If the soldier was able to decrease civilians’ anger only by 0.05, then updated anger levels would be 0.0025 for A and 0.265 for B.
When a rebel chooses to use aid, she or he is assumed to increase the anger of a Number of Recruitable Civilians by Insurgent (systematically varied in the simulation between 1, 5, and 9) by a certain increment, Anger Change Given Insurgent Recruitment (systematically varied between 0.05, 0.15, and 0.25). The affected civilians’ anger in the following time unit will be:
| $${anger}_{i(t+1)} = {anger}_{it} + {Anger\,Change\,Given\,Insurgent\,Recruitment}*(1-{anger}_{it})$$ | (3b) |
For instance, the same civilians A and B, whose anger levels were 0.05 and 0.3 respectively in tick t, were recruited among the 5 other civilians by a rebel. The rebel was able to increase civilians’ anger by 0.1. In tick t+1, A’s anger will become 0.145 and B’s anger will become 0.37. If the soldier was able to decrease civilians’ anger only by 0.05, then updated anger levels would be 0.0975 for A and 0.335 for B.
As with the attacking insurgents, detection of peacefully recruiting insurgents is uncertain. When insurgents attack, in the simulation code, they are revealed to soldiers, but soldiers may have low ability to identify and remove insurgents, i.e., low effectiveness, thus we say that identifying true insurgents is uncertain, as the probability of their capture varies. The probability of insurgent exposure when recruiting, PIEWR, is varied between 0, 0.5, and 1.0. This modeling choice leads to insurgent attacks always triggering soldiers’ counterattack (that may or may not remove the insurgent or injure innocent bystanders), while peaceful recruitment triggers soldier counterattack with probability PIEWR. This modeling choice reflects the underlying reality that violent action is easier to detect and justify a response to. While perfect detection of peacefully recruiting rebels is unrealistic, we investigate this scenario to understand whether the gains from intelligence are linear. They are not, as explain in the analysis section.
| Notation | Model Parameter | Discrete values analyzed | Total unique values |
| effectiveness | Effectiveness | 0.01, 0.1, 0.2, 0.3, 0.4, 0.5, 0.6, 0.7, 0.8, 0.9 | 10 |
| accuracy | Accuracy | 0.01, 0.1, 0.2, 0.3, 0.4, 0.5, 0.6, 0.7, 0.8, 0.9 | 10 |
| PGR | P(Soldier Does Good Works) | 0.0, 0.1, 0.2, 0.3, 0.4, 0.5, 0.6, 0.7, 0.8, 0.9 | 10 |
| Number of Civilians Recruitable by Soldier | 1, 5, 9 | 3 | |
| Anger Change Given Soldier Recruitment | -0.25, -0.15, -0.05 | 3 | |
| PIR | P(Insurgent Recruits) | 0.0, 0.1, 0.2, 0.3, 0.4, 0.5, 0.6, 0.7, 0.8, 0.9 | 10 |
| Number of Civilians Recruitable by Insurgent | 1, 5, 9 | 3 | |
| Anger Change Given Insurgent Recruitment | 0.05, 0.15, 0.25 | 3 | |
| PIEWR | P(Insurgent Exposed Given it Recruits) | 0.0, 0.5, 1.0 | 3 |
Example Runs
Each run of the simulation produces an entire history of interactions between soldiers and rebels, and continues either until the insurgency is defeated (no latent insurgents remain in the world), or 5,000 ticks are reached (loosely indicating a self-sustaining insurgency).
We illustrate the dynamics of the simulation by showing the termination state display output for nine individual runs in Figures 3, 4, and 5. Figure 3 describes the display output for three runs, all of which had highly inaccurate and ineffective military action by soldiers (effectiveness=0.2 and accuracy=0.2), i.e., soldiers miss targets and injure bystanders 80% of the time. Figure 4 presents the display output for three runs, in which soldiers had medium levels of accuracy and effectiveness (0.5 each). Figure 5 shows the output from the three runs, in which soldiers were highly accurate and effective (effectiveness=0.8 and accuracy=0.8), i.e., soldiers miss targets and injure bystanders 20% of the time.

Each panel of Figures 3, 4, and 5 shows three displays. The leftmost display is the two-dimensional world map grid on which the actors are located. It is described in subsection World Map Display of the section Model.
The central display titled “Actors” shows the counts of actors and events in the simulation run over time. The y-axis shows a simple count of agents and instances of events; one unit on the y-axis represents 100 agents/instances. The x-axis represents time; one unit of the x-axis represents 1,000 ticks. In all nine runs, this display shows that the simulation has 500 civilians at all times (shown in blue), because we replace each killed insurgent with a randomly placed civilian. In addition, the central display tracks the number of active insurgents (shown in red), number of latent insurgents (green), cumulative number of insurgents killed (black), and the number of recent attacks (orange). The rightmost display “Anger/Fear’’ shows the average levels of anger and fear among civilians over time. Both anger and fear are bounded between 0 and 1 and so is the y-axis of the rightmost display. The x-axis represents time; one unit of the x-axis represents 1,000 ticks.
Panels (a), (b), and (c) of Figures 3-5 differ by how the actors employ aid. Panel (a) replicates the model in Bennett (2008) without letting soldiers or insurgents use any aid option. Panel (b) presents scenarios in which soldiers use a well-designed aid program 50% of the time, but insurgents never use aid. Anecdotal evidence suggests that most rebel groups provide at least some public goods to the local communities, so this scenario is unrealistic. Yet, it is useful as a hypothetical best-case scenario for the government. Finally, panel (c) shows scenarios in which both soldiers and insurgents employ well-designed aid programs 50% of the time. By "well-designed" aid programs we mean those that affect nine civilians at a time and decrease/increase civilians' anger by the greatest increment of -0.25 (for soldiers) and 0.25 (for insurgents).
Finally, we used the random seed of 1 for each of the nine runs to ensure comparability among the nine runs.
The role of aid for soldiers of low accuracy and effectiveness. Consider Figure 3, which shows scenarios of soldiers with low accuracy and effectiveness (both 0.2), a “nightmare scenario for most governments …[that] might fit the case of fighting an urban counterinsurgency campaign, where insurgents have many places to hide, and where noninsurgent civilians are densely packed” (Bennett 2008: 4.11). All three scenarios (3a, 3b, and 3c) are forced to stop at the 5,000th tick, indicating that an insurgency spreads throughout the entire population and becomes established in a given territorial unit.
Compared to scenario 3a, the introduction of soldiers’ aid strategy (3b) lowers the average level of anger in the population, as shown in the Anger/Fear display. In scenario 3a, it takes only 438 ticks for soldiers to create a hostile population (at tick 439, average anger exceeds than average fear and remains close to or above 0.9 for the rest of the model run). When only soldiers employ aid (3b), the average anger never surpasses average fear; it takes 1,892 ticks for the average anger to reach 0.7 for the same inaccurate and ineffective soldiers (in 3a the average anger of 0.7 was reached at ticks 439). When both rebels and soldiers employ aid (3c), the average anger approaches but never surpasses average fear and it takes 1,314 ticks to reach the average anger of 0.7.
