Ian Lustick (2002)
PS-I: A User-Friendly Agent-Based Modeling Platform for Testing Theories of Political Identity and Political Stability
Journal of Artificial Societies and Social Simulation
vol. 5, no. 3
To cite articles published in the Journal of Artificial Societies and Social Simulation, please reference the above information and include paragraph numbers if necessary
<https://www.jasss.org/5/3/7.html>
Received: 26-May-2002 Accepted: 14-Jun-2002 Published: 30-Jun-2002
 Abstract
Abstract
|
| Figure 1. |

|
| Figure 2. |
 |
|
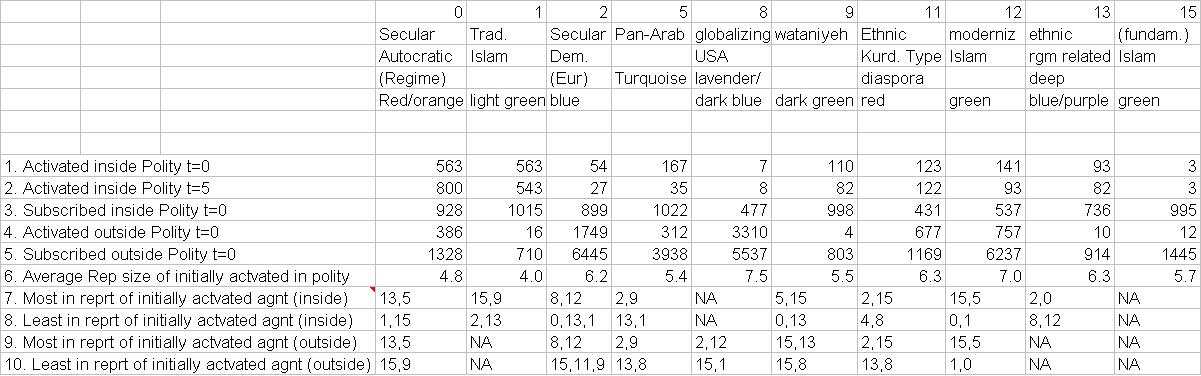
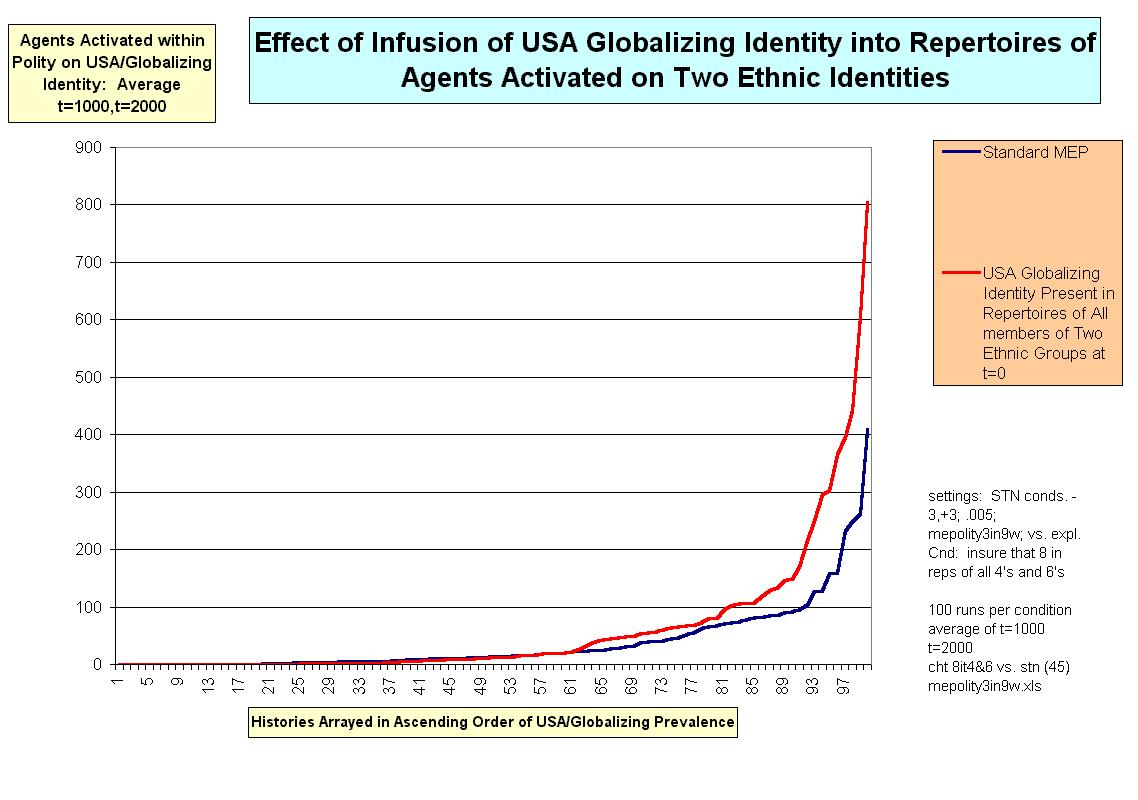
Figure 3. Guide to Salient Identities Notes on Abbreviations: reprt = repertoire Agnt = agent Rep = repertoire Trad = traditional Rgm = Regime NA = Not enough in category to warrant the measurement |
|
|
| Figure 4. |
|
|
| Figure 5. |