Introducing aid gives soldiers fewer opportunities to remove insurgents, thus, the cumulative number of killed insurgents declines from 1,237 in scenario 3a with no aid to 800 in 3b and 713 in 3c. Recall that soldiers target insurgents as a response to insurgent attack and during soldier turn (on patrol). This is why introducing soldier aid strategy 50% of the time does not cut the number of removed insurgents in half. Furthermore, if rebels recruit civilians peacefully (3c), they further reduce soldiers’ opportunities to counterattack and remove insurgents from the population as insurgent exposure when they recruit is probabilistic.
Fewer opportunities to attack, combined with insurgents raising civilians’ anger in addition to soldiers’ angering civilians by creating collateral damage, leads to 40% of the population becoming active insurgents by the end of run 3c. This large number of active insurgents is also shown by clusters of red circles in world map display in panel 3c. By contrast, only 8% and 3% of civilians constitute active insurgent at the 5,000th tick of runs 3a and 3b respectively, implying that if the runs 3a-3c were not interrupted at the 5,000th tick, scenario 3c would have lasted much longer than 3a and 3b.
In summary, soldiers that miss insurgent targets and injure civilians 80% of the time cannot defeat an insurgency at its early stages, even when they employ aid. While relying on aid helps slow the speed of growth of insurgency, aid cannot compensate for the dangerous effects of ineffective and inaccurate military action.
The role of aid for soldiers of medium accuracy and effectiveness. Consider Figure 4, which depicts end-state output from three scenarios of soldiers with medium accuracy and effectiveness (both 0.5). Scenario 4a is consistent with Bennett’s (2008) finding that once soldiers capture targets and avoid hurting civilians at 40% of the time or more, an average duration of insurgency drops considerably. Scenarios 4a, 4b, and 4c end before the 5,000th tick, indicating that an insurgency does not become sustained in a given territorial unit. Adding aid strategy creates a wide variation in the duration of insurgency: the 4a run with no aid ends at the 1,148th tick, the 4b run with soldiers’ aid ends after 246 ticks, and the 4c run with both sides’ aid ends at the 3,057th tick.
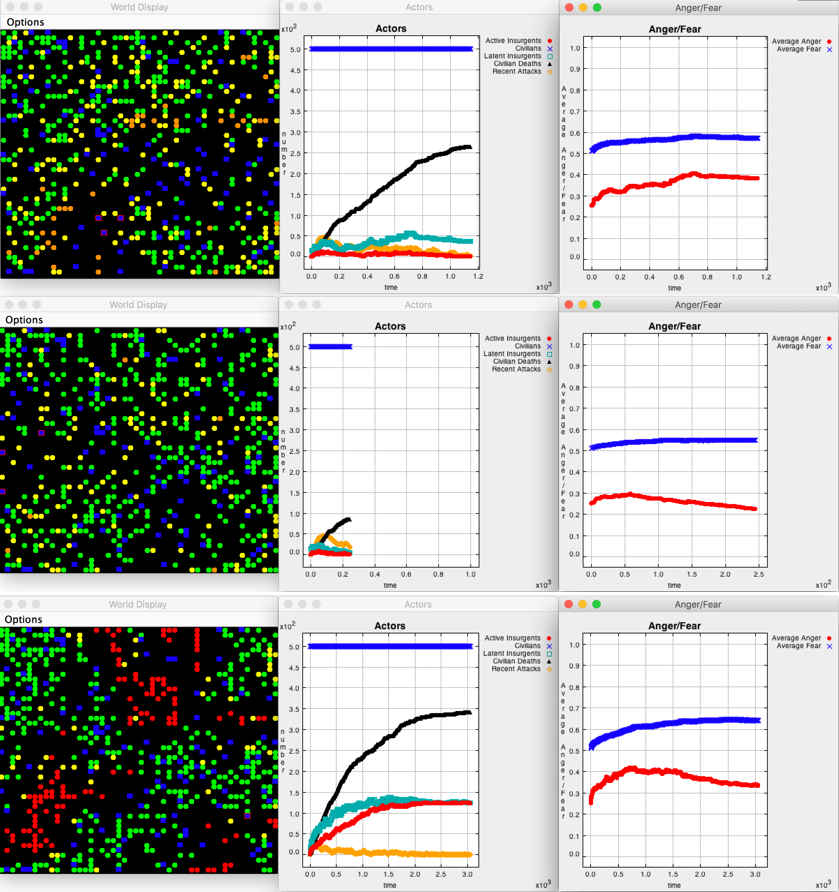
Relative to scenarios 4a and 4b, the 4c run describes a more realistic situation of both sides employing aid. Allowing aid on both sides extends insurgency more than twofold compared to the 4a run and more than twelvefold compared to the 4b run. This is due two reasons: (i) soldiers go on patrols 50% less, since they recruit half the time, thus they can remove half of insurgents in a given time period, and (ii) insurgents that peacefully recruit civilians are not always detected by soldiers.
In the cases with medium accuracy and effectiveness, average anger in the population never surpasses average fear. In scenario 4a, the highest level of average anger is 0.42, while introducing soldiers’ aid in 4b lowers the highest level of anger achieved to 0.31. When both rebels and soldiers employ aid (4c), the average anger reaches the 0.44 level at about the same time as the peak anger is reached in the 4a run with no aid (around the 600th and 700th tick respectively).
Lower levels of average anger among civilians also mean that the runs in Figure 4 end with lower proportions of latent insurgents than the runs in Figure 3. In the 4c run, insurgents raise civilians’ anger at the government via aid, making 29.2% of civilians latent insurgents. This proportion is still much lower than half the population being latent insurgents by the end of the scenario 3c.
In summary, soldiers that miss insurgent targets and injure civilians 50% of the time defeat an insurgency at its early stages regardless of the aid approach. It is important to note that for the cases of soldiers’ medium levels of accuracy and effectiveness, the set-up of the aid strategy may extend the duration of insurgency more than twice when both soldiers and insurgents peacefully recruit.
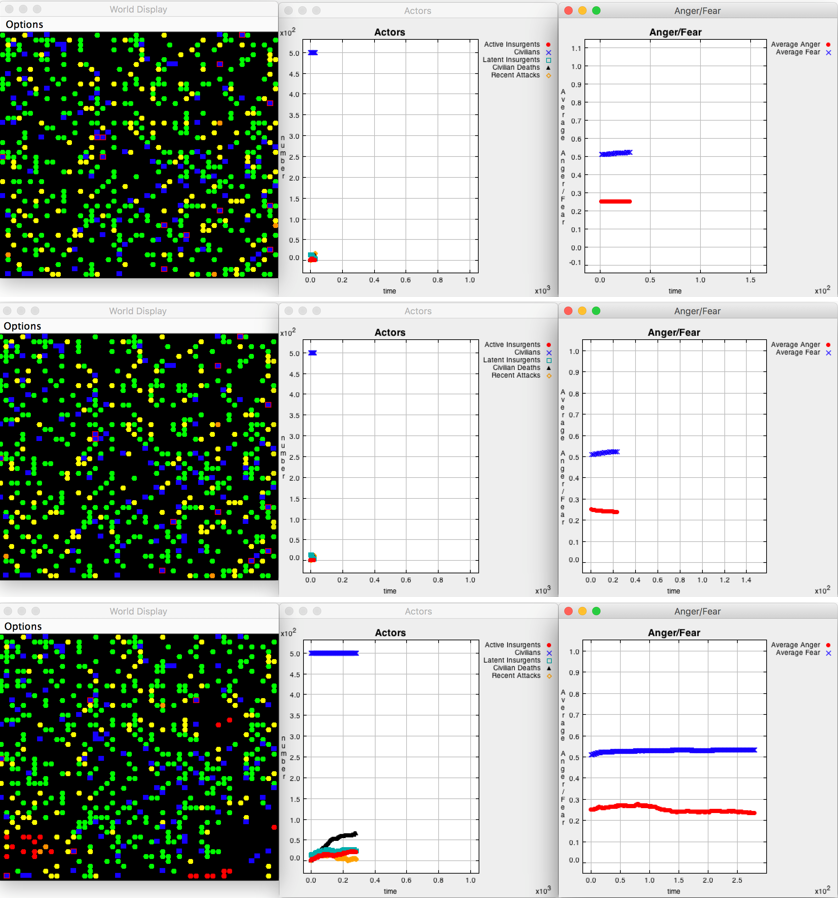
The role of aid for soldiers of high accuracy and effectiveness. Consider Figure 5, which presents end-state output from three scenarios of soldiers with high accuracy and effectiveness (both 0.8). Scenario 5a is consistent with Bennett’s (2008) finding that once soldiers capture targets and avoid hurting civilians at 80% of the time, an insurgency is defeated swiftly (in just 30 ticks in the 5a run). Among scenarios 5a, 5b, and 5c, the latter depicts the longest insurgency that ends after 283 ticks, still a very short insurgency compared to the runs of Figure 4. This further demonstrates that the levels of accuracy and effectiveness of soldiers’ military action are the primary determinants of the duration of insurgency. This is not to say that the aid strategy does not matter. For instance, letting both soldiers and insurgents recruit half the time in the 5c run extends an insurgency more than nine-fold relative to scenario 5a. Yet, even this extended duration is very short when compared to runs with low/medium effectiveness and accuracy.
Analysis of Repeated Simulations
The duration of insurgency is an emergent feature of our model, such that if the soldiers have no latent insurgents in their range, the insurgency is considered defeated. Alternatively, reaching 5,000 ticks terminates a run, loosely indicating a self-sustaining insurgency.[10] We evaluate the output of the simulation, assuming that government actors prefer insurgencies that are shorter and rebel actors – longer.
Table 2 specifies the discrete values of key initialization parameters and details the total number of unique combinations of parameter values: 4 parameters were varied across 10 discrete values, while 5 parameters were varied across 3 values, resulting in (104)(35)=2,430,000 unique combinations of parameter values. Since the model has stochastic elements, we analyze summaries of multiple histories generated from the starting value sets to determine reliable trends that appear across multiple iterations of the model, rather than examining a single run which might not be representative. 38 million simulation runs were recorded and collapsed into a dataset of 2.43 million observations, such that each observation is an average of 10 to 15 runs of the model at each unique combination of parameter values.
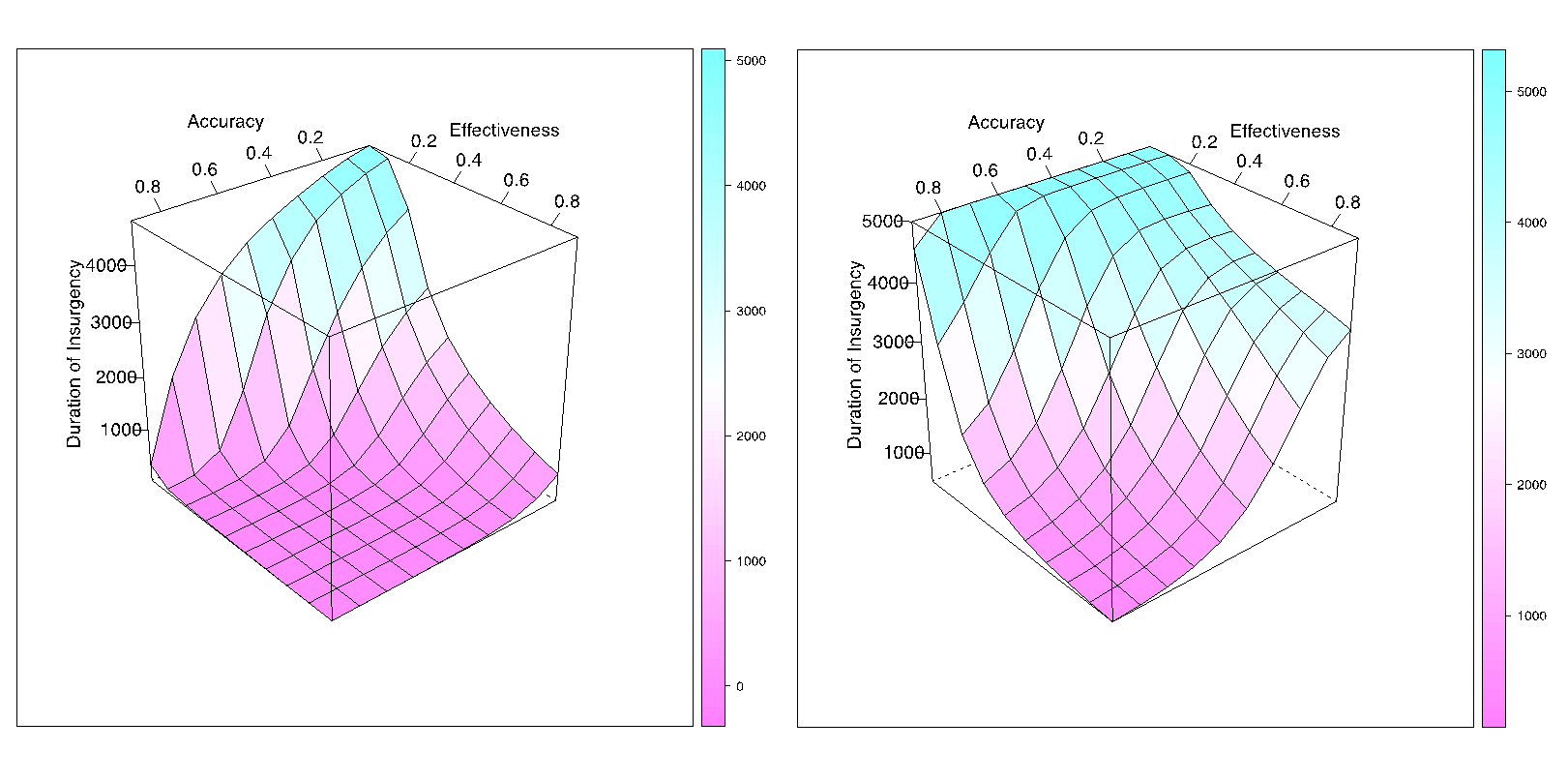
Baseline effect of the quality of the military approach. Figure 6 shows the duration of insurgency varying as a function of the quality of the military strategy for those cases when neither side uses aid strategy (also see row 1 in Table 3 for more precise mean and variance values).[11]
We use this surface as a baseline for comparison with the scenarios discussed below. In this and subsequent graphs, the height represents duration of insurgency (bounded between 0 and 5,000, where the maximum point represents the cutoff, at which we assume that insurgency cannot be defeated). Length and depth of the graph represent soldiers’ effectiveness and accuracy (both bounded between 0.01 and 0.9), two features that define the quality of the military strategy.