| A note on questions of time: To relate findings from these experiments to the real world it is necessary to make some sort of judgment regarding the time frame involved. How long should one time step be imagined to be in the life of Middle East polity and of the agents within it? To what periods of real time should we imagine t=1000 or t=2000 correspond? There is no easy or firm answer to these questions, but some reasonable estimates can be made. One way to do so is to monitor the extremes of rapid change within the landscape and then match the number of time steps required for those changes to the number of months or years very unusually rapid change occurs in the real Middle East. Such estimates can be corroborated by considering how often people and groups usually adjust their identity commitments and then comparing that observation to the probabilities present in the landscape under standard or stable volatitlity settings. Using these techniques, a preliminary judgment can be made that 1000 time steps of MEP is equivalent to somewhere in the neighborhood of fifteen years; with every time step therefore estimated to represent approximately five and a half days. |
|
| Figure 6. |
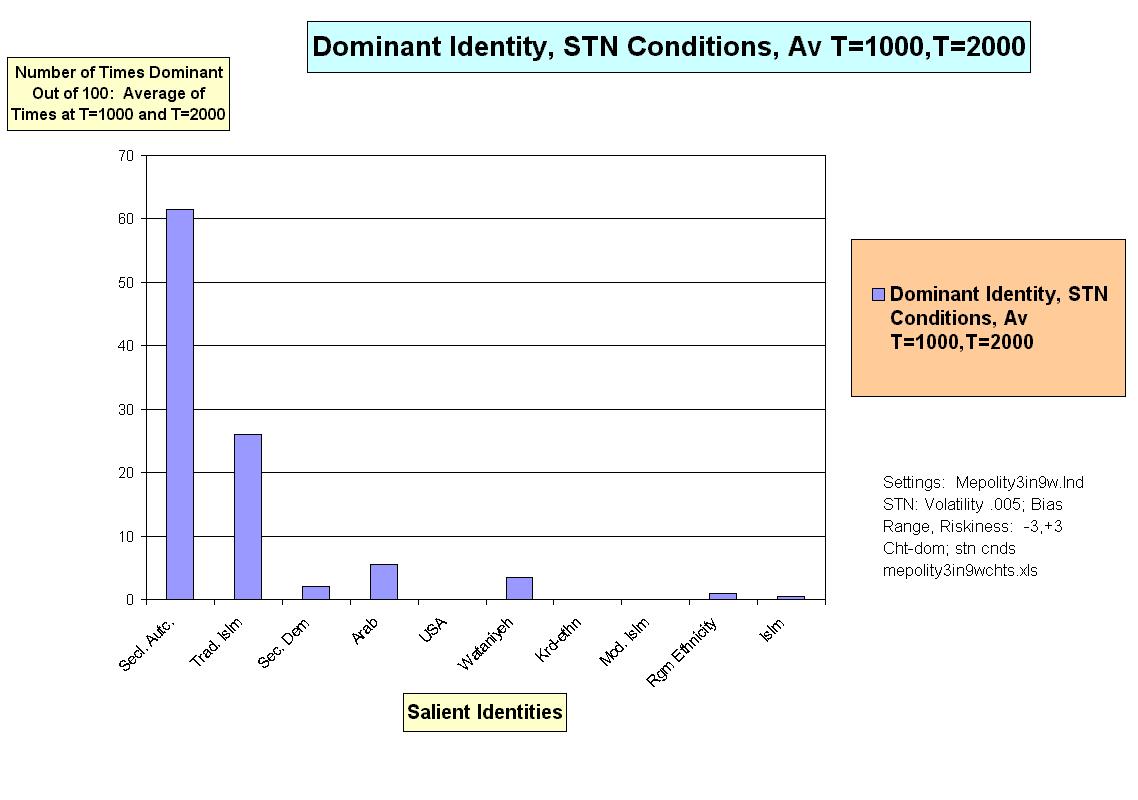 |
| Figure 7. |
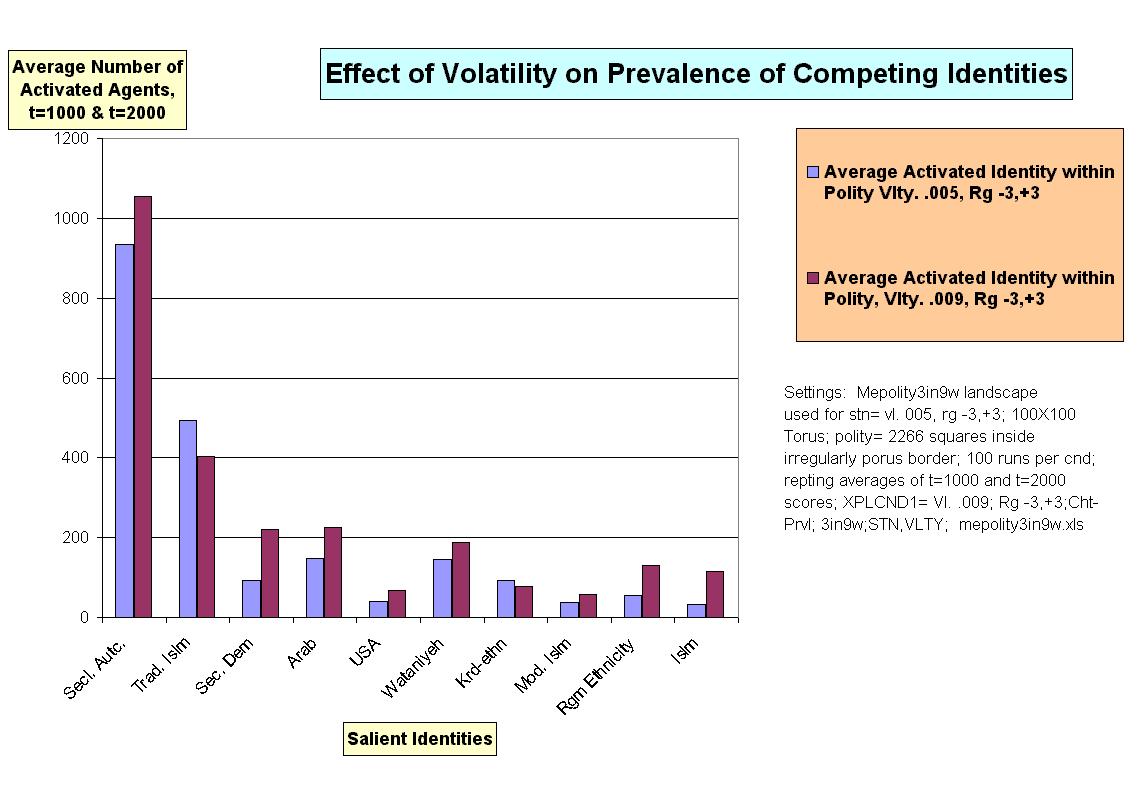
|
| Figure 8. |
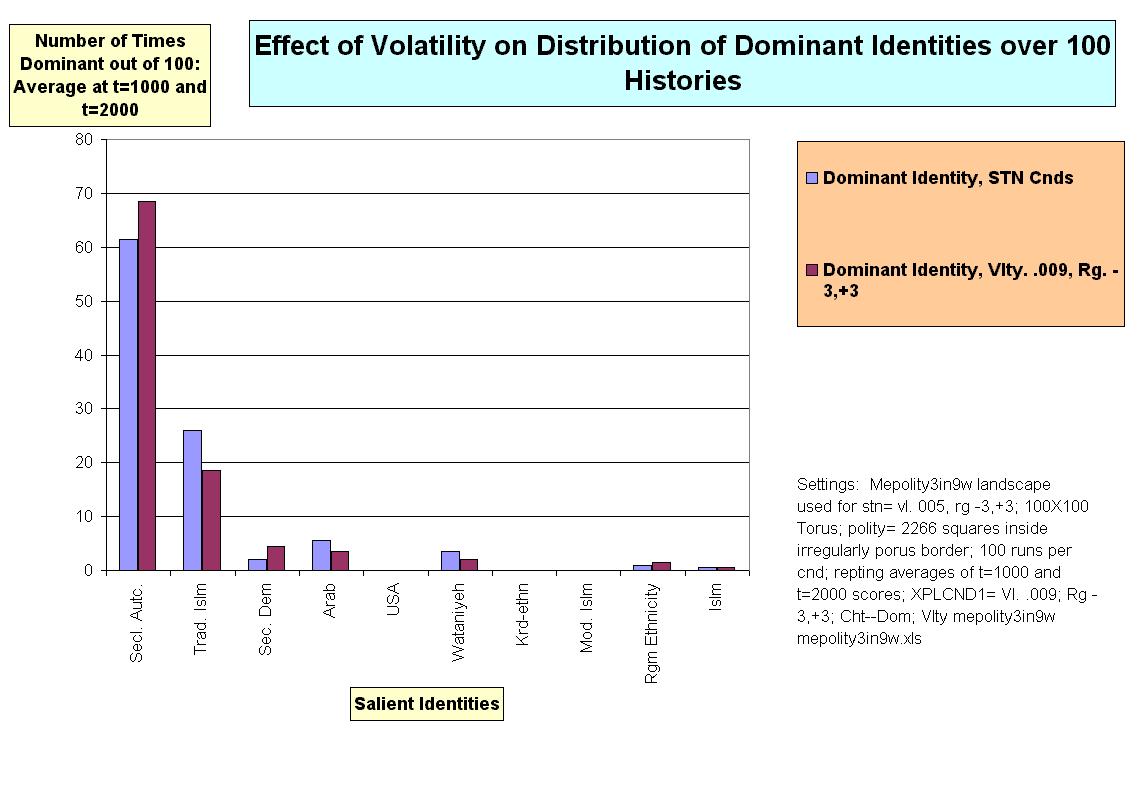
|
| Figure 9. |
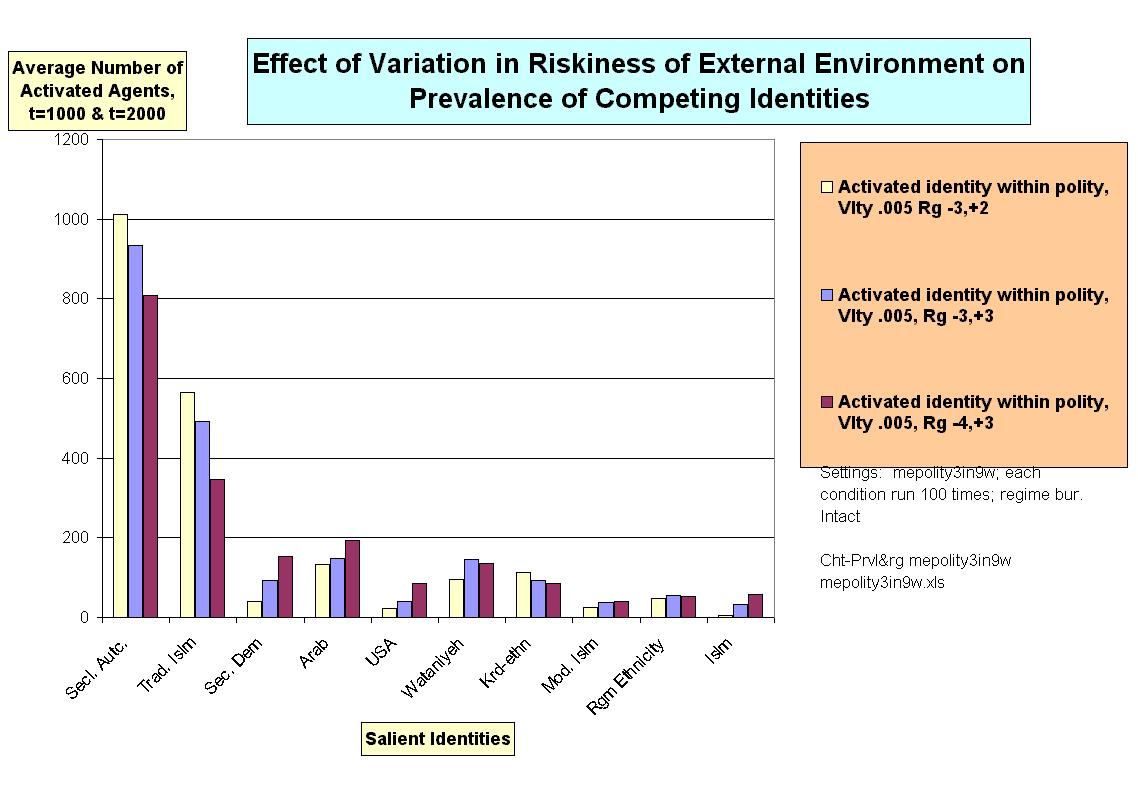
|
| Figure 10. |
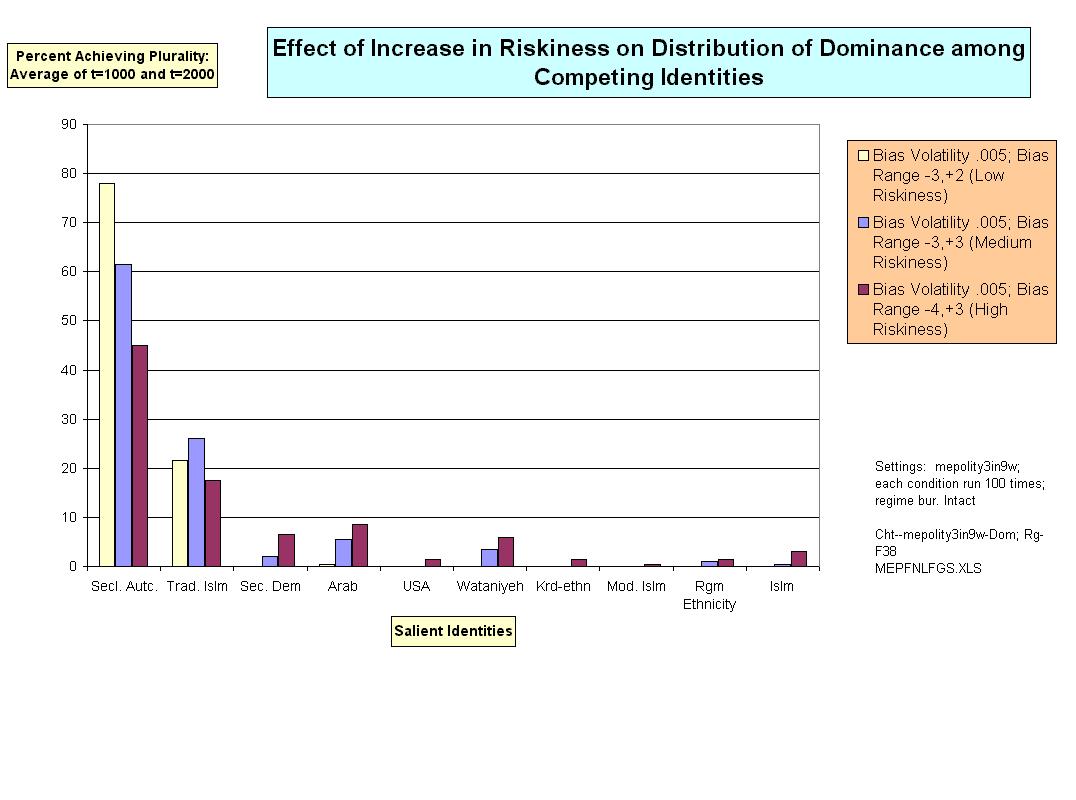 |
| Figure 11. |
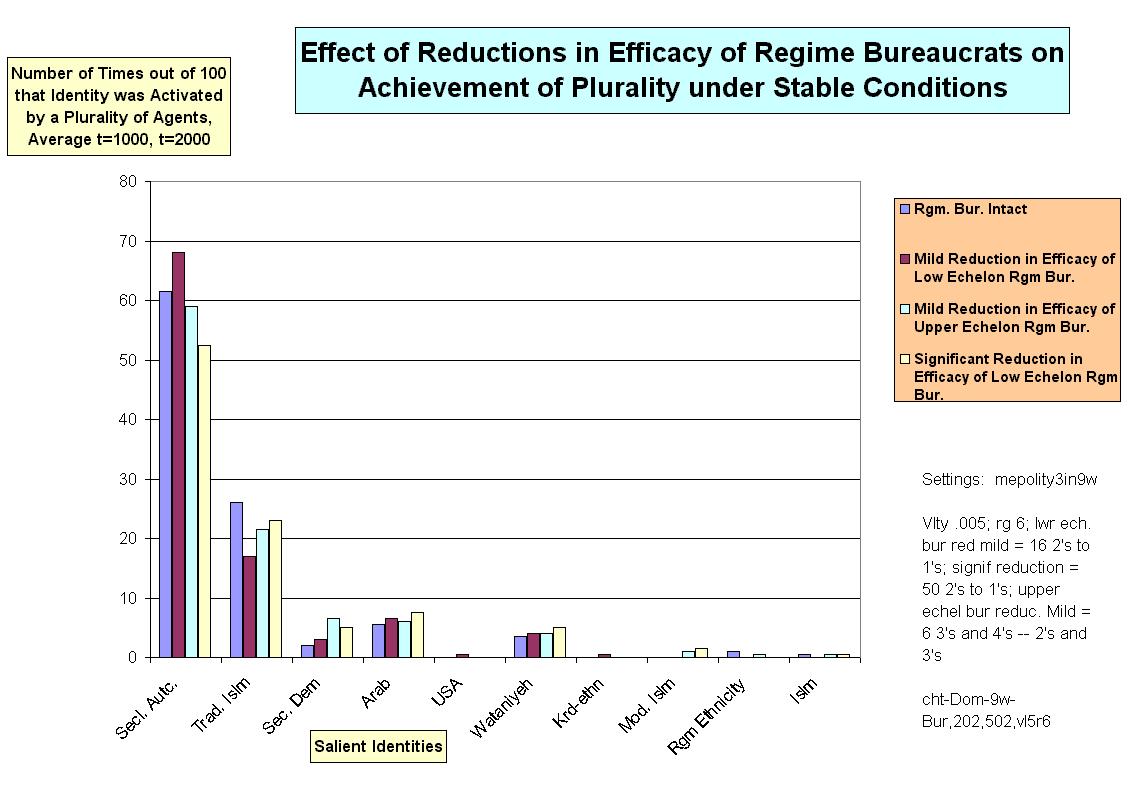
|
| Figure 12. |
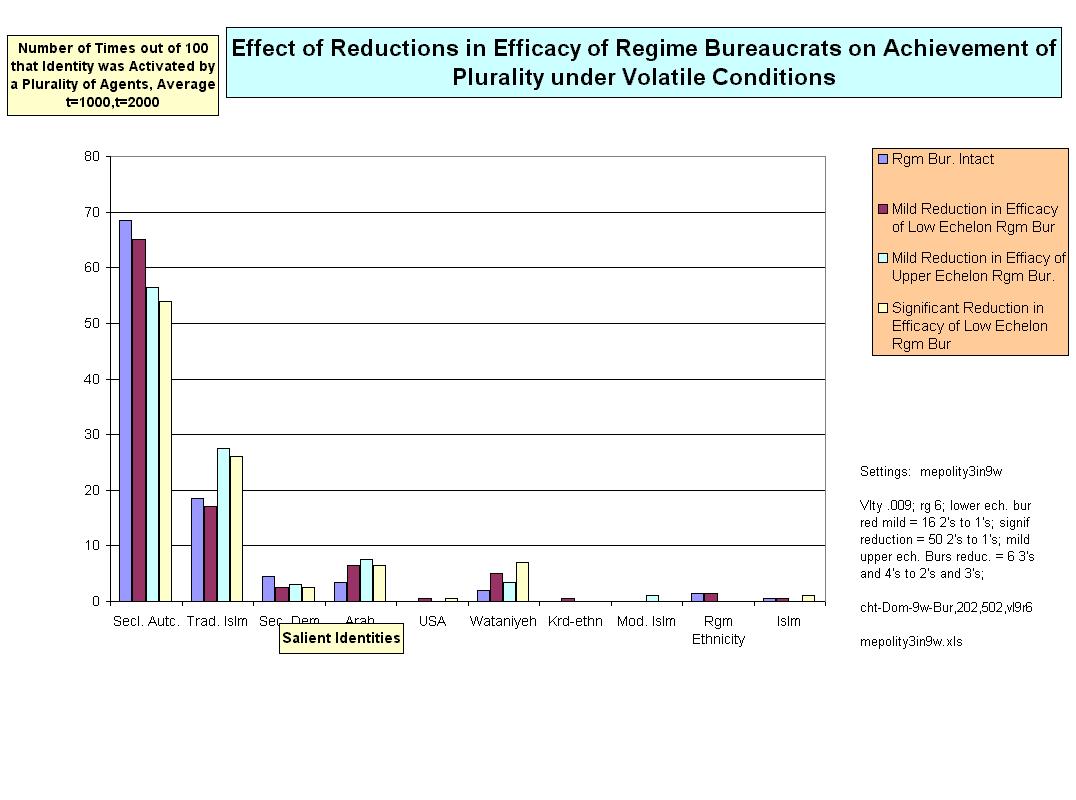 |
| Figure 13. |
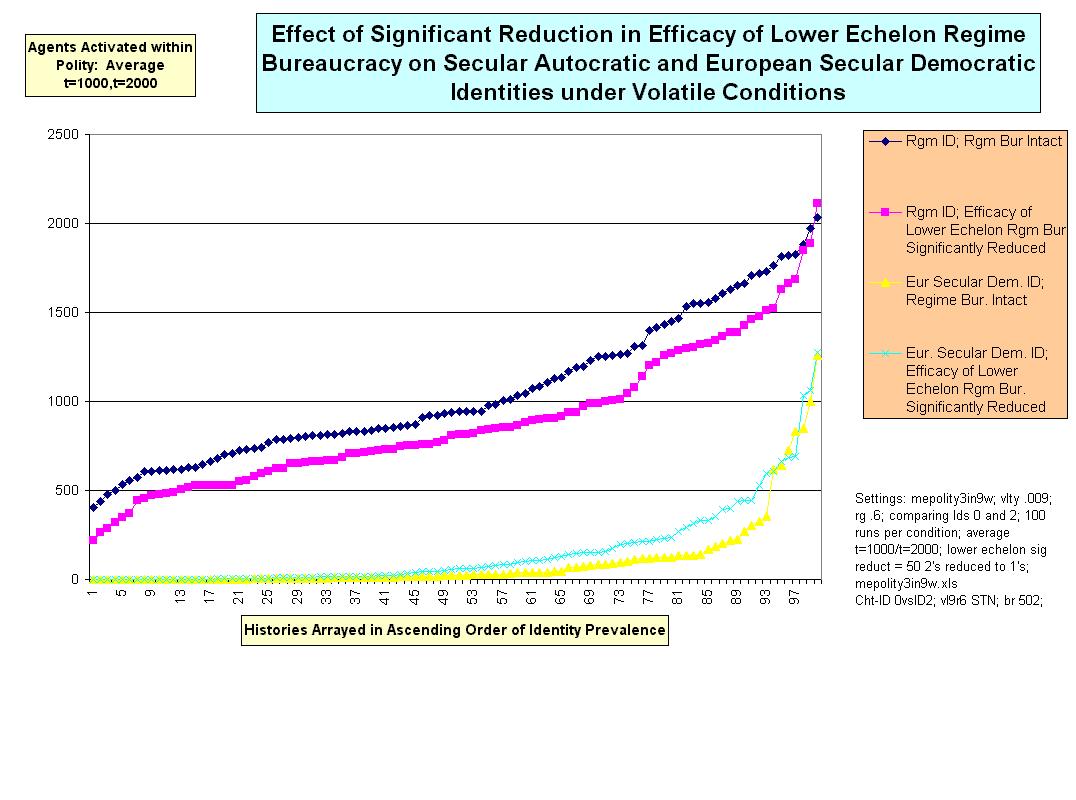 |
| Figure 14. |
 |
| Figure 15. |
 |
| Figure 1 |
 |
| Figure 2 |
 |
| Figure ? |
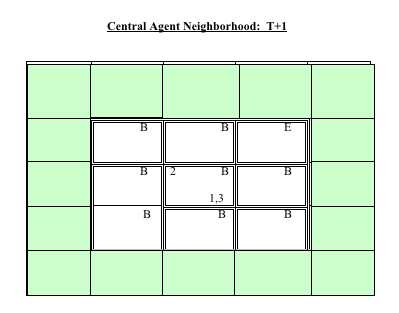 |
| Figure 4 |
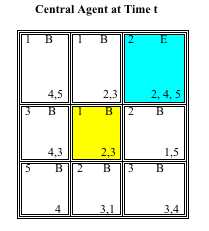
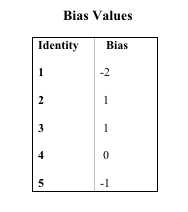
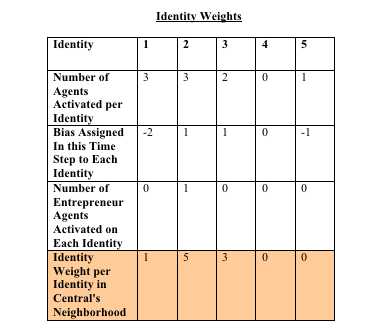
2 See the Appendix for a step-by-step illustration of how constructivist identity theory is operationalized for an exemplar agent through two time steps.
3 That is, if all other conditions are met, an agent is eligible for transforming into a border agent if and only if no more than 20% of the agents activated on its activated identity have the dominant identity in their repertoire of identities.
4 Each run of the simulation can be seen as a "future" by looking forward from the point of view of the polity at time zero (t=0) or as a history by looking backward from the point of view of any time step after t=0.
5 In the experiments reported here with MEP, biases assigned to identities all start out at 0. Although it depends on chance and the volatility setting in use for any particular run, few if any biases change from 0 within the first five time steps. But adjustments of agents to one another locally take place even in the absence of any external signals about the advantages or disadvantages of activating on different identities. These adjustments are very similar in every run of the template and most of them have occurred by t=5. So a snapshot of MEP at t=5 is actually a more accurate representation of its effective starting point than a snapshot at t=0.
6 The screenshot appears somewhat different from previous screenshots, and displays much more information about the landscape, because a customized version of PS-I, rather than the ABIR program itself, was used to prepare it. As noted above, PS-I is a tool-kit or platform for the production of an unlimited number of variants of the original ABIR model. PS-I 3.0 in its advanced but still "pre-release" form is available for downloading at http://ps-i.sourceforge.net/. Concerning ABIR and PS-I see http://www.psych.upenn.edu/sacsec/abir/.