Figure 6 shows a reverse relationship between the quality of the military strategy and the duration of insurgency: insurgencies are longest when accuracy and/or effectiveness are low and shortest when those levels are high. If soldiers miss targets more than 70% of the time (effectiveness<0.3), it takes a high level of accuracy to defeat an insurgency (accuracy>0.7). If soldiers create collateral damage more than 70% of the time (accuracy <0.3), improvements in effectiveness lead to shorter insurgencies. If both accuracy and effectiveness improve above 30%, insurgencies can be defeated rapidly.
Baseline effect of the quality of aid: Both sides (soldiers and rebels) may employ the aid strategy. Figure 7 presents highly stylized scenarios in which only one side does so (only soldiers provide aid in 6a and only insurgents – in 7b). In both panels of Figure 7 actors employ a well-designed aid strategy, i.e., soldiers and insurgents affect 5 to 9 civilians, whose anger is changed by larger anger increments (–0.15 and –0.25 for soldiers’ aid strategy and 0.15 and 0.25 for insurgents’ aid strategy).

The main takeaway of Figure 7 is unsurprising: one’s decision to abandon the aid strategy benefits the opponent. As panel 7a shows, if insurgents never employ aid, while state soldiers use well-designed development programs 90% of the time, then even militarily inaccurate and ineffective soldiers will defeat insurgency (all cases of insurgency end under 4,000 ticks, thus not one case becomes a sustained insurgency). Similarly, if soldiers never employ the aid strategy, yet rebels are able to affect multiple civilians at a time, then whether insurgents will succeed at reaching 5,000 ticks depends entirely on how accurate and effective the soldiers are. If soldiers locate targets at least 30% of the time (effectiveness≥0.3) and avoid hurting civilians at least 30% of the time (accuracy≥0.3) they will be able to remove all insurgents before it reaches 5,000 ticks. Furthermore, if soldiers’ effectiveness and accuracy≥0.5, they defeat insurgency very quickly (in under 1,000 ticks). While these scenarios are unrealistic, they help illustrate that even when soldiers ignore aid, they still can defeat an insurgency if their military response relies on intelligence and avoids hurting civilians.
Is the military or aid approach more important in defeating insurgency? Our model yields that, for soldiers to defeat an insurgency, improvements in accuracy and effectiveness are more important than improvements in the two features of the aid strategy: the number of recruitable civilians by soldier and anger change given soldier recruitment. In other words, if the model’s assumptions capture insurgency dynamics adequately, it is more critical for soldiers to invest in their ability to acquire intelligence about who the rebels are (parameterized by effectiveness) and do so without hurting bystanders (parameterized by accuracy), than to invest in designing such economic development programs that would improve the welfare of more civilians.
Table 3 presents average durations of insurgency by the features of the aid strategy and by the features of the military approach. Horizontal scenarios are numbered from 1 to 11. Each scenario contains five rows to present durations of insurgency as the average, standard deviation, 25th percentile, median, and 75th percentile. The scenarios are labeled as high, medium, and low quality of the aid program’s design, parameterized by the number of recruitable civilians by soldier/insurgent and the anger change given soldier/insurgent recruitment. In addition, each scenario contains three columns that represent high, medium, and low levels of accuracy and effectiveness of soldiers’ military action respectively.
For each scenario presented across rows of Table 3, improvements in the quality of the military approach lead to greater reductions in duration of insurgency than improvements in the quality of aid. In other words, differences across columns of Table 3 are greater than differences across rows. The effect of aid quality is especially small in the rightmost column of cases with inaccurate and ineffective military approach: with one exception (discussed in the following subsection), all average durations are less than a standard deviation away from a sustained insurgency (5,000 ticks).[12] In our simulation, it is possible for soldiers to defeat rebels when soldiers’ aid strategy affects only a few civilians but their military strategy is effective and accurate. In contrast, it is impossible for a government to defeat an insurgency if soldiers affect a lot of civilians through aid programs but cannot identify rebels or capture them without hurting bystanders.
| Quality of aid response | Quality of military response3 | Type of cell entry | |||
| Soldiers1 | Insurgents2 | High | Medium | Low | |
| 1. No aid | No aid | 15.46 | 106.05 | 4231.41 | Mean |
| [2.26] | [106.53] | [905.64] | St. deviation | ||
| 13.7 | 40.36 | 3521.8 | 25thpercentile | ||
| 15.18 | 66.09 | 4739.217 | 50thpercentile | ||
| 16.91 | 127.63 | 5000 | 75thpercentile | ||
| 2. Aid | Aid | 53.26 | 748.28 | 4590.52 | Mean |
| (all cases) | (all cases) | [107.70] | [1172.06] | [805.64] | St. deviation |
| 17.75 | 75.45 | 4618.69 | 25thpercentile | ||
| 23.45 | 186.18 | 5000 | 50thpercentile | ||
| 33.83 | 819.75 | 5000 | 75thpercentile | ||
| 3. High | High | 145.15 | 1116.71 | 4689.04 | Mean |
| [111.98] | [588.52] | [487.37] | St. deviation | ||
| 56.94 | 719.18 | 4546.41 | 25thpercentile | ||
| 132 | 984.82 | 4977.61 | 50thpercentile | ||
| 194.83 | 1601.16 | 5000 | 75thpercentile | ||
| 4. | Medium | 23.31 | 154.24 | 3867.31 | Mean |
| [7.42] | [104.09] | [1170.06] | St. deviation | ||
| 17.66 | 76.75 | 2756.46 | 25thpercentile | ||
| 22.5 | 133.73 | 4329.02 | 50thpercentile | ||
| 28.9 | 202.82 | 4976.68 | 75thpercentile | ||
| 5. | Low | 19.01 | 78.60 | 3233.89 | Mean |
| [4.60] | [48.04] | [1470.66] | St. deviation | ||
| 15.36 | 45.36 | 1801.75 | 25thpercentile | ||
| 17.6 | 63 | 3731.55 | 50thpercentile | ||
| 22.75 | 104.82 | 4759.91 | 75thpercentile | ||
| 6. Medium | High | 267.50 | 2550.83 | 4946.26 | Mean |
| [263.01] | [1242.32] | [119.73] | St. deviation | ||
| 80 | 1700.72 | 4985.94 | 25thpercentile | ||
| 137.64 | 2487.17 | 5000 | 50thpercentile | ||
| 409 | 3501.36 | 5000 | 75thpercentile | ||
| 7. | Medium | 23.62 | 351.80 | 4739.99 | Mean |
| [8.40] | [399.87] | [441.87] | St. deviation | ||
| 16.3 | 79.82 | 4699.62 | 25thpercentile | ||
| 22.64 | 207.67 | 4991.66 | 50thpercentile | ||
| 26.8 | 357.64 | 5000 | 75thpercentile | ||