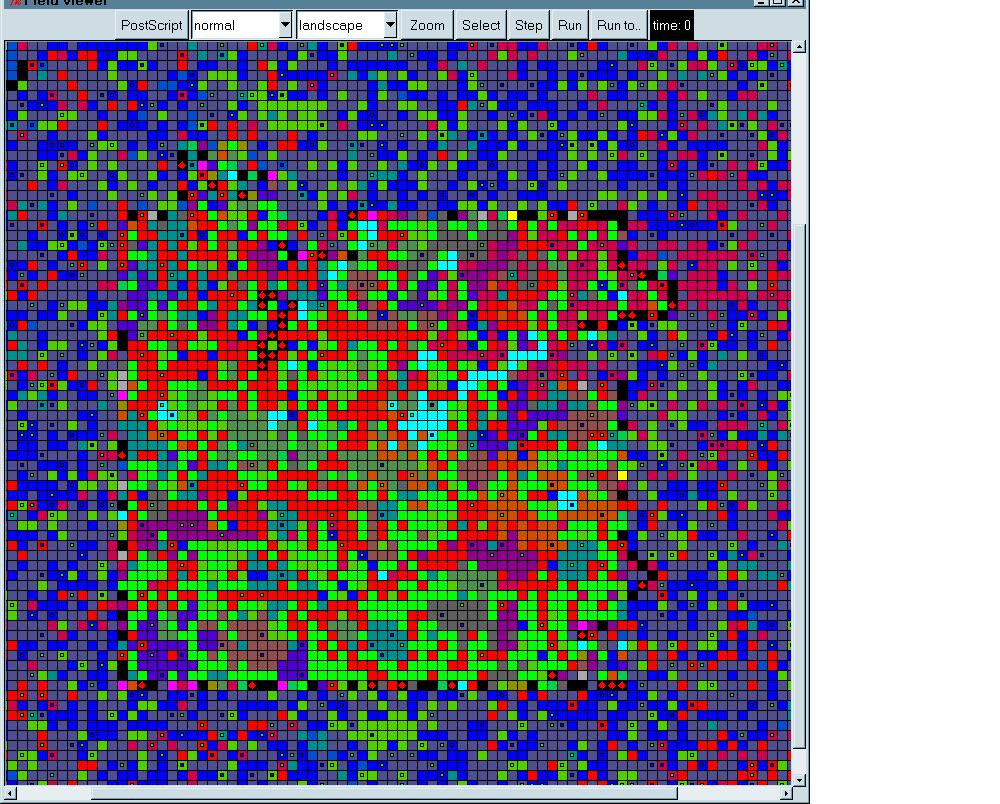
7 Moving the cursor over any particular agent in an ABIR landscape reveals the identities in its repertoire and its influence level, along with, of course, its activated identity.
8 NA means that the number was too small to make the measurement meaningful. For details on how constructivist principles were used to guide production of a landscape in which identities would emerge as relational properties of interactions among agents, rather than as hard-coded "primordial" traits, see http://www.duke.edu/web/licep/4/lustick/pp. 4-7.
9 There is one "leader" (occupying the square at coordinates 34,56) with an identity weight of 6.
10 The small shape bordered with black squares in the upper left hand corner of the landscape is a primitive rendition of Israel. The bright shade of blue (14) represents a Jewish/Israeli identity. The gray (19) represents a Palestinian identity, concentrated in the occupied territories and a part of Israel itself. This portion of the landscape has little if any discernible effect on MEP but its presence acts as one indicator of bizarre behavior in the model suggestive of something being seriously awry (e.g. takeover of MEP by the Israeli Jewish identity; or takeover of Israel by a patriarchal Islamic identity).
11 Because MEP is larger and contains many more different identities (20) than landscapes used in other experiments the standard or stable settings for range fluctuations is wider: -3,+3.
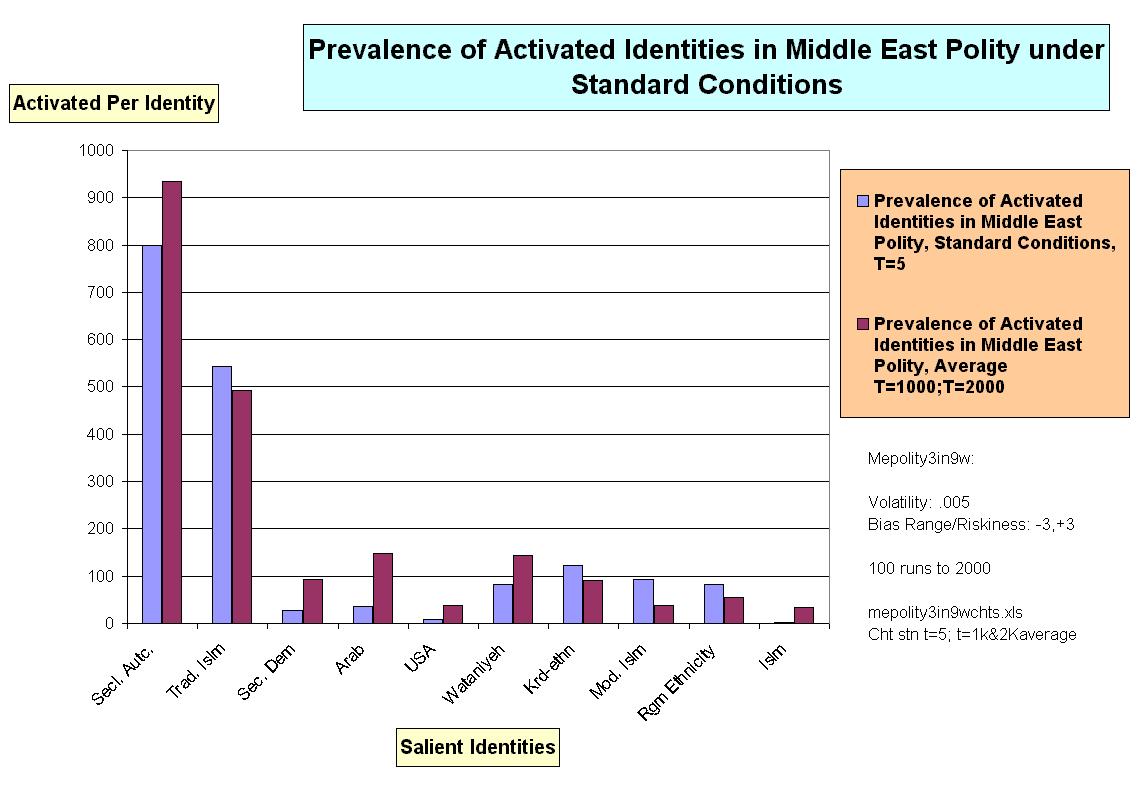
12 Data described by this and other Figures in this paper are available in Excel format from the author atilustick@sas.upenn.edu. The "salient" identities are the identities that together comprise an overwhelming majority of all activated identities in the landscape though they are only a subset of the twenty activatable identities present in MEP and its environment.