| 8. | Low | 20.60 | 107.23 | 4215.17 | Mean |
| [6.02] | [83.18] | [1055.53] | St. deviation | ||
| 15.36 | 51 | 3491.012 | 25thpercentile | ||
| 20.25 | 70.36 | 4719.86 | 50thpercentile | ||
| 26.4 | 170.83 | 5000 | 75thpercentile | ||
| 9. Low | High | 345.31 | 3880.60 | 4987.11 | Mean |
| [365.84] | [1136.44] | [43.03] | St. deviation | ||
| 71.94 | 3168.72 | 5000 | 25thpercentile | ||
| 179.75 | 4299 | 5000 | 50thpercentile | ||
| 501.73 | 4783.18 | 5000 | 75thpercentile | ||
| 10. | Medium | 24.38 | 927.91 | 4963.18 | Mean |
| [9.35] | [1164.248] | [93.91] | St. deviation | ||
| 18.08 | 110.33 | 4990.37 | 25thpercentile | ||
| 21.3 | 298.75 | 5000 | 50thpercentile | ||
| 29.81 | 1204.81 | 5000 | 75thpercentile | ||
| 11. | Low | 20.17 | 148.81 | 4678.001 | Mean |
| [5.37] | [174.62] | [593.97] | St. deviation | ||
| 14.91 | 48.73 | 4737.64 | 25thpercentile | ||
| 19.9 | 87.67 | 5000 | 50thpercentile | ||
| 26.08 | 172.27 | 5000 | 75thpercentile | ||
| 1 High quality of state aid: probability of soldiers employing aid PGR=0.5; anger change given soldier recruitment =-0.25; number of recruitable civilians by soldier=9. Medium quality of state aid: PGR=0.5; anger change given soldier recruitment=-0.1; number of recruitable civilians by soldier=5. Low quality of state aid: PGR=0.5; anger change given soldier recruitment=-0.05; number of recruitable civilians by soldier=1. 2 High quality of insurgent aid: probability of insurgents employing aid PIR=0.5; anger change given insurgent recruitment =-0.25; number of recruitable civilians by insurgent=9. Medium quality of insurgent aid PIR=0.5; anger change given insurgent recruitment=-0.1; number of recruitable civilians by insurgent=5. Low quality of insurgent aid: PIR=0.5; anger change given insurgent recruitment=-0.05; number of recruitable civilians by insurgent=1. 3 High quality of soldiers’ military action: accuracy>0.6; effectiveness>0.6. Medium quality of soldiers’ military action: accuracy ≥ 0.4 and ≤ 0.6; effectiveness≥0.4 and ≤0.6; Low quality of soldiers’ military action: accuracy ≤0.3; effectiveness ≤0.3. See Table 1 and Figure 15 of the web appendix for an extended analysis of insurgency duration, and also peak of latent and active insurgents. | |||||
Could the use of aid ever compensate for a low-quality military strategy? The simulation suggests that a government may not avoid a sustained insurgency under an ineffective and inaccurate military strategy by relying on aid. The only exception to this trend is described in the dark-gray column of scenario 5 of Table 3: the average, median, and 75th percentile durations of insurgency under scenario 5 are 3,233.89, 3,731.55, and 4,759.91 respectively, i.e., this is a long insurgency. In this scenario, inaccurate and ineffective soldiers affect nine civilians through aid programs at a time, while insurgents influence only one civilian through aid at a time.[13] We assume that this scenario is unrealistic, because in practice, insurgents would be better off either increasing their peaceful recruitment efforts or forgoing recruitment altogether, letting the inaccurate and ineffective military action by soldiers backfire even more (since insurgent attacks always trigger soldier counterattacks, while a counterattack after insurgent recruitment is based on the probability that an insurgent is exposed given it recruits, PIEWR).
In contrast, under a more realistic set-up in which both sides rely on effective aid strategy, the simulation yields that soldiers cannot defeat insurgents with an ineffective and inaccurate military approach (see scenarios 2-4 of Table 3). Specifically, scenario 3 of Table 3 represents a case of both soldiers and rebels employing a well-designed aid strategy, i.e., both types of agents affect nine civilians at a time and change civilians’ anger by the amount of -0.25 for soldiers and 0.25 for insurgents. Under scenario 3, consider the low quality of military response scenario that summarizes durations of insurgency for the ineffective and inaccurate military approach (soldiers miss targets and injure civilians more 70% of the time). The median insurgency under these conditions lasts 4,977.61 ticks and the 75th percentile insurgency is considered self-sustaining, interrupted at 5,000 ticks.
In fact, with the exception of the aforementioned scenario 5, all median insurgencies under the conditions of inaccurate and ineffective military approach exceed 4,000 time units, i.e., represent prolonged conflicts. Given that the 5,000th tick cut-off point is arbitrary, we should not put too much weight on the difference between insurgencies that end just short of 5,000 and those that are interrupted at the 5,000th step.
Finally, our model suggests that when both sides use the aid strategy, insurgencies survive much longer – even for the most accurate and effective military operations – than in the cases when the aid strategy is omitted. Compare all cases of using aid 50% of the time on both sides (scenario 2 of Table 3) to the baseline scenario of no aid on either side (scenario 1 of Table 3). The average duration of insurgency in scenario 2 is on average 1.5 times greater than in the scenario 1. The differences are especially pronounced when comparing the scenarios of more effective and accurate military action: insurgencies last on average 16 ticks in scenario 1 vs. 522 ticks in scenario 2 for the soldiers that capture targets and avoid collateral damage >60% of time. Furthermore, an average insurgency lasts 177 ticks in scenario 1 vs. 1658 ticks in scenario 2 for soldiers that capture targets and avoid collateral damage 40-60% of time. At the same time, when comparing the militaries of low accuracy and effectiveness across the recruitment scenarios, the differences are negligible. This is an artificiality introduced by the arbitrary cut-off point of 5,000 ticks. Future research may want to consider other cut-off points to investigate whether all inaccurate and ineffective military strategies are equally bad for the government. In summary, our main finding that emerges from Table 3 is that inaccurate and ineffective military approach cannot be compensated for by a well-designed aid program.

The role of intelligence. Our simulation further yields that collection of intelligence is critical to soldiers’ success. We model intelligence collection though two parameters: the probability of locating and removing the attacking insurgents (effectiveness) and the probability of locating the peacefully recruiting insurgents (PIEWR). In those scenarios when both of these probabilities approach 0, soldiers cannot defeat insurgency.
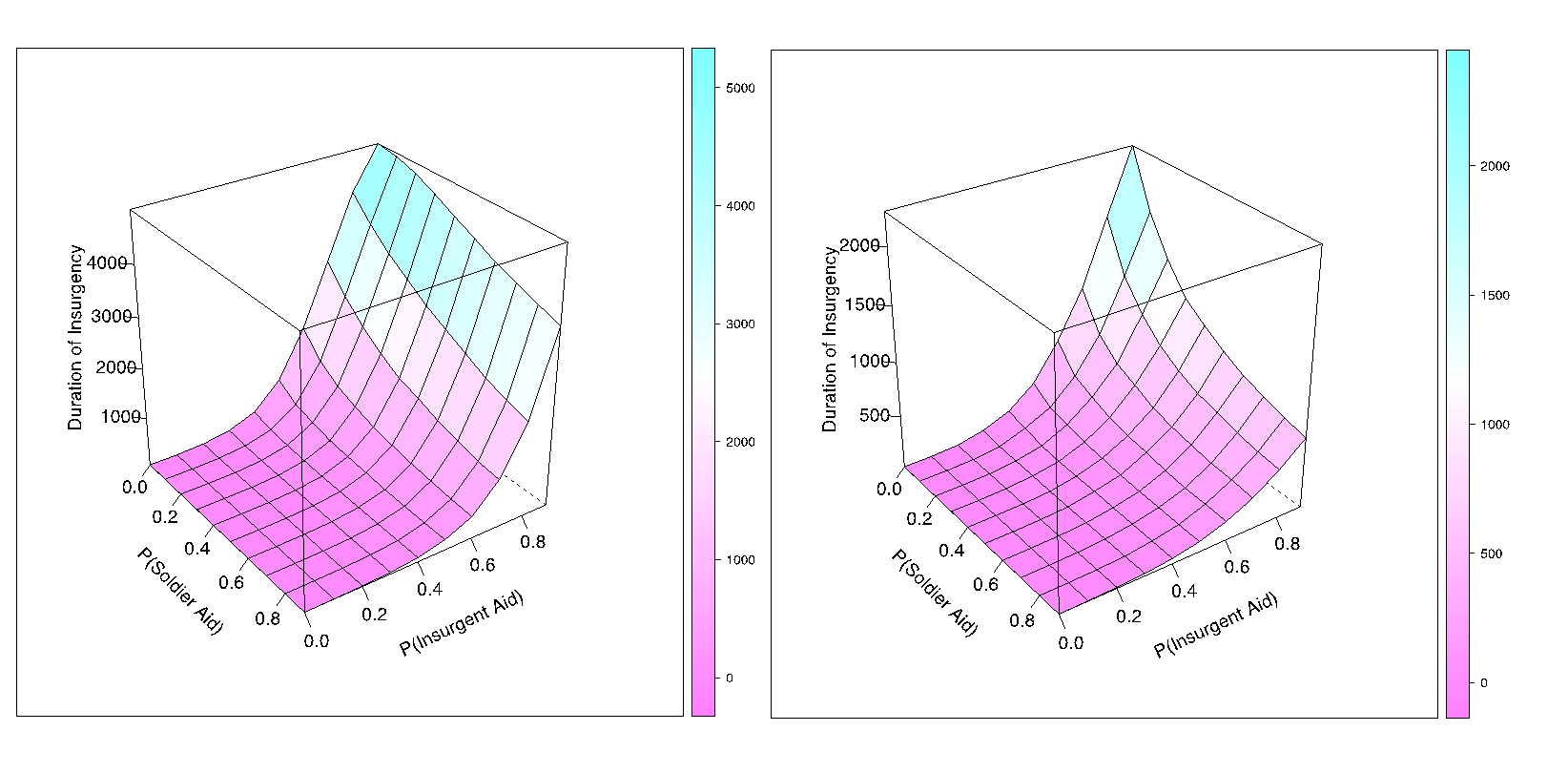
Figure 8 plots insurgency duration as a function of soldiers’ effectiveness and accuracy, when both soldiers and rebels use well-designed aid programs that recruit multiple civilians at a time and change their anger levels by moderate and high increments. The two panels in Figure 8 differ in soldiers’ ability to detect peacefully recruiting rebels (PIEWR = 0 in 8a and 0.5 in 8b). When rebels can peacefully recruit undetected by soldiers (Figure 8a), insurgency duration depends on whether soldiers acquire intelligence about the attacking insurgents (effectiveness) and whether soldiers can avoid collateral damage during their response operations (accuracy). That is, if soldiers have no information about the peacefully recruiting insurgents, but locate the attacking insurgents and avoid collateral damage at least 30% of the time (effectiveness and accuracy both at 0.3), then an average insurgency lasts more than 4,000 ticks, very long but finite. In contrast, if soldiers obtain intelligence about the peacefully recruiting insurgents 50% of the time (Figure 8b) and locate the attacking insurgents and avoid collateral damage 30% of the time, then an average insurgency lasts about 2,000 ticks.[14]

Figures 9 and 10 further emphasize the role of intelligence in counterinsurgency. These figures plot insurgency duration as a function of soldiers’ and rebels’ probability of employing the aid strategy under low levels (Figure 9) and high levels (Figure 10) of accuracy and effectiveness of soldiers’ military action. In Figure 9, the difference between no detection (9a) and imperfect detection of 50% (9b) of peacefully recruiting rebels is insignificant. That is, even when soldiers can detect peacefully recruiting rebels 50% of the time, they still cannot target them effectively and accurately. This difference is much more pronounced between Figures 10a and 10b, as high accuracy and effectiveness of soldiers’ military approach can be further improved by greater detection of the peacefully recruiting rebels (note the maximum duration of insurgency of only 3,000 ticks in 10b, as opposed to 5,000 in 10a). Figure 10a shows that there exists a narrow scenario in which even the soldiers that avoid collateral damage and capture insurgents at least 50% of the time cannot prevent an insurgency from becoming a self-sustaining one. This happens if soldiers obtain no intelligence on peacefully recruiting rebels and rebels use the aid strategy 90% of the time, implying that only 10% of the time they attack, revealing themselves to the soldiers.
Are there any cases when greater reliance on aid is undesirable for counterinsurgents? The model further suggests that –from the viewpoint of soldiers – a well-designed aid strategy is always preferable for accurate and effective military operations,[15] while being futile for the inaccurate and ineffective military campaigns.[16] Figures 9 and 10 differ in the soldiers’ military action: low levels of accuracy and effectiveness in Figure 9 vs. high levels in Figure 10.[17] When soldiers miss their targets and cause collateral damage 50-90% of the time (shown in graphs 9a-b), the region of self-sustaining insurgencies is overwhelming (the median duration of insurgency in Figure 9a is 4,918.15 ticks). Even when defeated, the 10th percentile duration of insurgency in Figure 9a is 1,729.56 ticks. Under inaccurate and ineffective the military strategy the shorter insurgencies occur when insurgents recruit at most 10% of the time and soldiers recruit 80-90% of the time. This hypothetical case – albeit unlikely – underscores the importance of somehow limiting rebel use of the aid strategy when no opportunity to limit civilian casualties exists.
In contrast, under an accurate and effective military strategy when soldiers miss their targets and cause collateral damage less than 50% of the time (shown in graphs 10a-b), rebels rarely achieve a self-sustaining insurgency (compared to Figures 9a-b). Under these circumstances, a higher rate of soldiers’ use of aid reduces the average duration of insurgency.[18]
Finally, obtaining any intelligence about rebels’ use of aid is more important for soldiers than obtaining perfect intelligence. We have also graphed the surfaces in Figures 9 and 10 with soldiers’ ability to detect peacefully recruiting rebels perfectly, i.e., PIEWR= 1.0 (the graphs are omitted for space). While some intelligence makes a big difference for the accurate and effective soldiers (the difference between 10a and 10b), perfect intelligence does not provide as much gain in reducing the duration of insurgency for the state.
In summary, a greater reliance on aid only helps soldiers if they avoid collateral damage more than 50% of the time and obtain at least some intelligence about who the recruiting insurgents are. This conclusion underscores how critical the assumption that civilians trade intelligence for aid is (Berman, Shapiro and Felter 2011; Berman et al. 2013; Condra and Shapiro 2012). Table 3 and Figures 8, 9, 10 demonstrate that neither side undermines its cause by employing a (well-designed) aid strategy, yet, soldiers cannot compensate for an ineffective and inaccurate military action by using peaceful recruitment. The relative weight of military strategy (compared to aid) is greater when considering how both COIN strategies affect the duration of insurgency.