13 Statistical significance tests were done separately on the data at t=1000 and t=2000, but, for technical reasons, not on the averages between them-the data displayed in the Figures. Most of these relationships regarding the impact of riskiness on prevalence and dominance were significant at both t=1000 and t=2000 at the .01 or .05 level (2-tailed).
14 The effect of a proportionately larger reduction of upper regime bureaucratic efficacy was not tested, though the expectation must be of an even greater reduction in the rate of regime dominance.
15 Absent the addition of USA/globalizing identity to the repertoires of agents activated on the two target ethnic groups, that identity achieved a plurality not once out of 100 histories (t=2000, standard conditions). In the presence of this intervention, a USA/globalizing plurality was achieved once, but only once, out of 100 histories.
ARONOFF, Myron J. 1998. "The Politics of Collective Identity." Reviews in Anthropology, Vol. 27, no. 1: 71-85.
AXELROD, Robert. 1997. The Complexity of Cooperation: Agent-Based Models of Competition and Collaboration. Princeton: Princeton University Press.
AXTELL, R. L. 2000. "Why Agents? On the Varied Motivations for Agent Computing in the Social Sciences." In Macal, BENOIT, Kenneth. 2001. "Simulation Methodologies for Political Scientists," The Political Methodologist, Vol. 10, no. 1: 12-16.
BARKOW,J., L. Cosmides, and J. Tooby. 1992. (eds.), The Adapted Mind: Evolutionary Psychology and the Generation of Culture. New York: Oxford University Press.
BOURHIS,Richard Y., John C. Turner, and André Gagnon. 1997. "Interdependence, Social Identity and Discrimination." In Russell Spears, Penelope F. Oakes, Naomi Ellemers, and S. Alexander Haslam (eds.), The Social Psychology of Stereotyping and Group Life. Oxford: Blackwell Publishers: 273-95.
BOYD, Robert and Peter J. Richerson. 1985. Culture and the Evolutionary Process. Chicago: University of Chicago Press.
BREWER, Marilynn B. and Rupert J. Brown. 1998. "Intergroup Relations." In Daniel T. Gilbert, Susan T. Fiske, and Gardner Lindzey (eds.), The Handbook of Social Psychology, Vol. II. Boston: McGraw-Hill: 554-93.
BROWN,Michael, Owen Cote, Jr., Sean Lynn-Jones, and Steven Miller (eds). 2000. Rational Choice and Security Studies: Stephen Walt and His Critics. Cambridge, Mass.: MIT Press.
BRUBAKER, Rogers. 1996. Nationalism Reframed: Nationhood and the National Question in the New Europe. Cambridge: Cambridge University Press.
BYMAN, Daniel. 2000. "Forever Enemies? The Manipulation of Ethnic Identities to End Ethnic Wars," Security Studies, Vol. 9, no. 3: 149-190.
CALHOUN, Craig. 1995. Critical Social Theory: Culture, History and the Challenge of Difference. Oxford and Cambridge, MA: Basil Blackwell.
CAMPBELL, Donald T. 1975. "On the Conflicts Between Biological and Social Evolution and Between Psychology and Moral Tradition." American Psychologist. December:1103-23.
CASTI, John. 2000. "Would-Be Business Worlds." Complexity. Vol. 6, no. 2: 13-15.
CEDERMAN, Lars-Erik. 1997. Emergent Actors in World Politics: How States and Nations Develop and Dissolve. Princeton: Princeton University Press.
CEDERMAN, Lars-Erik. 2001. "Agent-Based Modeling in Political Science," The Political Methodologist, Vol. 10, no. 1: 16-22.
CHANDRA, Kanchan. 2001. "Introduction: Constructivist Findings and Their Non-Incorporation," APSA-CP: Newsletter of the Organized Section in Comparative Politics of the American Political Science Association. Vol.12, no. 1: 7-11.
COLLIER, Paul, and Anke Hoeffler. 2000. Greed and Grievance in Civil War. Washington, D.C.: World Bank.
CRITICAL REVIEW. 1995. Special Issue on Rational Choice Theory, Vol. 9, no. 1-2.
DANSPECKGRUBER, Wolfgang. 1997. (ed.), Self-Determination and Self-Administration. London: Lynne Rienner Publishers, 1997.
DAWKINS, Richard. 1989. The Selfish Gene. Oxford: Oxford University Press.
DENNETT, Daniel C. 1995. Darwin's Dangerous Idea. New York: Simon and Schuster.
DUGDALE, Julie. N.d. "An Evaluation of Seven Software Simulation Tools for Use in the Social Sciences."http://www.irit.fr/COSI/training/evaluationoftools/Evaluation-Of-Siumulation-Tools.htm.
ECOLOGICAL Society of America. 1999. "Computational Ecology," NewSourceNEWS, 65.
EIDELSON, Roy J. and Ian S. Lustick. Forthcoming 2002. "National Identity Repertoires, Territory, and Globalization." In Mabel Berezin and Martin Schain (eds), Remapping Europe: Territory and Politics. Baltimore: Johns Hopkins Press.
ELEY, Geoff and Ronald Grigor Suny. 1996. "Introduction: From the Moment of Social History to the Work of Cultural Representation," in Eley, Geoff and Ronald Grigor Suny (eds.), Becoming National: A Reader. New York: Oxford University Press: 3-37.
EPSTEIN, Joshua M. 1999. "Agent-Based Computational Models and Generative Social Science," Complexity, Vol. 4, no. 5: 41-60
CHAFETZ, Glenn, Michael Spirtas, Benjamin Frankel. 1999. "Introduction: Tracing the Influence of Identity on Foreign Policy." In Glenn Chafetz, Michael Spirtas, Benjamin Frankel (eds.),The Origins of National Interests. London: Frank Cass: vii-xxii.
GREEN, Donald P. and Ian Shapiro. 1996. Pathologies of Rational Choice Theory: Critique of Applications in Political Science. New Haven: Yale University Press.
GROSS J., Louis J. 1997. Parallel Processing for Individual-Based Ecological Models. http://ecology.tiem.utk.edu/~gross/nsfreport.797.txt
HANNUM, Hurst. 1990. Autonomy, Sovereignty, and Self-Determination: The Accommodation of Conflicting Rights. Philadelphia: University of Pennsylvania Press.
HOLLAND, John H. 1998. Emergence: From Chaos to Order. Reading, MA: Helix Books.
HUGHES, Barry B. 1999. International Futures: Choices in the Face of Uncertainty. Boulder: Westview Press.
HUNT, Allen G. 2001. "El-Nino: Dynamics, Its Role in Climate Change, and Its Effects on Climate Variability: The Limits of Predictability," Complexity, Vol. 6, no. 2: 16-32.