Limitations and Future Work
This work does not exhaust the possible modeling choices with respect to how states and insurgents implement the aid and military strategies. Future work could consider, for instance, an adaptive value for soldiers’ probability of employing the aid strategy. While we have modeled the government’s strategy to employ aid programs as an externally given value, we could allow governments to adapt their strategy in response to the perceived number of insurgents, perceived level of civilian anger, or insurgent strategy. Strategy adaptation could be applied to the insurgents’ probability of using aid (as opposed to violence) as well.
There are also fundamentally different ways that action sequences could be modelled in a simulation of insurgency. For example, the model could be restructured such that instead of one insurgent and one soldier engaging each tick, all insurgents and all soldiers act in each tick. This modeling choice would ensure that none of the available soldiers stays unengaged, which could theoretically happen in the current version of the model, as it is conceivable that a soldier is not randomly picked throughout the entire run. We believe that this restructuring would have the primary effect of speeding up the simulation as multiple actions have effects at once; it could also remove the possible effect of sequential activity and path dependence. It is possible that a similar effect could be obtained in the current sequence by expanding the reach of “media” in the simulation so that actions have less-localized effects on civilians’ anger and fear. For instance, if civilians in a nearby province are made aware of either a successful local aid project or of an attack killing civilians, the effects of the action will spread more rapidly.
We could also explore different types of resource constraints on governments. Our model considers the limitation of state resources only to an extent: there are 100 soldiers at all times in our model and if the state employs the aid strategy 70% of the time, then after, say, 200 ticks (if insurgency survives until then) on average 70 soldiers will have engaged in peaceful recruitment of civilians and 30 soldiers will have employed military action. The current model represents the tradeoff between aid and military action only in the number of soldiers available and each soldier’s inability to do both actions during the same tick. An alternative representation of a tradeoff that governments face could involve consideration of the cost of aid vs. military action, and the cost of deploying (soldier) agents to implement those strategies.
Conclusion
Recent arguments in the counterinsurgency literature suggest the importance of using peaceful aid strategy in conjunction with, or in place of, the military strategy when seeking to defeat an insurgency. To understand the relative importance of each strategy and to evaluate the reasonable balance between the aid and military approaches, we developed a computational model of insurgent and soldier interactions in which both types of agents can either peacefully recruit civilians or undertake military attacks on the opponent. A series of computational experiments established four major implications of our model. First, a high-quality military strategy, i.e., attacking insurgents without harming civilians, is more important for defeating an insurgency than aid. Second, aid cannot compensate for a low-quality military strategy. Third, investing in obtaining at least some intelligence is critical for the government; however, the gains in improving from imperfect intelligence to perfect intelligence are not as dramatic. Finally, soldiers benefit from a greater reliance on aid only if they can obtain some intelligence about the insurgents’ aid activity and soldiers avoid collateral damage during military engagement at least half the time.
When it comes to evaluating the best strategies for insurgents, our model suggests that when facing a poorly trained army, increasing recruitment activities is unnecessary for insurgents, as government troops create more rebels than they kill by their inaccurate and ineffective attacks. In contrast, when insurgents face a well-trained military operation, they are better off avoiding attacks altogether. In this case, recruiting civilians in as much secrecy as possible yields better results for insurgents.
The first two takeaways may be combined into a testable hypothesis: greater amounts of aid provided to those regions where military strategy avoids civilian casualties are expected to suppress insurgent attacks. In contrast, investing in areas where military operations abuse loyal civilians is expected to be counterproductive.
Acknowledgements
We thank the editor and the two anonymous referees for very helpful comments. We are also grateful to Daehee Bak and Burt Monroe for their valuable help and feedback.Notes
- Our focus on these strategies does not deny that many scholars have investigated the importance of multiple other factors in influencing the course of an insurgency or civil war. E.g., we could consider (i) the absence of difficult terrain and the absence of natural resources that could fund a rebel organization (Collier and Hoeffler 2004; Fearon and Laitin 2003; Ross 2004), and (ii) ethnic sorting and cleansing (Agnew et al. 2008; Weidmann and Salehyan 2013). Our simulation ignores these other independent factors for the moment; it could be expanded in the future if we would expect these factors to confound our results.
- The most interesting dynamic of Bennett’s (2008) model emerges at low rates of soldiers capturing targets, which could approximate situations of soldiers having no intelligence about who the individual insurgents are in the population. For instance, in a scenario of soldiers capturing targets 10% of the time, militaries can never defeat an insurgency if they avoid collateral damage 30% of the time or less, while gains in avoiding collateral damage beyond 50% of the time will generate dramatic reductions in insurgency duration (Bennett 2008, 1.6). This effect is replicated in Figure 6.
- Other common labels include "enemy-centric" (Guide to the Analysis of Insurgency 2012) or "hard-power" (Rineheart 2010).
- For instance, see Kocher, Pepinsky and Kalyvas (2011), Condra et al. (2010), Benmelech, Berrebi and Klor (2015). However, see Lyall (2009) and Johnston and Sarbahi (2016) for divergent findings.
- An important caveat to these findings is that empirically, aid disbursements in Iraq seemed to suppress insurgent attacks only in those areas that a government controls, while actually increasing insurgent attacks in areas of split control (Sexton 2016). Since government / insurgent control over territory is an emergent characteristic of our model, we cannot directly compare the underpinnings of our model to Sexton’s (2016) findings. However, our model’s result that the military approach is important at defeating insurgency is consistent with Sexton’s (2016) findings: first, soldiers need to secure an area, then, work on increasing support for the government.
- The simulation was programmed in Java.
- While one might think of plausible alternative distributions for initial fear, initial anger, and violence threshold in the population, in this version, we follow Bennett’s (2008) default values for these parameters to make comparisons with the baseline model more straightforward.
- While we do not separate these activities (e.g. protest vs. quiet action) explicitly, a future version of the model could expand the action set, or by focusing on additional subsets of civilians, like those whose anger is greater than fear, yet the violence threshold has not been met.
- The precise means by which a soldier attacks an insurgent (or vice-versa) is left undefined in the model, it is possible that an actor could be using some method of violence that is not face-to-face.
- We also analyzed additional emergent features of the simulation, notably speed of growth (measured as the time until 25% of the population become latent insurgents), peak number of latent insurgents, and peak number of active insurgents. Analyses of these features support the same conclusions as presented here. For details, see Figures 9a through 12b and Table 1 of the web appendix.
- The figure parallels Bennett’s (2008) results. See Figure 9 in Bennett (2008), as all of the results presented in this paper are the runs with replacement and no neighborhood influence.
- This same point is illustrated in greater detail by a series of 2D graphs in the web appendix. Compare Figures 1a-4b, and Figures 5a-8b.
- Also, refer to Figures 13 and 2a-2b and a note on a narrowly constructed scenario of when the aid strategy may compensate for an incompetent military strategy of the web appendix.
- Figures 3a and 3b in the web appendix communicate this point in greater detail through a series of 2D graphs.
- The exception being a scenario in which the insurgents recruit 90% of the time and there is no exposure of the recruiting insurgents (see Figure 7a).
- The exception being a scenario in which insurgents do not recruit at all (see Figure 4b).
- Across all levels of aid quality in Table 3, Figure 6 approximates the average between the columns "low" and "medium" quality of the military approach and Figure 7 approximates the average between the columns "medium" and "high" quality of the military approach in Table 3. Figures 5a-8b of the web appendix communicate these same takeaways in finer detail in a series of 2D graphs.
- A narrow exception is discussed in the previous subsection.
Appendix: Model Pseudocode
References
AGNEW, J., Gillespie, T.W., Gonzalez, J. & Min, B. (2008). Baghdad Nights: Evaluating the U.S. Military ‘Surge’ Using Nighttime Light Signatures. Environment and Planning A, 40(10), 2285-2295. [doi:10.1068/a41200]
BENMELECH, E., Berrebi, C. & Klor, E. (2015). Counter-Suicide Terrorism: Evidence from House Demolitions. Journal of Politics, 77(1), 27-43. [doi:10.1086/678765]
BENNETT, D.S. (2008). Governments, Civilians, and the Evolution of Insurgency: Modeling the Early Dynamics of Insurgencies. Journal of Artificial Societies and Social Simulation, 11(4), 7: https://www.jasss.org/11/4/7.html
BERMAN, E., Shapiro, J.N. & Felter, J.H. (2011). Can Hearts and Minds Be Bought? The Economics of Counterinsurgency in Iraq. Journal of Political Economy, 119(4), 766-819. [doi:10.1086/661983]
BERMAN, E., Felter, J.H., Shapiro, J.N. & Troland, E. (2013). Modest, Secure, and Informed: Successful Development in Conflict Zones. American Economic Review: Papers & Proceedings, 103(3), 512-517. [doi:10.1257/aer.103.3.512]
CAULKINS, J.P., Grass, D., Feichtinger, G. & Tragler, G. (2008). Optimizing Counter-Terror Operations: Should One Fight Fire with `Fire’ or `Water’? Computers and Operations Research, 35(6), 1874-1885. [doi:10.1016/j.cor.2006.09.017]
COLLIER, P. and Hoeffler, A. (2004). Greed and Grievance in Civil War. Oxford Economic Papers 56, 563-595. [doi:10.1093/oep/gpf064]
CONDRA, L.N., Felter, J.H., Iyengar, R.K. & Shapiro, J.N. (2010). The Effect of Civilian Casualties in Afghanistan and Iraq. Boston. NBER Working Paper No. 16152.
CONDRA, L.N . and Shapiro, J.N. (2012). Who Takes the Blame? The Strategic Effects of Collateral Damage. American Journal of Political Science, 56(1), 167-187. [doi:10.1111/j.1540-5907.2011.00542.x]
EUROPEAN Asylum Support Office. (2012). EASO Country of Origin Information report. Afghanistan. Taliban strategies – Recruitment. Luxembourg: Publications Office of the European Union.
EPSTEIN, J.M. (2008). Why model? Journal of Artificial Societies and Social Simulation, 11(4), 12: https://www.jasss.org/11/4/12.html.
FEARON, J.D. and Laitin, D.A. (2003). Ethnicity, Insurgency and Civil War. American Political Science Review, 97(1), 75-90. [doi:10.1017/S0003055403000534]
FINDLEY, M.G. and Young, J.K. (2007). Fighting Fire with Fire? How (Not) to Neutralize an Insurgency. Civil Wars, 9(4), 378-401. [doi:10.1080/13698240701699482]
GALULA, D. (2006). Counterinsurgency Warfare: Theory and Practice. Westport, CT: Praeger Security International. Originally published 1964.
Guide to the Analysis of Insurgency. (2012). Vol. Accessed online on February 7, 2015 Published by the US Government. Washington DC: CIA Publication.
HEADQUARTERS, Department of the Army, figUnited States Marine Corps (2006). Counterinsurgency: The U.S. Army/Marine Corps Field Manual. FM 3-24. MCWP 3-33.5. United States Marine Corps. Washington, DC.
HUMPHREYS, M. and Weinstein, J. (2008). Who Fights? The Determinants of Participation in Civil War. American Journal of Political Science, 52(2): 436-455. [doi:10.1111/j.1540-5907.2008.00322.x]
JOHNSEN, G.D. (2014). The Last Refuge: Yemen, al-Qaeda, and America’s War in Arabia. New York: W. W. Norton & Company, Inc.
JOHNSTON, P.B. and Sarbahi, A.K. (2016). The Impact of US Drone Strikes on Terrorism in Pakistan. International Studies Quarterly. 60 (2), 203-219. [doi:10.1093/isq/sqv004]
KALYVAS, S.N. (2006). The Logic of Violence in Civil War. Cambridge University Press. [doi:10.1017/CBO9780511818462]
KALYVAS, S.N. and Balcells, L. (2010). International System and Technologies of Rebellion: How the End of the Cold War Shaped Internal Conflict.' American Political Science Review, 104 (3), 425-429. [doi:10.1017/S0003055410000286]
KALYVAS, S.N. and Kocher, M.A. (2007). How "Free" Is Free Riding in Civil Wars? Violence, Insurgency, and the Collective Action Problem. World Politics, 59(2), 177-216. [doi:10.1353/wp.2007.0023]
KOCHER, M.A., Pepinsky, T.B. & Kalyvas, S.N. (2011). Aerial Bombing and Counterinsurgency in the Vietnam War. American Journal of Political Science, 55(2), 201-218. [doi:10.1111/j.1540-5907.2010.00498.x]
KRESS, M., and MacKay, N.J. (2014). Bits or Shots in Combat? The Generalized Deitchman Model of Guerrilla Warfare. Operations Research Letters, 42, 102-108. [doi:10.1016/j.orl.2013.08.004]
KRESS, M., and Szechtman, R. (2009). Why Defeating Insurgencies Is Hard: The Effect of Intelligence in Counterinsurgency Operations – A Best-Case Scenario. Operations Research, 57(3). 578-585. [doi:10.1287/opre.1090.0700]
LYALL, J. (2009). Does Indiscriminate Violence Incite Insurgent Attacks? Evidence from Chechnya. Journal of Conflict Resolution, 53(3), 331-362. [doi:10.1177/0022002708330881]
NAGL, J.A. (2002). Learning to Eat Soup with a Knife: Counterinsurgency Lessons from Malaya and Vietnam. Chicago: Chicago University Press.
OLSON, M. (1993). Dictatorship, Democracy, and Development. American Political Science Review, 87(3), 567-576. [doi:10.2307/2938736]
PETRAEUS, D.H. (2006). Learning Counterinsurgency: Observations from Soldiering in Iraq. Military Review, January-February: 2-12.
RINEHEART, J. (2010). Counterterrorism and Counterinsurgency. Perspectives on Terrorism, 4 (5).
ROSS, M. (2004). How Do Natural Resources Influence Civil War? Evidence from Thirteen Cases. International Organization, 58, 35-68. [doi:10.1017/S002081830458102X]
SEPP, K.I. (2005). Best Practices in Counterinsurgency. Military Review, May-June: 8–12.
SEXTON, R. (2016). Aid as a Tool against Insurgency: Evidence from Contested and Controlled Territory in Afghanistan. American Political Science Review, 110(4), 731-749. [doi:10.1017/S0003055416000356]
U.S. GOVERNMENT COUNTERINSURGENCY GUIDE. (2009). Bureau of Political-Military Affairs, U.S. Department of State.
WEIDMANN, N.B. and Salehyan, I. (2013). Violence and Ethnic Segregation: A Computational Model Applied to Baghdad. International Studies Quarterly, 57(1), 52-64. [doi:10.1111/isqu.12059]