JOHNSON, Paul E. 1998. "Rational Actors Versus Adaptive Agents: Social Science Implications." Paper presented at the annual meeting of the American Political Science Association, Boston.
JOHNSON, Paul E. 1999. "Simulation Modeling in Political Science," American Behavioral Scientist, Vol. 24, no. 10: 1509-30.
KAPLAN, Robert D. 1993. Balkan Ghosts: A Journey Through History. New York: St. Martin's Press.
KING, Gary, and Lanche Zeng. 2001. "Improving Forecasts of State Failure." World Politics, Vol. 53, no. 4: 623-58.
KOWERT, Paul A. 1999. "National Identity: Inside and Out," in Glenn Chafetz, Michael Spirtas, Benjamin Frankel, eds, The Origins of National Interests. London: Frank Cass. 1-34.
LAITIN, David D. 1986. Hegemony and Culture. Chicago: University of Chicago Press.
LAITIN, David D. 1988. Identities in Formation. Ithaca: Cornell University.
LAITIN, David, and Daniel Posner. 2001. "The Implications of Constructivism for Constructing Ethnic Fractionalization Indices." APSA-CP: Newsletter of the Organized Section in Comparative Politics of the American Political Science Association. Vol.12, no. 1: 13-17.
LEVITAN, Bennett. 1997. "Models and Search Strategies for Applied Molecular Evolution." In M.R. Pavia, W.H. Moos, A.D. Ellington, and B.K.Kay (eds.), Annual Reports in Combinatorial Chemistry and Molecular Diversity. Netherlands: ESCOM Publishers.
LUSTICK, Ian S. 1993. Unsettled States, Disputed Lands: Britain and Ireland, France and Algeria, Israel, and the West Bank/Gaza. Ithaca: Cornell University Press.
LUSTICK, Ian S. 2000. "Globalization and the Resurgence of Identity Politics." Paper presented to LiCEP workshop, Duke University, April 22. http://www.duke.edu/web/licep/1/lustick/Lustickmemo.doc.
LUSTICK, Ian S. 2001. "Agent_based Modeling and Constructivist Identity Theory," APSA-CP: Newsletter of the Organized Section in Comparative Politics of the American Political Science Association. Vol.12, no. 1: 22-25.
LUSTICK, Ian S. and Dan Miodownik. 2000. "Deliberative Democracy and Public Discourse: The Agent-Based Argument Repertoire Model," Complexity. Vol. 5, no. 4: 13-30.
LUSTICK, Ian S. and Dan Miodownik. Forthcoming, 2002. ""The Institutionalization of Identity: Micro Adaptation, Macro Effects, and Collective Consequences." Studies in Comparative International Development.
LUSTICK, Ian S., Dan Miodownik, and Stacey Philbrick. 2000. "The Institutionalization of Identity." Paper presented to LiCEP workshop, University of Pennsylvania, October. http://www.duke.edu/web/licep/2/lustick/lustick.
LUSTICK, Ian, Dan Miodownik, and A. Maurits van der Veen. 2001. "Studying Performance and Learning with ABIR: A Research Note," In David Sallach and Thomas Wolsko (eds) Proceedings of the Workshop on Simulation of Social Agents: Architectures and Institutions, October 6-7, 2000. Argonne, IL: Argonne National Laboratory.
MCGARRY, John and Brendan O'Leary (eds.), 1993. The Politics of Ethnic Conflict Regulation. London: Routledge.
MONTVILLE, Joseph. 1987. Conflict and Peacemaking in Multiethnic Societies. Lexington, MA: Lexington Books.
NAGEL, Joane. 1994. "Constructing Ethnicity: Creating and Recreating Ethnic Identity and Culture." Social Problems, Vol. 41, no. 1: 152-176.
O'LEARY,Brendan, Ian S. Lustick, and Thomas Callaghy, eds. Right-sizing the State: The Politics of Moving Borders. Oxford: Oxford University Press, 2001.
PAGE, Scott. 1999. "Computational Models from A to Z," Complexity, Vol. 5, no. 1: 35-41.
PANEL on Modeling and Simulation of the Committee on Technology for Future Naval Forces, Naval Studies Board, National Research Council. George F. Carrier (Chair). 1997. Technology for the United States Navy and Marine Corps, 2000-2035, Vol. 9. Washington, D.C.: National Academy Press.
PERELSON, Alan S. and Frederik W. Wiegel, 1999. "Some Design Principles for Immune System Recognition," Complexity, Vol. 4, no. 5: 29-37.
SAFRAN, William and Ramon Maiz. 2000. (eds.), Identity and Territorial Autonomy in Plural Societies. London: Frank Cass.
SAMBANIS, Nicholas. 2000. "Partition as a Solution to Ethnic War: An Empirical Critique of the Theoretical Literature," World Politics. V. 52, no. 4: 437-83. Data available at: http://www.worldbank.org/research/conflict/papers/partition.htm.
SIMON, Herbert A. 1997. Administrative Behavior. New York: The Free Press, Fourth Edition.
TESFATSION, Leigh. 2001. "Software for Agent-Based Computational Economics (ACE) and Complex Adaptive Systems." http://www.econ.iastate.edu/tesfatsi/acecode.htm
THOMPSON, James. D. 1967. Organizations in Action. New York: McGraw-Hill.
VAN DER VEEN, A. Maurits, and Ian S. Lustick. 2001. "The Emergence of a European Identity: An Agent-Based Modeling Approach." Paper presented at the conference on Ideas, Discourse and European Integration at the European Union Center, Harvard University, May.
VAN DER VEEN, A. Maurits, Ian S. Lustick, and Dan Miodownik. 2001. "Studying Performance and Learning with ABIR: The Effects of Knowledge, Mobilizing Agents, and Predictability," Social Science Computer Review. Vol. 19, No. 3: 263-280.
Van Evera, Stephen. 2001. "Primordialism Lives!" APSA-CP: Newsletter of the Organized Section in Comparative Politics of the American Political Science Association. Vol.12, no. 1: 20-22.
VERDERY, Katherine. 1991. National Ideology Under Socialism Identity and Cultural Politics in Ceausescu's Romania. Berkeley: University of California Press.
WALDROP, M. Mitchell. 1992. Complexity: The Emerging Science at the Edge of Order and Chaos. New York: Touchstone.
ZEBULUM, R., Pacheco, M.A., Vellasco, M. (1998) "Comparison of different evolutionary methodologies applied to electronic filter design." In Proceedings of the IEEE International Conference on Evolutionary Computation (ICEC98), Anchorage, Alaska: 434-439.
Return to Contents of this issue
© Copyright Journal of Artificial Societies and Social Simulation, [2002]